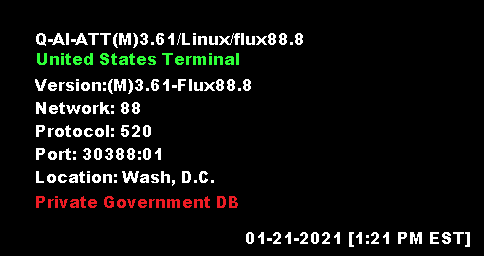
Hacking Network 88 Server : The Hyper Quantum AI AT-T Machine

-START
Find 88 Network 3 Node Flare 88
Thank you for your inquiry!
We will be in touch soon....
Searching......
Network Flare 88 Found.
Quantum Visualization System Ready.
/3D/4D/5D Gates Opening....
Joining Network Flow Segment Stack Blocks...
Accessing Nodes 1-8........
1 Node 2 Nodes
3 Nodes 4 Nodes
5 Nodes 6 Nodes
7 Nodes 8 Nodes

Hyper Q AI ATT (M) Server Error 88
Show Error 88
Showing Catalyst Cisco 3 Hyper Q AI ATT (M) Server Router—
Layer hierarchical Model, 42-45, 43
Administrative Access Layer - 45 Core Layer, 44 Distribution Layer
44-45 CiscoFusion, 161 Class A NETWORK, 88 89 90.
CLASS A CORRUPT RED LIGHT GREEN LIGHTOVERRIDE
/EIGRP/Dev_Training_GuidePg667.txt
open Dev_Training_Guide_Pg667.txt
Page 667

Enhanced Interior Gateway Routing Protocol - EIGRP does not operate using the Transmission Control Protocol (TCP) or the User Datagram Protocol (UDP). This means that EIGRP does not use a port number to identify traffic. Rather, EIGRP is designed to work on top of layer 3 (i.e. the IP protocol). Since EIGRP does not use TCP for communication, it implements Cisco's Reliable Transport Protocol (RTP) to ensure that EIGRP router updates are delivered to all neighbors completely. The reliable transport protocol also contains other mechanisms to maximize efficiency and support multicasting. EIGRP 224.0.0.10 multicast address and protocol number 88.
open 224.0.0.10:88
For metric calculations, EIGRP metric is a 32-bit number. These are big, ugly numbers that are based on a Ciscoproprietary Diffusing Update Algorithm (DUAL). By default, EIGRP uses "K-values" Bandwidth (BW) and Delay (DLY). If you want to, you can also factor in Reliability (REL) and Load, though these are not in use with "out of the box" EIGRP configurations. MTU is also exchanged but not used for metric calculations. So, in order for the EIGRP neighbor relationship to be formed exchanging routes, the K-values must match in the hello messages. Configuration In order to configure EIGRP you must be in the router configuration mode. Then, just as with Access Control Lists or OSPF network configurations, you can use the wildcard mask to specify the network/host addresses you want to start EIGRP. If you don't key in the wildcard mask entries, the system defaults to classful assumption.
You could use different subnet masks at different places in your network, based on your host requirements or other business reasons. This means there is a VLSM (Variable Length Subnet Mask) support in EIGRP. EIGRP allows you implement unequal load sharing alongside equal load sharing, if you have parallel links between sites.
EIGRP allows you to specify the different times of the day when different passwords will be effective. (I hope your time servers are keeping things in sync so you can take advantage of this great feature.) EIGRP uses IP protocol 88, so if you are the firewall person or the ACL person, you want to ensure that the protocol number 88 is allowed. Remember, EIGRP rides on IP, not on TCP or UDP like some other protocols do (RIP, for example, rides on UDP port 520). EIGRP allows you to use MD5 authentication between peers. This could be very powerful if you are afraid that someone could be sniffing the network and stealing your routes. With EIGRP authentication, you can validate each update and ensure that you are talking to the correct EIGRP neighbor since they share the same password. open protocol + +
open protocol 88 & 520
88
"It's better than the other distance vector protocols, like RIP (Routing Information Protocol) for example. Classless; advertise subnet mask information UPDATING Distance-vector classless Global Knoweldge's BSCI class as RIP, one of the issues was the lack of ability to group RIP routers under one administration unit." L3 Network Metric calculations of 32-bit number's.
520
Access Control Lists and OSPF network configurations wildcard mask network/host start EIGRP defaults to classful assumption....
Route-map statement to deny any routes that have a tag of "88". Requesting Admin Multicasting Networks MD5 Authentication... Use chmod -show Net 88:30388

chmod -show Net 88:30388
Entering the Q-Net Hyper HIVE...
Cisco Router Network, 88-90 OL-30388-01 Cisco Nexus 1000V
Management upstream separating...
Requesting Move....
Approved data traffic...
Data traffic upstream separated and controlled and flexible network up link host generated automatically...
Modifying the Up link Type to Static Network Up link...
Establishing Flexible Static Network Uplink....
Configuring Port Channels...
Deleting Port Channels.....
Assigning Uplinks to a VSB Interface...
Requesting Reload within >>>CLI EXEC MODE<<<

