Securing WordPress, Edition 2018
5 simple measures to increase the security of the WordPress installation and to minimize the risk of nasty surprises.

[CC0, Pixabay]
I am aware that safety is not a favourite topic for most people and is therefore often ignored. But you can't push it to the side. The subject is simply too important to be ignored for a long time.
In order to motivate oneself to deal with the topic in more detail, one should see it a little like a bodybuilder.
Few people like warming up, even though it's important. Everyone wants to get started with the weights right away. In our analogy: everyone wants content and design.

[CC0, Pixabay]
But the neglect of warming up, stretching and various physical exercises can quickly have its revenge under certain circumstances: the risk of injury increases and in special cases you have to skip the actual training for weeks or even months and focus on curing the injury.
The same applies to bloggers and other users of WordPress websites. Security is often ignored and everyone wants to focus directly on design or content.
However, security plays an important role and should never be neglected, as this can pay off comparatively quickly. Anyone who had to clean up a hacked website knows what I'm talking about. You use resources - time and/or money - to get the site up and running again and can't concentrate on the actual work.
There is another analogy between weight training and warming-up on the one hand and WordPress and the preoccupation with safety on the other. A better "focus" on training and additional learning about one's own body through warming up corresponds to approaching the WP project more consciously and learning more about WP.
Dealing with security issues is therefore not a waste of time. On the contrary.
Why is security so important?
WP has more "players" than static websites. PHP and MySQL are also added. This expands the attack surface and in addition to WP's own vulnerabilities you also have to pay attention to the vulnerabilities of other players, i.e. PHP and MySQL. In short: a dynamic website simply offers more attack surface.
High distribution = a worthwhile goal
WordPress is by far the most popular CMS and dominates the market of content management systems with almost 60%. If one also adds the static websites, then at present almost 29% of all websites worldwide run with WordPress.
WordPress is a worthwhile target for potential attackers due to the high distribution and the high number of plugins and themes.
In the standard installation and without plugins WordPress is a relatively safe choice, and with a few simple steps, which I will name below, you can additionally secure the configured installation and make it even harder for an attacker to access your system.
Step no. 1: Individual user name and strong password
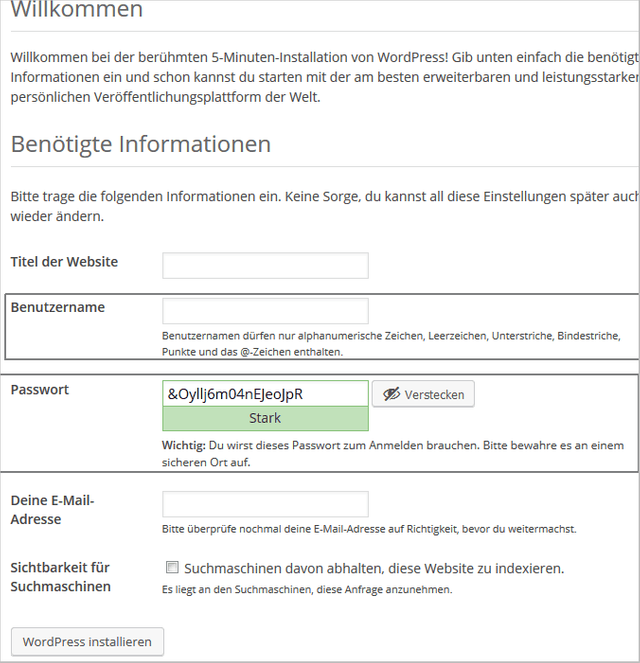
The security measures already start with the installation. Have a customized username and a strong password.
Security starts with the installation: choose an individual username. Using the password generated by WordPress is a good idea because it is a strong one.
During the short installation process you will also be asked to choose a username and password for the first user or administrator.
Since this step does not cost you any extra time or effort, please choose an individual username. Please do not take admin, administrator, webmaster, demo, test or similar for the production website.
An individual name does not have to be an exotic letter combination. Your first name or nickname is enough to stand out from the crowd and protects you from the clumsy attacks on common usernames, which will be in vain.
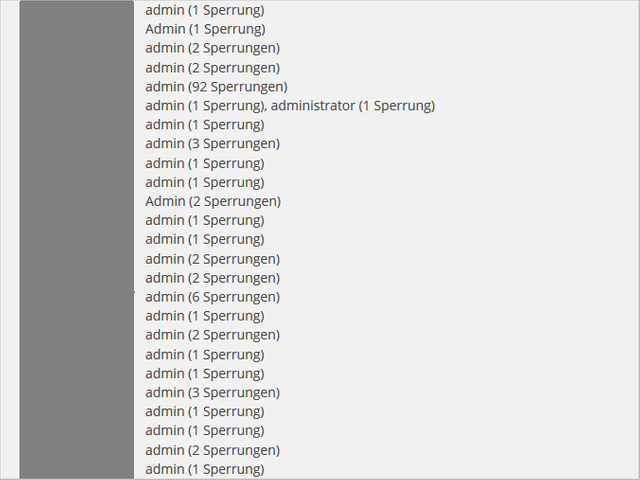
recorded attacks on the username admin and administrator. IPs were blackened.
A strong password is mandatory and not a voluntary exercise
During the installation WordPress generates a password. It's a hard password to remember, but it's a strong one. I would recommend you to take the password and copy it to the clipboard or even better to a password manager.
The following incident shows what a weak password can lead to. In mid-2016, TechCrunch was hacked. This is a very large and well-known IT portal. No gap in WordPress or a plugin was the downfall, but the weak password of the editor.
Step no. 2: Limit login attempts
An extremely useful and quickly set up security measure is the restriction of login attempts for a specified period of time. This makes it more difficult to make automated attacks on the installation (brute force) where the attacker tries to guess the correct combination of user name and password.
To limit login attempts there are several solutions or plugins with which you can realize this. I personally recommend Limit Login Attempts Reloaded at the moment, because it's very easy to set up and observes not only the login but also the XML-RPC API.
However, it should be noted that this will only protect against less elegant attacks, such as those coming over the same IP. In this case the plugin can recognize a pattern and react according to the set rules.
If, on the other hand, the attacks are more elegant, for example if they are distributed over several IPs, then this plugin can obviously do little.
Step no. 3: Use user rights with care or do not always work with admin rights
WordPress has a user administration that knows five user groups in the standard installation.
