Block PSExec.exe being running from remote computer
Hi, I Am Rohit Chauhan and today in this article we will see how to block psexec.exe being running from remote computer and for those who don't know what pstools is actually see this link
https://docs.microsoft.com/en-us/sysinternals/downloads/psexec
let's get started
So it seems there is yet another piece of ransomware in the wild which is more sophisticated than Wannacry as it uses multiple attack vectors. I have read that one of these is once a machine is infected that it uses the great SysInternals utility psexec.exe, and possibly Microsoft’s command line WMI utility wmic.exe, to spread further. Whilst there are products, like Ivanti Application Control, formerly AppSense Application Manager, that can be used to blacklist these, if you haven’t got those products today then you need a way of stopping these attack vectors. One way would obviously be to delete wmic.exe, or remove NTFS permissions to it, but you can’t do that for psexec since presumably the malware is either downloading it or has it embedded within its payload.
to block pstools being executed 2 method is available
1.disabling windows default share
2.Through Registry
1.disabling windows default share
How psexec run ???
So when psexec is used to run something on a remote system, it works by creating a new service executable called psexesvc.exe which is embedded within the original psexec.exe file. This is copied to the Windows folder on the remote machine via the admin$ default share (hence why you need to be an admin to get psexec to work remotely). It then creates the PSEXESVC service with this, now local, executable, starts it and then runs the specified command.
to disable admin$ share folder follow this steps.
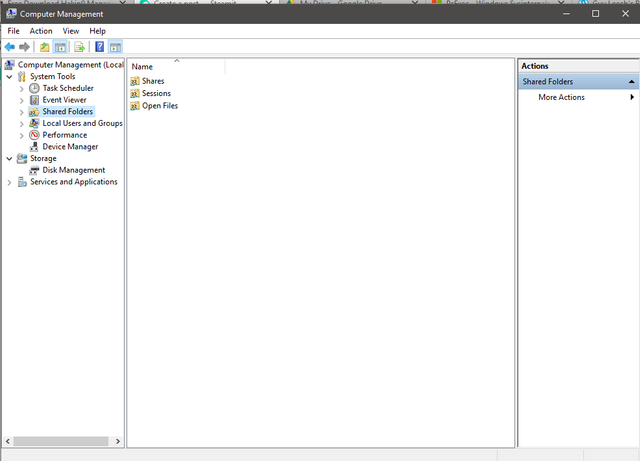
1.open computer management this will open windows like this
2.open Shared Folder and select Shares
3.right click on admin$ share and select "stop sharing"
All Done .....!
- Through Registry
Here is where we can use the little known Image File Execution Options (IFEO) registry key to put a temporary, or permanent, block on these, or any other executables, so they cannot run. We can either get them to fail silently or run a script informing the users that their machine is infected
What you have to do ??
In its simplest form, create the key “psexec.exe” in “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options” and then create a REG_SZ value called “Debugger” and set it to any file that you want to execute when psexec run.
if you dont want to follow download direct registry file from here
https://drive.google.com/open?id=11uub9gYFNf-SGozloEwBjNYVJP1I1hDG
Done !! You have sucuessfully blocked psexec
I hope this helps some of you and stay safe (and don’t run routinely with admin privileges!)
Congratulations @rohitc9537! You received a personal award!
Click here to view your Board of Honor
Congratulations @rohitc9537! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!