Linux Command Line Tutorial #7 - the sudo command
What Will I Learn?
You will learn how to use and configure the sudo command.
Requirements
- Basic linux knowledge
- Knowledge of using a text editor to open and edit files
Difficulty
- Intermediate
Tutorial Contents
Why do we need the sudo command?
When you use a linux system, you will most likely need to run important commands that are not available for the new user. Now, we could give everyone the root password, but that increases the chances of the root password leaking.
Instead, we could allow certain users, or certain groups to run a few(or all) commands as root, without them knowing the root password. This is exactly what the sudo tool lets us achieve. Basically, the sudo command lets the root account delegate the power to run a few(or all) commands with administrator(root) privileges to other users.
The sudo command is obviously the subject of a lot of memes, so I think most people are aware of how its actually used. This is the syntax:
sudo cmd
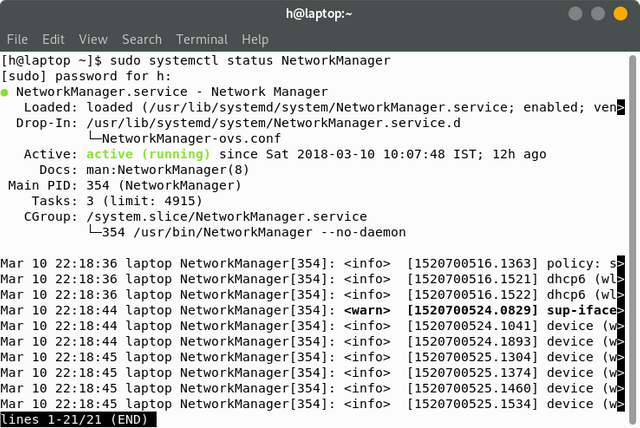
So if i wanted to see the status of NetworkManager using the systemctl status command, this is what i'd use:
But there are a few other command line arguments that are useful.
For example, if you have commands that depend on your environment, you can use the -E flag to preserve them when running the command, like so:
sudo -E cmd
If you actually want to check what commands you're allowed to run with the sudo command, you can use the -l argument. If i run it, this is what i get:
[h@laptop ~]$ sudo -l
User h may run the following commands on laptop:
(ALL) ALL
[h@laptop ~]$
The (ALL)ALL means that can run any command with sudo.
Another really interesting feature of sudo is that you can run a command as any user, not just root. You can do this using the -u flag. Like so:
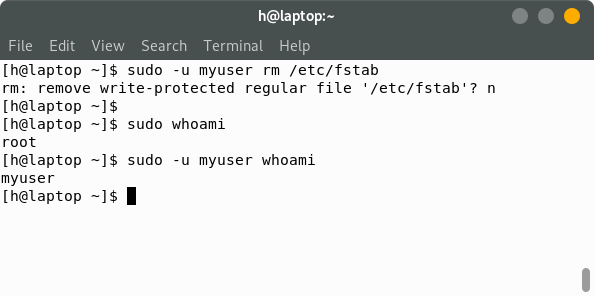
So in the first line, the prompt says that the file /etc/fstab is write-protected , ie the user myuser doesn't have the permission to write to the file. But if there was no -u flag set, it would have deleted the file right away.
In the following lines, running the whoami command gives the value myuser when the -u flag is set.
Configuring the sudo command by editing the /etc/sudoers file
One of the biggest Linux memes out there is the one where you run a command, but your user isn't in the sudoers file, and thus the "incident will be reported":

So where ARE the incidents ACTUALLY logged?
On ubuntu/debian systems, it's stored at:
/var/log/auth.log
On redhat systems, it's stored at:
/var/log/secure
On other systems it's simply stored in the system logs(sysconf or journald).
Editing the sudoers file using visudo
The file /etc/sudoers is used for configuring the sudo command. But this is a very important file, and if you get the syntax wrong, you could end up with a broken system. So we have to use the visudo command to edit this file. The visudo command makes a copy of the file, and checks the syntax before saving it.
So if you want to use the nano editor, you can use this command:
EDITOR=nano visudo -f /etc/sudoers
You'll see this:
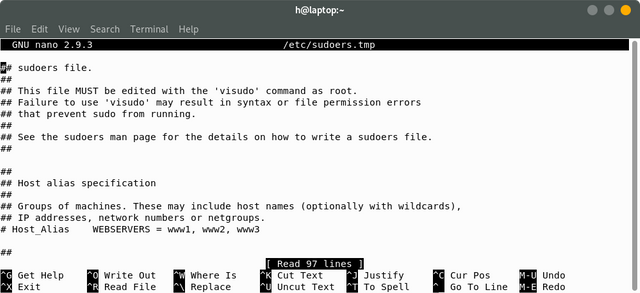
As you can see, we're using the sudoers.tmp file, not the actual sudoers file.