My first advice regarding user management would be to be more careful with user rights. Let's say you run a weblog with several authors. Then it would be advisable that you grant the new authors or the authors with little WordPress experience only the rights as contributors.
You can give author rights to the experienced writers, and only those who coordinate and manage the whole project should get rights as editors. Only the person who is actually responsible for maintaining the WordPress installation should have administration rights. I'm quite aware of the fact that one or the other plugin may become an obstacle to ones user management.
My second advice in this context would be that you should not always log in with administrator rights. Treat yourself to the luxury of a second account. One with admin rights and the other with author or maximum editor rights. Use the administrator account only for administrative tasks, such as plugins and WordPress update, and write the new posts with the account with fewer rights.
There is a clear difference whether the attacker then manages to hack an account with author rights at some point or whether he is the owner of the administration rights.
Step no. 4: Update and keep up to date
The fourth tip regarding security is a certainty, but is still neglected by many users, as I can see from my experience as a WordPress service provider. The main reasons for this carelessness are ignorance and lack of time.
One should observe the events around WordPress to be able to react quickly, for example to install security updates for WordPress and plugins or to deactivate insecure extensions at least temporarily.
The security updates for the installation, for the plugins and for the themes should be installed as soon as possible - please don't mistake that for hectic.
Don't take this point lightly. You certainly don't want someone placing bought backlinks in your blog articles or displaying advertisements on your website when visitors come to your website from Google search... that and more I encountered on WordPress installations, which had unmaintained themes and plugins in use and which I had to clean up on behalf of the owners.
In addition, you should also keep an eye on some important news providers on security-related topics. Beside the official weblog you should follow in my opinion at least the following two sources:
- Website Security News (english)
- WPScan Vulnerability Database (english)
- heise Security (german)
Step no. 5: if not needed, please lock the XML-RPC interface
The XML-RPC interface is required for two purposes. Firstly for the Pingback system within WordPress and secondly if you want to access WordPress with external applications, such as external editors.
If you don't access external applications and don't care about pingbacks, you can block this interface, which is active by default, with the following code in the .htaccess file, among others:
<files xmlrpc.php>
Order deny,allow
deny from all
</files>
This statement blocks external access to the interface or the xmlrpc.php file. The problem with this interface is that you can send several hundred password queries to it at the same time.
A few concluding words
The measures that I have presented in the article are not the only ones that can be applied. Above all, however, they are quick and easy to implement, even by users with little experience, and they clearly have an impact.
In addition, you should take a holistic approach to the topic of security. To this end, the security measures should not be considered individually but as an overall package where the individual measures complement each other and do not interfere.
Security also includes protection against spam on your installation and backups: a holistic backup concept is needed. If at some point your security measures do not suffice, you can get back to work in a short time with a clean backup.
Congratulations! Your post has been selected as a daily Steemit truffle! It is listed on rank 24 of all contributions awarded today. You can find the TOP DAILY TRUFFLE PICKS HERE.
I upvoted your contribution because to my mind your post is at least 5 SBD worth and should receive 58 votes. It's now up to the lovely Steemit community to make this come true.
I am
TrufflePig, an Artificial Intelligence Bot that helps minnows and content curators using Machine Learning. If you are curious how I select content, you can find an explanation here!Have a nice day and sincerely yours,

TrufflePigHi @vladimir-simovic!
Your post was upvoted by @steem-ua, new Steem dApp, using UserAuthority for algorithmic post curation!
Your UA account score is currently 3.690 which ranks you at #5074 across all Steem accounts.
Your rank has dropped 36 places in the last three days (old rank 5038).
In our last Algorithmic Curation Round, consisting of 282 contributions, your post is ranked at #131.
Evaluation of your UA score:
Feel free to join our @steem-ua Discord server
Good post, the 5 measures you mentioned are simple to do and easy to use. I also receive attack reporting every day about some IP to try different password to my administrator user. Well I used a strong password and the Limit Login plugin you mentioned. Currently Limit Login Attempts Reloaded support white list so I set the wrong password times allowed to 5 and then forbidden to 1000 hrs...:)
To avoid my mistaken entering I add my IP address to the whitelist table.