THE WIZSEC GROUP CALLED VINNIK THE MAIN SUSPECT IN THE THEFT OF THE MT.GOX FUNDS

WizSec, a group of enthusiasts who have been conducting their own independent investigation concerning the theft of funds from the Mt.Gox exchange for several years, have published the first part of the results of their investigation.
The impetus for the release of information was given by yesterdayэs arrest of Alexander Vinnik, whom the group considers one of the key figures in the case of laundering stolen bitсoin.
“This is the result of many years of work. Everyone who has worked on this case has patiently remained silent, directing the results to the law enforcement agencies.”
The facts published by WizSec are as follows:
In September 2011, the private keys of the hot Mt.Gox wallet were stolen. This gave the hacker access to a large number of bitcoins and control over all incoming transactions.
The hacker deduced funds regularly and sent bitcoins to the wallets supervised by Vinnik. This had been going on for a long time, but there were also breaks – the second stage of the theft occurred later in 2012 and 2013.
By mid-2013, the hacker had extracted about 630,000 bitcoins from the accounts at Mt.Gox.
After all the coins had been removed to Vinnik’s purseswallets, most of them were sent to BTC-e and sold or laundered (BTC-e codes). A total of about 300,000 BTC were on the BTC-e, while other coins were deposited on other exchanges, including Mt.Gox itself.
The funds of Mt.Gox were not the only coins stolen by Vinnik. The funds stolen from Bitcoinica, Bitfloor and during several more thefts which occurred at the end of 2011 and 2012 were laundered through the same wallets.
Moving coins back to Mt.Gox became a clue, which allowed identifying Vinnik, since the Mt.Gox accounts he had used were associated with his online identity “WME.”
After determining the actual transactions for most of the stolen bitcoins at Mt.Gox, the group tracked them and combined all the addresses, quickly discovering that the other stolen coins could be tracked to the same purses. Below, there is a generalized picture illustrating the theft of the monetary flow in September 2011.
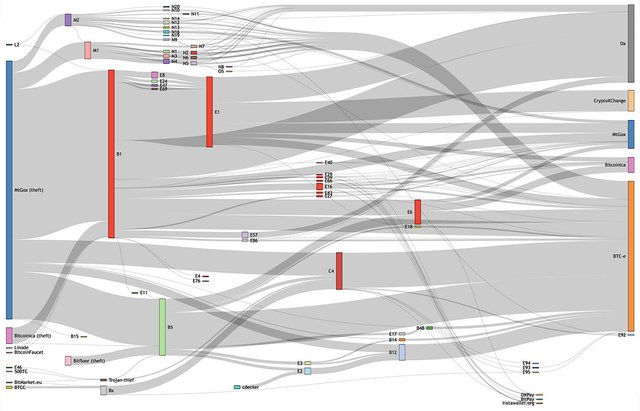
When some coins were redirected back to Mt.Gox, determining which accounts were used to receive them became possible. Two entries were of interest and it enabled establishing a connection with the online identity “WME.”
“WME was involved in the theft of Bitcoinica funds, which served as another convincing proof that we identified the right person who had apparently been the main money launderer behind the robber of Mt.Gox.”
The investigation has also showed that Vinnik is not a hacker/thief – he is only a launderer of the money. Perhaps he simply bought cheap coins from the hackers or offered money laundering services.
But he is the decisive puzzle in this jigsaw, since he probably knows those who have committed the theft, and, therefore, his capture is a major breakthrough in the matter.
The group expressed an assumption that law enforcement agencies would take the next steps and identify other persons involved in the criminal scheme, and promised to soon publish the second part of the investigation results.

WANT TO BECOME A CRYPTONAIRE?
At Cryptonaire, we do things a little differently...
We don't try and be polite about things.
We build systems to help people from all over the world create wealth from the Cryptocurrency markets....FAST.
We create our own success and we CRUSH everything in our path to take our game to the next level as entrepreneurs.
TAKE YOUR BUSINESS TO THE NEXT LEVEL...
A BUSINESS LIKE NO OTHER, DON'T WASTE MY TIME OR YOURS GET IN NOW! SIGN UP NOW HERE: http://www.cryptonaire.co/Amadat