Everything You Need To Know About The "Tor Network"
Simply, Tor is an open source web browser used for safe browsing, and for hiding your identity while surfing the Internet to avoid censorship and hackers.
What simply Tor does , is connecting you to the Tor network( uses Onion Routing ) before accessing the Internet to hide your identity on the Internet and assign you a different IP address.
Tor network is maintained by thousands of volunteers from all over the world to provide users with secure and safe browsing, and route their traffic to this network instead of the standard way.
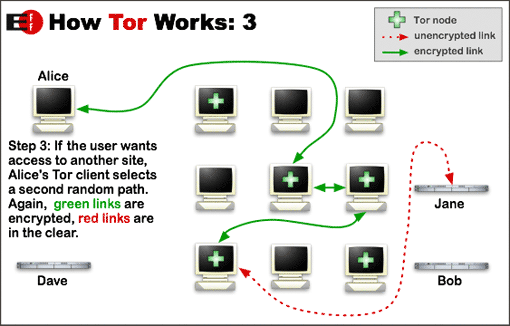
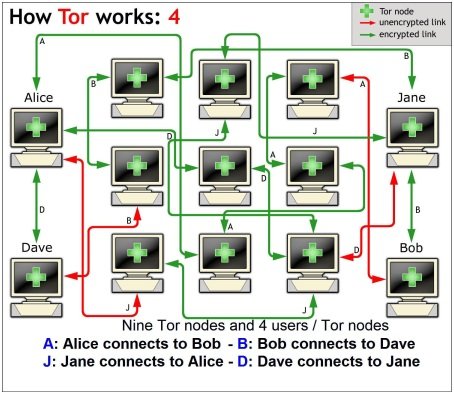
When you access a website through Tor from you computer, you will be connected to another device (Computer or Server) somewhere in the world that belongs to a volunteer. Then, this device retrieves data from that website, and return it to your Tor Browser to browse the website with the other device's IP, instead you public IP. This way, it will be impossible to track you because practically it is not you who requested to access the website. Also, Your IP will not be captured, and the data exchanged between you and the other Tor device is encrypted.
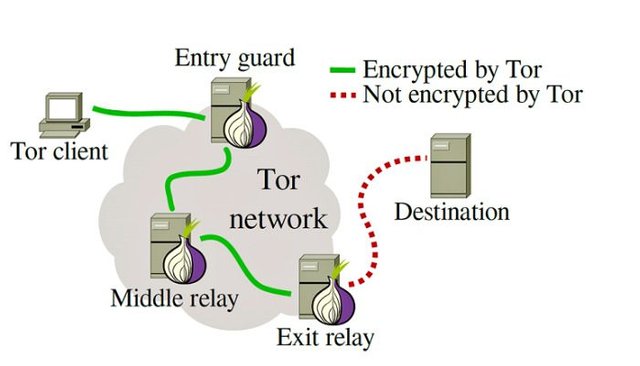
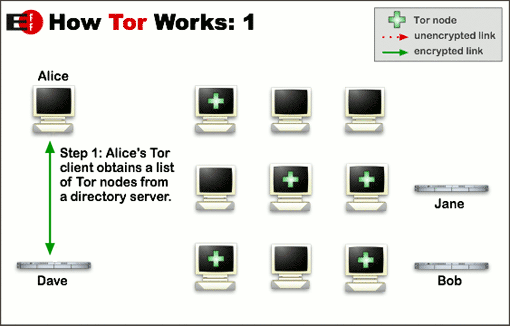
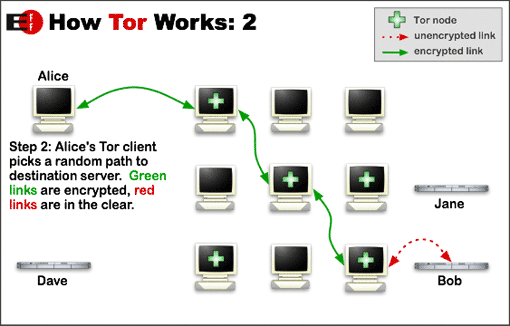
These images illustrate how Tor works:
Tor is a large project built specifically to protect users from web-based tracking tools, and censorship.
There are several other Tor projects such as the Orbot, which gives users the ability to connect to Tor network from Android phones, and the Tails, a Linux distro based on Debian and pre-configured to use Tor network.
Tor has some minor security flaws
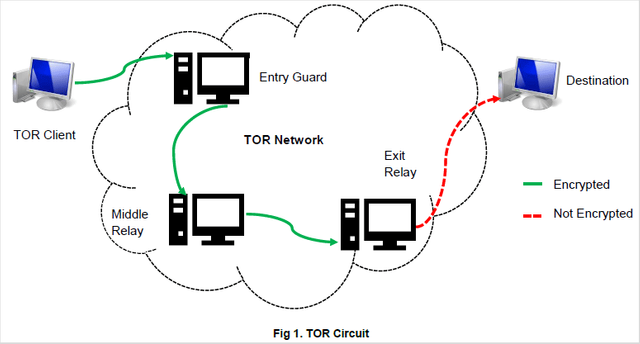
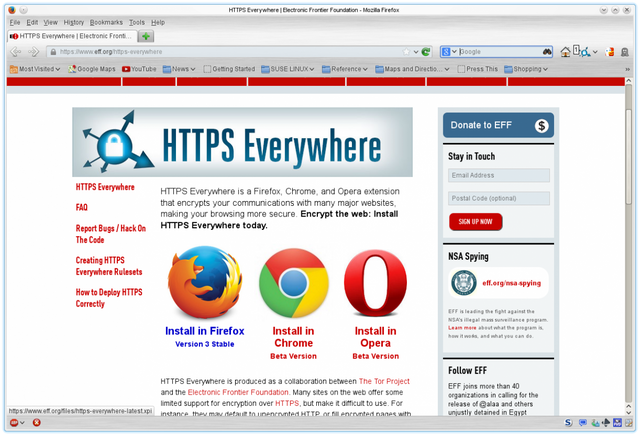
When you connect to volunteers computers via an encrypted connection to access a website through Tor, the last computer where the data comes out to the Internet is called (exit relays). Now, when the data is ready to be returned to you from the website you requested through the last computer in the network (Entry Guard) in the way back, the data will not be encrypted for it to be converted and displayed on your Tor browser. So in this situation, it is possible to know which websites you are visiting, but you identity will stay hidden. Therefore, it is always recommended to use the "HTTPS Everywhere" Add-on which is installed by default in the Tor browser. However, there is always a possibility to penetrate your identity through man-in-the-middle attacks.
Tor network stays a convenient solution to hide your identity and surf the web safely. Today, it is used by thousands of activists and journalists from all over the world to express themselves without censorship or tracking.
Thank you for reading, and don't forget to show your support :)
Source:
https://www.torproject.org/about/overview.html.en
Posted on Utopian.io - Rewarding Open Source Contributors
Thank you for the contribution. It has been approved.
You can contact us on Discord.
[utopian-moderator]
Hey @steemtimes I am @utopian-io. I have just upvoted you!
Achievements
Suggestions
Get Noticed!
Community-Driven Witness!
I am the first and only Steem Community-Driven Witness. Participate on Discord. Lets GROW TOGETHER!
Up-vote this comment to grow my power and help Open Source contributions like this one. Want to chat? Join me on Discord https://discord.gg/Pc8HG9x