The difference between zkRollup and Validium: What scenarios are they suitable for?
Foreword:
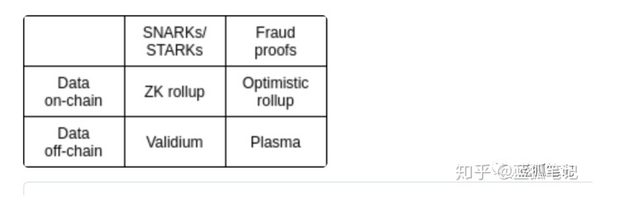
zkRollup and Validium are both scalable solutions of Ethereum Layer 2. Its transaction validity is achieved through the use of zero-knowledge proofs, but the data availability of one is kept on the chain and the other is kept off the chain. This seemingly small difference leads to a big difference in the security level of the two assets.
Of course, this also leads to a big difference in throughput between the two. Validium may be more suitable for relatively high-frequency applications (such as game dApps) that do not require so much trust, while zkRollup is more suitable for scenarios such as payment and exchanges with higher security requirements. The author of this article is Alex Gluchowski, translated by "SIEN" from the "Blue Fox Notes" community.
DeversiFi recently launched a new version of the exchange, which is supported by the StarkEx trading engine. This is an amazing technical achievement that has increased the level of security users expect from cryptocurrency exchanges. This also marks a historic turning point: this is the first ever to apply STARK (a concise zero-knowledge proof without trust setting) in a production system. From the background, StarkEx is Validium: it is a Layer 2 scalability solution in which all transaction validity is enforced using zero-knowledge proofs, while data availability remains off-chain. This prevents funds in Validium from being stolen, because every transfer of value from a specific user account must be authorized by the user.
(Vitalik retweeted Eli Ben-Sasson's summary of the difference between the two)
Validium's mechanism is very similar to zkRollup. The main difference is that the data availability in zkRollup is on-chain, while Validium remains off-chain. This allows Validium to achieve higher throughput, but this comes at a price: the operator of StarkEx Validium can freeze users’ funds "Those who can destroy things control things."-Frank Herbert, Dune does not have the data availability of zkRollup It is guaranteed that the operator of Validium (or more precisely, the manager of data availability), can deny any user the right to transfer funds.
This is how it works: Operators make minor changes to Merkel's status without revealing the changes to the user. Without this information, users cannot create Merkel proof of ownership for their account.
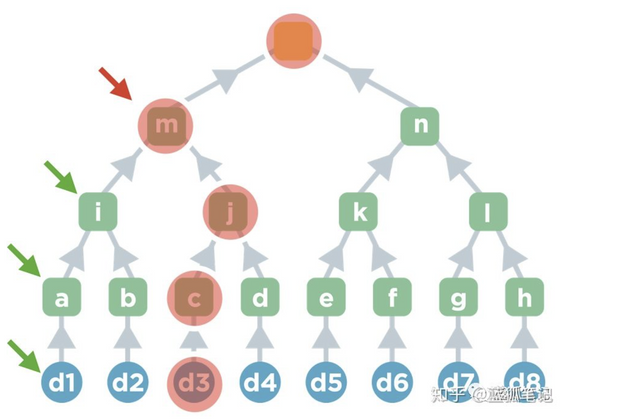
As shown in the figure: if the operator changes the account d3, the owner of the account d1 will lose the information of the node m required in the certificate, which needs to be used to prove the ownership of the account.
Is there a way to prevent data retention attacks in Validium? Since the Plasma concept was proposed in 2016, this issue has been discussed by everyone. At the same time, zkRollup was born from the results of this research. Non-rollup attempts to ensure data availability without trust, which will result in the loss of most of Validium's competitive advantages.
Although it cannot completely solve the problem, StarkEx has alleviated the situation by introducing a licensed data availability committee (DAC).
The DAC must confirm that it has received the data by signing every update of the status through a quorum of its committee members. In StarkEx, the DAC consists of 8 participants (adding too many members will not be conducive to the activity of the system). They are all well-known and prestigious organizations in established legal jurisdictions. For them, it is almost impossible to try to abuse their power. This is the logic of its construction.
Paradoxically, the well-known, prestigious, and powerful jurisdictions of countries are what makes them vulnerable. One possible troublesome situation is that the operator requires the implementation of KYC/AML regulations and is obliged to freeze (possibly forever) all funds in accounts with transaction records exceeding $10,000.
As our research deepens, StarkEx has implemented a "validator contract upgrade" mechanism, which allows operators to immediately add new items to the validator contract on the chain. It cannot invalidate any old logic, for example, you cannot delete user signature checks. Instead, it allows other constraints to be added (as far as Solidity is concerned, you can think of constraints as require() statements). This is a good security feature: if any missing constraint is found in the logic of StarkEx’s STARK circuit, it can be quickly fixed without introducing new vulnerabilities. However, this feature can be used as a hidden review backdoor. In short, StarkEx operators can always deploy extensions to the contract logic, so that there is the possibility of introducing blacklist extensions without warning users in advance. This is not fully understood from its documentation, but it seems that implementing the new rules does not require the approval of the DAC (Blue Fox Notes: Data Availability Committee). If you think of StarkEX as a completely decentralized trading protocol, then it doesn't make much sense.
