[php-sodium] Bindings for detached AEAD functions

New Features
This contribution includes AEAD detached mode bindings for the php-sodium extension.
About the libsodium-php repository.
libsodium-php is a PHP extension providing the bindings to the amazing libsodium C library, making its easy and secure functions available for usage on PHP projects.
Since PHP 7.2.0, the version 2.0 of the libsodium-php library was incorporated on PHP itself, making modern cryptography available as a builtin feature.
Since there are projects which may already being using the extension on their projects, the people responsible agreed on naming the embed extension as
sodium, to prevent conflicts. And development made on this repository eventually is backported into PHP source.
What feature(s) did you add?
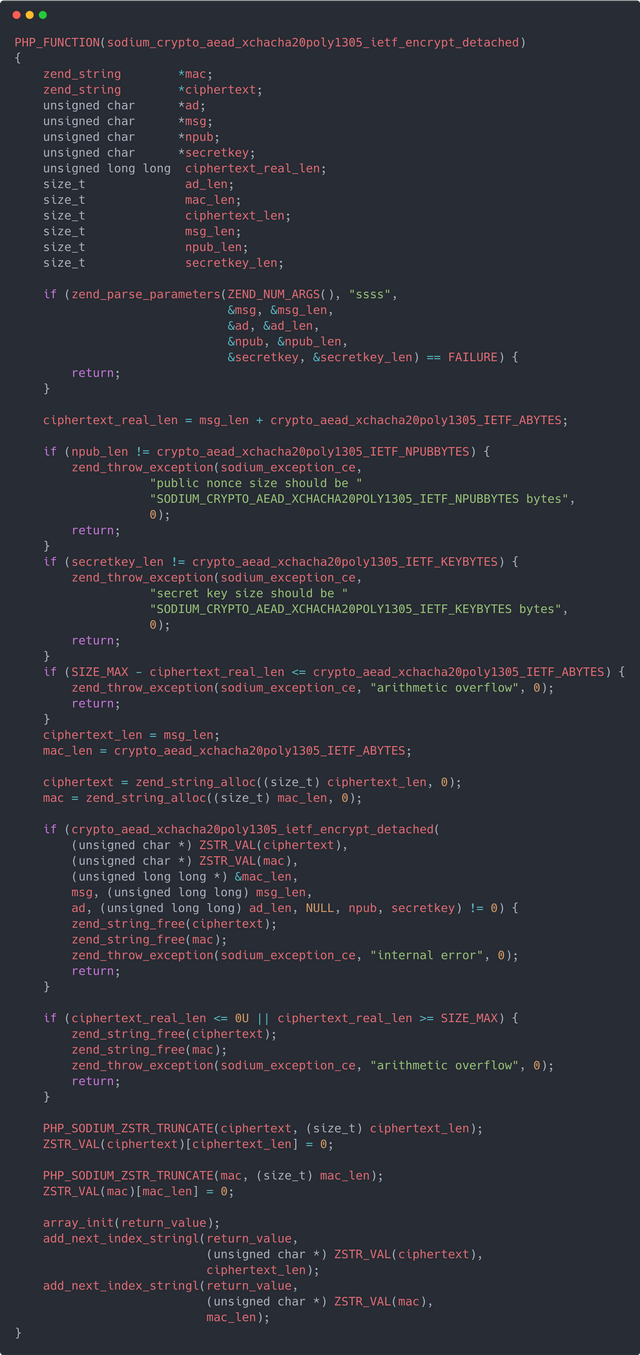
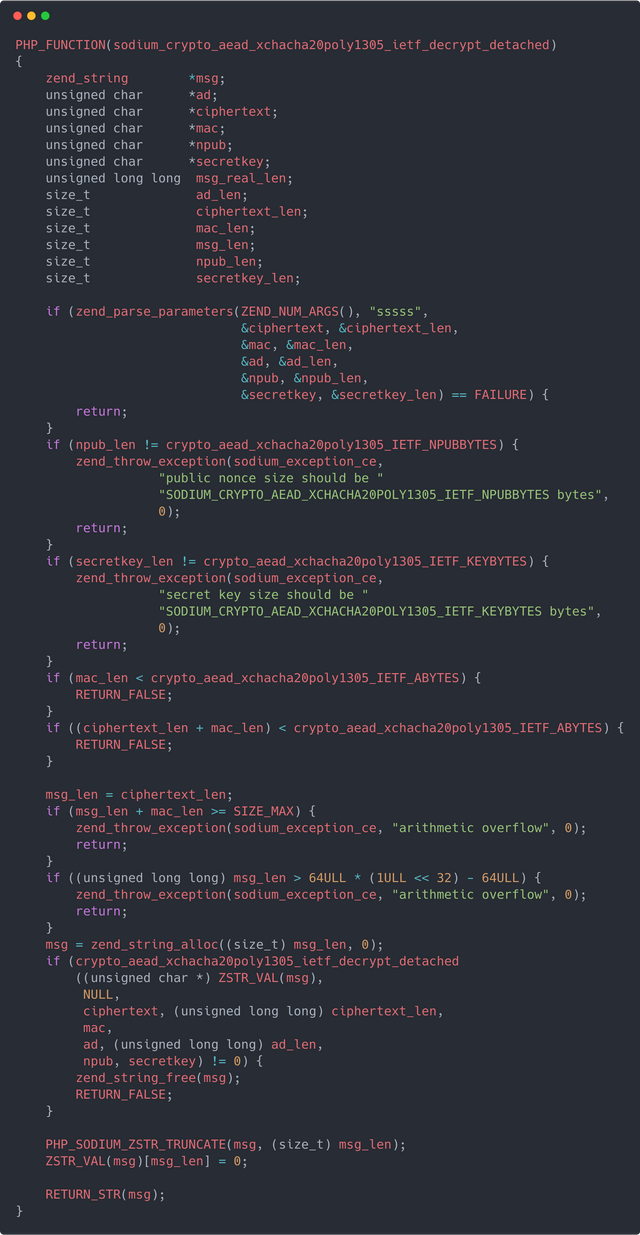
This contribution includes bindings for detached AEAD functions, not yet available for used within PHP, but a very useful feature of libsodium. Before this, the only mode avaialable was the default combined mode.
AEAD is a form of encryption with builtin authentication signatures, commonly referred to as authentication tags.
The combined AEAD mode returns both the encrypted data (ciphertext) and authentication tag as a single raw binary string output.
The detached mode, on the other hand, provides two outputs, the encrypted payload and the authentication tag separately.
One scenario where detached mode is useful are applications who transmit and receive the encrypted text, but the other part does not need to verify or decrypt the data.
Since the transmission channels or recipients don't need to verify the data, the authentication tag can be stored locally, and consulted upon decryption time, allowing smaller network usage while revealing almost nothing about the original content. This is also a very useful feature when the transmission channels are not very secure, meaning the authentication tag is not present, a brute force decryption attack will have no fast verification methods.