Allowing a user to use sudo
You can let a user use the sudo command, by adding the following line to the /etc/sudoers command:
USER ALL=(ALL) ALL
So in the case of myuser, this will be:
myuser ALL=(ALL) ALL
So after adding this, myuser can use the sudo command:
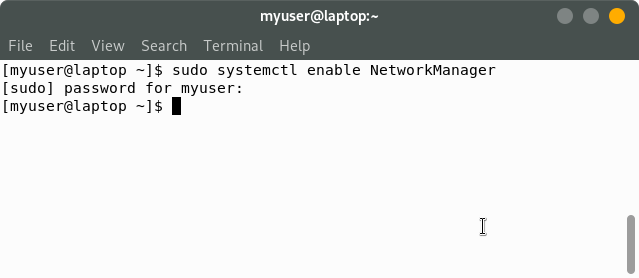
To allow all the users in a group to use the sudo command, use this command:
%GROUP ALL=(ALL) ALL
Allowing a user to only use certain commands with sudo
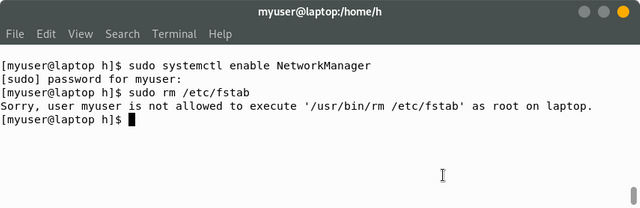
Let's say that you want myuser to be able to use the sudo command to only use the systemctl command, but not any other command. You can do that using this:
myuser ALL=/usr/bin/systemctl
With that set, myuser can use the systemctl command, but when you do anything else that requires root, we get an error message:
Disable password prompt for a user
Let's say that we totally trust myuser to be completely secure, and hence, there is no need to ask myuser for a password when it uses the sudo command. You can do so like this:
myuser ALL= NOPASSWD: /usr/bin/systemctl
After setting this, if we use the sudo command:
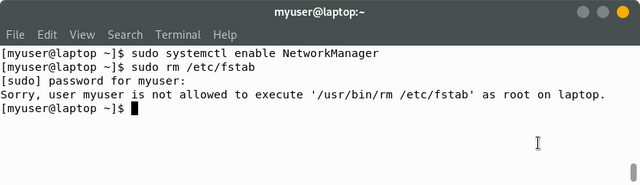
So as you can see, the systemctl command doesn't need a password, but other commands do(and if the command isn't specified in the sudoers file, it won't be allowed to be run).
Curriculum
Sources
- Header image from xkcd(https://xkcd.com/149/)
- xkcd - incident image - https://xkcd.com/838/
- All screenshots are of my own system.
Posted on Utopian.io - Rewarding Open Source Contributors
Thank you for the contribution. It has been approved.
Personal Note:
I would add more info to the What Will I Learn section next time so that readers can see right away the sub-points of the tutorial.
You can contact us on Discord.
[utopian-moderator]
Hey @flauwy, I just gave you a tip for your hard work on moderation. Upvote this comment to support the utopian moderators and increase your future rewards!
Thanks for the feedback! I'll do it next time.
sudo upvote ,I learned about visudo
sudo thank you :D
Good tutorial.
Here is a video you might enjoy that goes into enormous detail on the topic of sudo:
thanks. will check it out
Weird thing on OpenBSD they don't use sudo anymore. They use something called doas now. Which I assume is pronounced "do as".
See here is a discussion on doas:
https://news.ycombinator.com/item?id=9914693
hmm, very interesting. The BSDs have some very interesting stuff(like the networking utilities) that i wish were on linux.
Yeah you should check out the PF firewall which comes from OpenBSD. If you are on Mac then you are using PF without probably realizing it. Anyways will be following you, nice article.
Congratulations! This post has been upvoted from the communal account, @minnowsupport, by harshal from the Minnow Support Project. It's a witness project run by aggroed, ausbitbank, teamsteem, theprophet0, someguy123, neoxian, followbtcnews, and netuoso. The goal is to help Steemit grow by supporting Minnows. Please find us at the Peace, Abundance, and Liberty Network (PALnet) Discord Channel. It's a completely public and open space to all members of the Steemit community who voluntarily choose to be there.
If you would like to delegate to the Minnow Support Project you can do so by clicking on the following links: 50SP, 100SP, 250SP, 500SP, 1000SP, 5000SP.
Be sure to leave at least 50SP undelegated on your account.
Hey @harshallele I am @utopian-io. I have just upvoted you!
Achievements
Community-Driven Witness!
I am the first and only Steem Community-Driven Witness. Participate on Discord. Lets GROW TOGETHER!
Up-vote this comment to grow my power and help Open Source contributions like this one. Want to chat? Join me on Discord https://discord.gg/Pc8HG9x