Imagine if Vitalik Buterin had a switch that could instantly freeze any Ethereum account, what would be the result? In addition, if you view StarkEX as an enhancement of the security features of a crypto exchange (which its creator should have done), then it makes sense. The operator of StarkEX Validium is able to confiscate users' funds and let us expand the thought experiment. Regardless of the hypothetical reasons (probably due to reasons beyond the control of the operator), many users' assets have been frozen. So, can the user's funds in StarkEx also be confiscated? In fact, it is possible. Like many other encryption projects, StarkEx has implemented the latest upgrade mechanism.
Before deploying the new version, users will be notified 28 days in advance, and anyone can withdraw and exit as long as they don’t like it. Except for those whose funds are frozen. New logic can be deployed on the contract, so that after the grace period ends, the frozen funds can be transferred to the designated party for custody through the new logic. Unfortunately, the affected users have nothing to do with this. There are also reasonable concerns that the upgrade reminder cycle may not be enough to quit every user who disagrees with the change (the so-called "mass quit" scenario). However, this problem is a general contract upgrade problem, not a problem unique to Validium. Justin Drake described the cryptoeconomic attack on Validium. In the follow-up discussion, Justin Drake pointed out that data availability may lead to unexpected attack vectors: If the signature key of the quorum of the DAC (Data Availability Committee) is compromised To damage (considering that these keys remain online, which makes it difficult to guarantee complete security), an attacker can convert Validium to a state known only to them, thereby freezing all assets, and then demanding a ransom to unlock the assets. In theory, the contract upgrade mechanism can mitigate such attacks.
Validium operators can initiate the deployment of the new version and restore the status to the latest known version after the 28-day upgrade notification period. This will be a month of capital lock-in, which of course has a great cost, but if the DAC refuses to negotiate, the attacker will not get a penny. However, it turns out that there is a way for the attacker to force the operator to decide between losing all and allowing the attacker to double spend. This can be illustrated by the following example: Imagine that you can hack the ATM in a certain way to erase the entire bank database after the withdrawal is completed. You can only withdraw money from your account, but when the database disappears, the details of the operation will also be lost. Bank employees can complete the complex database recovery process within a month. However, since they cannot know who withdrew the money, they will also restore the balance of the money you have withdrawn by returning to the last checkpoint. (Blue Fox note: that is, the attacker can achieve a double-spending attack by operating his own account) Of course, this double-spending attack will be limited to the attacker’s account balance. However, it is not difficult to construct trustless contracts and borrow the necessary assets from anonymous whales. Data availability in zkRollup protects users' assets from seizure, censorship and hacker attacks, but its throughput is reduced. For zkrollup users, the status of rollup is available as long as there is an Ethereum full node online. It works like this: For each zkRollup block, the information required to reconstruct the state change must be submitted as the call data of the Ethereum transaction, otherwise the zkRollup smart contract will refuse to perform the state transition.
State changes on zkRollups will result in a lower gas cost per transaction, which increases linearly with the number of transactions. With the Merkle tree data at hand, the censored user can always directly request their funds from the zkRollup contract on the mainnet. All they need to do is provide proof of Merkle ownership on their account. Therefore, the availability of data on the chain can ensure that no one (including zkRollup operators) can freeze or capture user funds. On-chain storage of data availability leads to throughput limitations. zkRollup has an upper limit of 2000tps on Ethereum today, while StarkEx Validium claims to be able to reach 9000tps. This difference may result in determining the choice of the two technologies in terms of application areas and use cases. For example, zkRollup is very suitable for the expansion of decentralized encrypted payments (VISA's global average tps is 2000), as well as those non-tamperable smart contracts that have strict requirements for no trust; and for Validium, it may be more suitable for traditional High-frequency trading or a good game with a lower trust assumption. Conclusion It has been proved that zkRollups and Validium (StarkEX) work relatively similarly, but the main difference lies in whether the data is available on-chain or off-chain. This is essential to understand them and in what scenarios to use them. This difference also means that although zkRollup is a completely license-free decentralized extension protocol, Validium shows more properties of the managed PoA system (both throughput and risk characteristics), although its security has been extremely high.
Greatly improved. Both technological developments are reducing the need for trust and providing users with more control over their assets. They are both in the direction of empowering individuals. In order to make progress, we always need to make trade-offs. However, in the encryption community, there is a growing consensus that the technology has passed the "don't be evil" stage and has entered the "can't be evil" stage. We can achieve our goals through self-hosting, censorship resistance, privacy, and elimination of single points of failure. These ideas constitute the basic value of the system we are fighting for.