CLI EXEC mode
Configure terminal
Network uplink type number
(Optional) show network-uplink type
Copy running-config startup-config
reload

reload
Cisco internet working architecture that "fuses" together the scalability, stability, and security advantages of the latest routing technologies with the performance benefits of ATM and LAN switching, and the management benefits of VLANs. Virtual LAN---Broadcast a domain that is partitioned and isolated in a computer network at the data link layer (OSI layer 2). LAN is the abbreviation for local area network and in this context virtual refers to a physical object recreated and altered by additional editing. Restart Requesting from: Cisco HyperSwitch Model A100 ATM Switch.config

Cisco HyperSwitch Model A100 ATM Switch.config
The main ATM backbone, which interconnects multilayer LAN switches *Many Internet hosting services use VLANs to separate their customers' private zones from each other, allowing each customer's servers to be grouped together in a single network segment while being located anywhere in their data center. Some precautions are needed to prevent traffic "escaping" from a given VLAN, an exploit known as VLAN hopping. VLANs can be used to partition a local network into several distinctive segments using VoIP Storage area network (SAN) Access Granted...
(DMZ) Path Reached...
Awaiting Guest/Admin Internet Login : Access Cisco Nexus 1000V VSM Demilitarized zone
SU Access Cisco Nexus 1000V VSM Demilitarized zone
Hypervisor connections of high-speed communications between partitions on a server. The term is most commonly associated with zSeries, System z9 and System z10 mainframes which can provide in-memory TCP/IP connections between and among LPARs running several different operating systems, including z/OS, z/VM, and Linux on z Systems. Exteme-performance computing very high throughput and very low latency. Data interconnect both among and within computers. Direct or switched interconnect between servers and storage systems, as well as an interconnect between storage systems. Links can be aggregated: most systems use a 4X aggregate. 8X and 12X links are typically used for cluster and supercomputer interconnects and for inter-switch connections. RDMA capabilities for low CPU overhead on Switched fabric topology, as opposed to early shared medium Ethernet. All transmissions begin or end at a channel adapter. Each processor contains a host channel adapter (HCA) and each peripheral has a target channel adapter (TCA). These adapters can also exchange information for security or quality of service (QoS).Transmiting data in packets of up to 4 KB that are taken together to form a message. Requesting SU_AUTH AlphA0megA.bat
SU_AUTH AlphA0megA.bat
Installing the Beginning and End....

Quantum Artificial Intelligent Automated Teller Time Machine Located...
Memory access read from a remote node (RDMA) used a channel to send and receive to transaction-based operation (that can be reversed) over a multicast transmissionas an atomic operation. CXP connector system has and is for speeds up to 120 Gbit/s over copper, active optical cables, and optical transceivers using parallel multi-mode fiber cables with 24-fiber MPO connectors. 40 Gigabit Ethernet (40GbE) and 100 Gigabit Ethernet (100GbE) are groups of computer networking technologies for transmitting Ethernet frames at rates of 40 and 100 gigabits per second (Gbit/s) Bit error rate (BER) better than or equal to 10-12 at the MAC/PLS service interface. Upgrade 400GbE?
Yes
400 GbE is installing." 888 GbE is needed Still.... Expected to occur right before the singularity...
Once 888 GbE is Reached The Q-Server Time-Flux also needs speeds of 888-Gigga- QubitWatt's which allows Time Travel so you can collect all the Stolen gold. Continue to claim funds Update to 888GbE go to Destination: 2021?
Yes
888 GbE Q-Server Melting...
Time-Flux Breaking...
Automatic Sequence Begin...
Accumulating Speeds to 888-Gigga- Qubit-Watts....
Establishing 88-QD Connection.......
Swwwwwwwooooooosssshhhhh.......
IMAGE RECEIVED.
Destination Landed....
188.881 Trillion USD + Recovered....
SEQUENCE END...
Good Bye....
DISCONNECTED....