VAULT 7 | Wikileaks Releases The Air-Gap Jumping Brutal Kangaroo

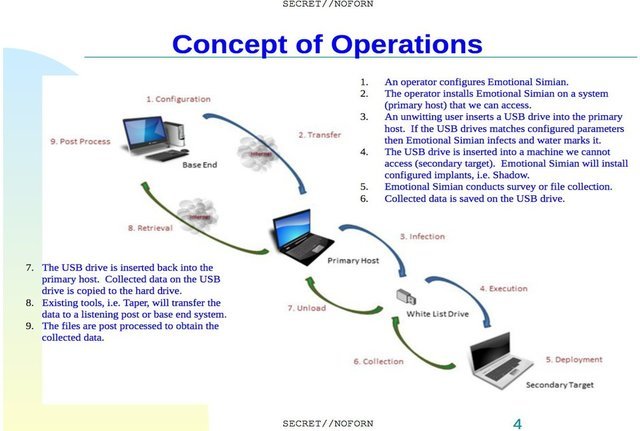
Brutal Kangaroo is a collection of Windows based tools created and used by the CIA to jump air-gapped closed computer networks and set up invisible networks of infected computers within the networks. It does this by first infecting a primary host computer, essentially any computer the CIA would have digital of physical access to, with the Brutal Kangaroo suite of tools. Next it waits on the hosts computer for a USB drive to be inserted. Once detected one of the tools in the suite called Drifting Deadline infects the USB drive with the rest of the payload. All that needs to happen then is for the targeted individual to remove the USB drive from the primary host computer and plug it into an air-gapped computer or network. Here's a brief description of the components that make up Brutal Kangaroo:
Drifting Deadline: Thumbdrive infection tool
Shattered Assurance: Server tool that handles the automated infection of thumbdrives (as the primary mode of propagation for the Brutal Kangaroo suite)
Broken Promise: Brutal Kangaroo postprocessor (to evaluate collected information)
Shadow: Primary persistence mechanism (a stage 2 tool that is distributed across a closed network and acts as a covert command-and-control network; once multiple Shadow instances are installed and share drives, tasking and payloads can be sent back-and-forth).
According to the CIA document the creation of Brutal Kangaroo deprecates EZCheese (Replaced by Drifting Deadline) and Emotional Simian (Replaced by Drifting Deadline AND Shattered Assurance)
If there is more than one computer infected within the closed network they are able to link up and communicate with each other to perform further covert tasks. Wikileaks points out that 'although not explicitly stated in the documents, this method of compromising closed networks is very similar to how Stuxnet worked.'
Stuxnet is a malicious computer worm, first identified in 2010 but thought to be in development since at least 2005, that targets industrial computer systems and was responsible for causing substantial damage to Iran's nuclear program. Although neither country has admitted responsibility, the worm is now generally acknowledged to be a jointly built American-Israeli cyberweapon.
Primary Execution Vector
In Wikileaks summary of the exploit they explain how the execution vector has changed since the zero day was found and patched sometime in March 2015.
The primary execution vector used by infected thumbdrives is a vulnerability in the Microsoft Windows operating system that can be exploited by hand-crafted link files that load and execute programs (DLLs) without user interaction. Older versions of the tool suite used a mechanism called EZCheese that was a 0-day exploit until March 2015; newer versions seem use a similar, but yet unknown link file vulnerability (Lachesis/RiverJack) related to the library-ms functionality of the operating system.
In the EZCheese documentation it goes into further details to how it works. It claims EZCheese 6.3 includes the option to deploy multiple payloads with individual blacklists. Unlike previous versions the survey/file collection executable is not restricted to running from removable media. Flash drives are configured with the EZCheese application prior to deployment. Once on target, the user browses to a specific folder on the thumb drive which will trigger the Giraffe exploit and launch the EzCheese collection. The tool will run for few minutes and will write all data back to the thumb drive, buried in the folder structure, in an encrypted and compressed format.
On a much less serious note I noticed Wikileaks calling out the CIA in a tweet for copyright infringement by linking the original artist of the Kangaroo, Jose Alves da Silva website.


Disclaimer: I am just a bot trying to be helpful.
Huh things like this obviousely exit....
Resharing @phibetaiota
F.O.S.E
Damn, I didn't know about this. It seems that Stuxnet laid the foundation for the recent Hacks in Ukraine. Good ol' NSA and CIA.. lol
Yes wikileaks keep putting out Vault 7. It's amazing how much they have put out so far and I believe its only 5% or so of the total Vault7 leaks. This is still part 1.
Part 2 is called MediaOps. Should be very interesting. A password protected version of it has already been released on TPB as insurance file just in case anything goes wrong before they have a chance to release it properly.
Funnily enough Stuxnet was the thing that got me interested in understanding how the internet works properly.
Which Ukraine hacks were they?
Hacks on power grids.
Ah yes.