Contributed Bindings:
Encryption and Decryption on the four available AEAD constructs were provided, and the general approach is outlined below:
Detached Encryption:
Detached Decryption:
Usage:
Usage, is then, trivial. The encrypt methods will produce an array, where the first element is the encrypted data, the the second, is the authentication tag:
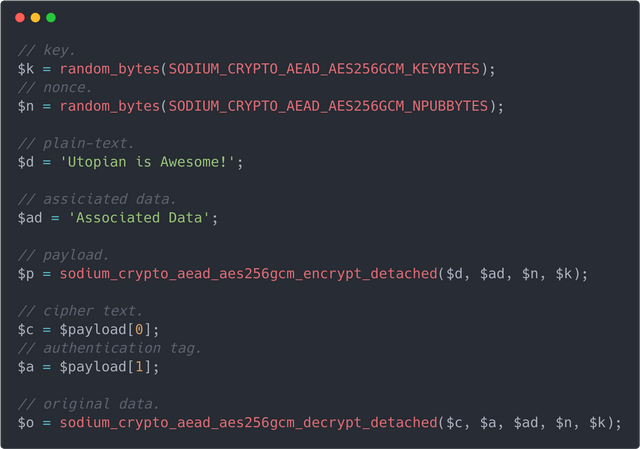 .
.
Posted on Utopian.io - Rewarding Open Source Contributors
Hey @hernandev! Thank you for the great work you've done!
We're already looking forward to your next contribution!
Fully Decentralized Rewards
We hope you will take the time to share your expertise and knowledge by rating contributions made by others on Utopian.io to help us reward the best contributions together.
Utopian Witness!
Vote for Utopian Witness! We are made of developers, system administrators, entrepreneurs, artists, content creators, thinkers. We embrace every nationality, mindset and belief.
Want to chat? Join us on Discord https://discord.me/utopian-io
keep up the good work!
Caramba... não sei nem o que comentar, parece grego mas imagino que na prática deve ser algo muito legal! Sucesso!
projeto #ptgram power | faça parte | grupo steemit brasil
projeto #ptgram power | faça parte | grupo steemit brasil
Thank you for the contribution. It has been reviewed.
I'm curious to know your affinity for AEAD and how you use it.
Need help? Write a ticket on https://support.utopian.io.
Chat with us on Discord.
[utopian-moderator]
Sorry @helo, wrote a bible in response but forgot to mention you so you could know about it haha
Thanks!
👍 Upvoted 😊 https://steemit.com/@a-0-0
thanks for the post. a lot of work has been done!