These security bugs need to be addressed in Steemit.com website
I submitted a contribution on how to use OWASP Zed Attack Proxy to find security vulnerabilities in any web application. Upon analyzing https://steemit.com , it shows up security vulnerabilities which should be addressed.
Out of the vulnerabilities, I can see there is already an contribution about AWSALB cookie being non secure and not allowing httponly access. So I am excluding that cookie and reporting the other vulnerabilities :
The following Cookies are set without Secure Flag (other than AWSALB )
- stm1 , stm1.sig
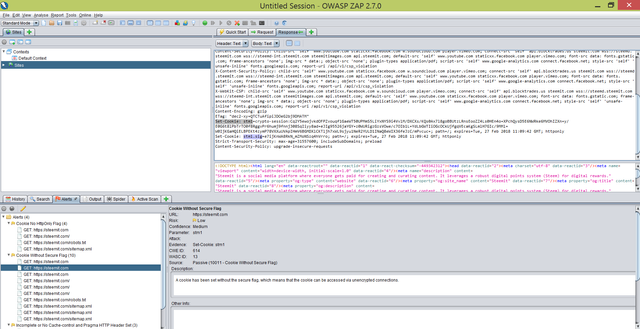
I have highlighted the two cookies in the above screen print.
Implications : A cookie has been set without the secure flag, which means that the cookie can be accessed via unencrypted connections. So an attacker can steal the cookie and potentially gain unauthorized access to the victim's web session.
Solution : Whenever a cookie contains sensitive information or is a session token, then it should always be passed using an encrypted channel. Ensure that the secure flag is set for cookies containing such sensitive information.
The scan also reports the following issue : Web Browser XSS Protection Not Enabled , or is disabled by the configuration of the 'X-XSS-Protection' HTTP response header on the web server.
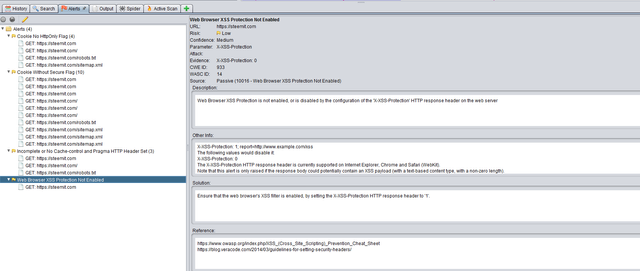
Here is some more info on this in the ZAP tool :
The X-XSS-Protection HTTP response header allows the web server to enable or disable the web browser's XSS protection mechanism. The following values would attempt to enable it:
X-XSS-Protection: 1; mode=block
X-XSS-Protection: 1; report=http://www.example.com/xss
The following values would disable it:
X-XSS-Protection: 0
The X-XSS-Protection HTTP response header is currently supported on Internet Explorer, Chrome and Safari (WebKit).
Note that this alert is only raised if the response body could potentially contain an XSS payload (with a text-based content type, with a non-zero length).
Solution : Ensure that the web browser's XSS filter is enabled, by setting the X-XSS-Protection HTTP response header to '1'.
The tool also reports another issue : Incomplete or No Cache-control and Pragma HTTP Header Set
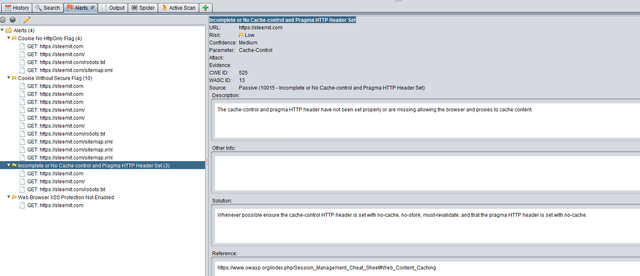
But I think its intentional because Steemit.com would allow the browsers to cache the content.
Steps to reproduce :
Download ZAP from the Wiki, its open source.
Launch ZAP and then in the Quick Start tab, enter https://steemit.com as URL to attack.
Click Attack and wait for few minutes till it attacks and prepares a report and all the issues.
Posted on Utopian.io - Rewarding Open Source Contributors
Great information from steemit leader..i like your post thanks for sharing dear....keep it up
Your contribution cannot be approved.
What you are doing here, is, for the most part, running a tool and pasting it's outputs/suggested solutions. This cannot be rewarded on Utopian. You could do this all day long, for countless projects and you already wrote two more or less identical posts, only with slightly different results that you pasted.
Also it is quite debatable if such security issues can be seen as a bug. A bug is always an actual development that doesn't work or work in an unexpected behavior. What you are pointing out here, aren't bugs in that sense. I would call it "missing security features".
But then, referring to @gtg's comments e.g. and my own investigation, it's still quite questionable how relevant these issues really are.
If you have any questions or feedback, you can contact us on Discord.
[utopian-moderator]