Capturing WPA/WPA2 Passwords using Fluxion Network

This tutorial uses a lot of GIF as illustrations. Gently let them load: go and make you a coffee, you shall need it.
What we are going to do in this tutorial:
The goal is to retrieve a WPA/WPA2 key from a targeted network using social engineering and MITM (Man In The Middle)(1) attack. We are going to create a fake access point, known as "evil twin,"(2) and redirect users to a phishing page (Captive Portal)(3) to get the WPA/WPA2 key.
To achieve our goal, we are going to use the Open Source project called Fluxion-Network.
I will assume that you already have the following requirements:
- Kali Linux OS - If not, you can download the latest version here: https://www.kali.org/downloads/
** Don't know how to set up Kali? Check this other tutorial on Utopian.io - GitHub account - If not, you can create an account here: https://github.com/join
- MOST IMPORTANT: a Wireless adapter capable of packet injection and natively supported by Kali Linux
Note about the hardware requirement: I recommend Alpha Network products. The model AR9271 is recommended to begin this tutorial.
Step 1: Generate your SSH keys
An SSH key is used to identify yourself to an SSH server; it gives you access to install the Fluxion-Network repository from GitHub.
Run a Terminal and launch ssh-keygen. It is a tool used to create authentication key pairs.
ssh-keygen -t rsa -b 4096 -C "[email protected]"
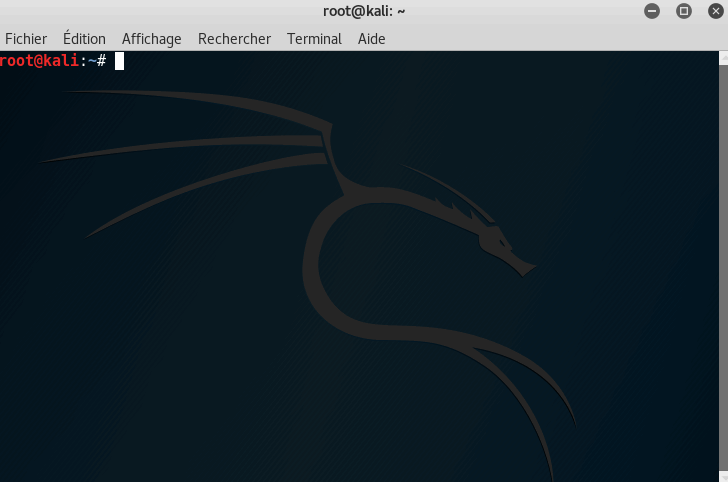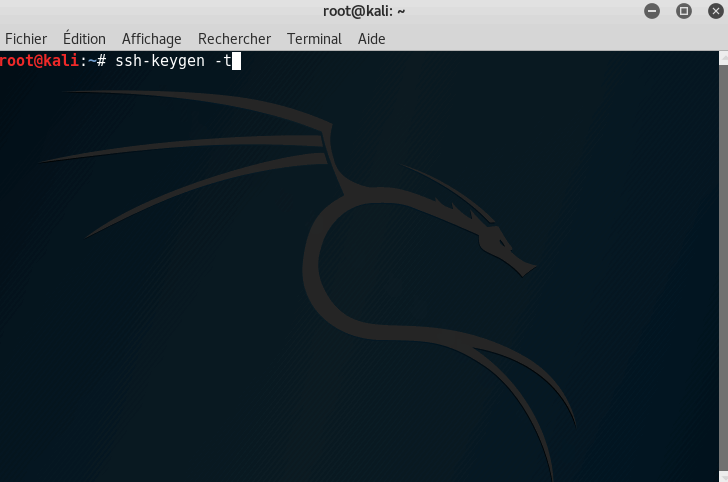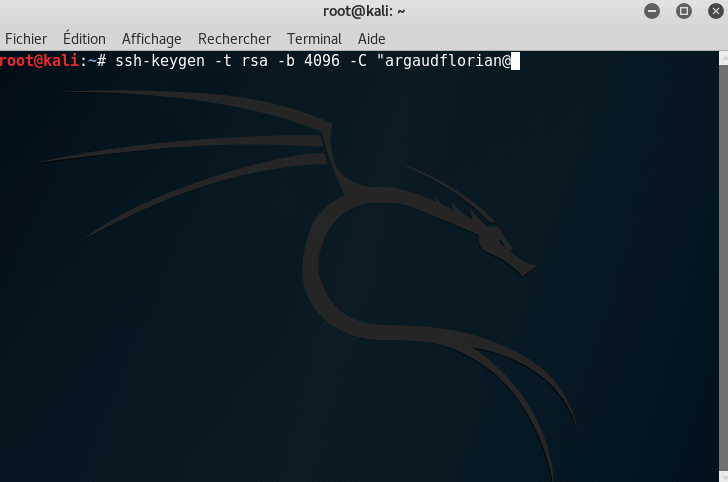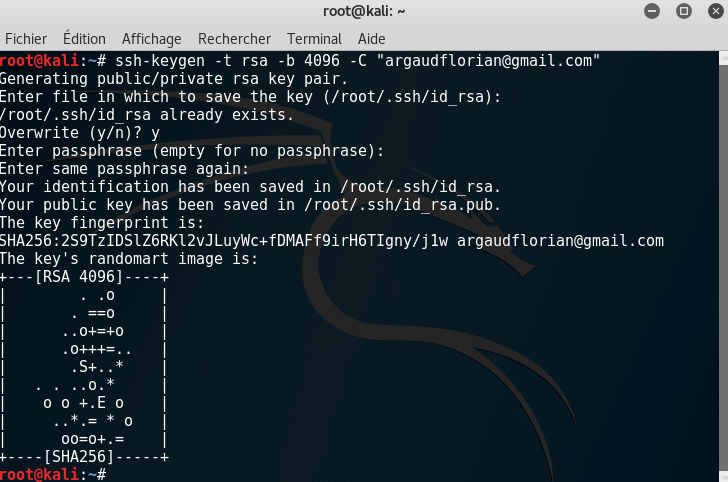
Note: Do not forget to replace [email protected] with your own (and valid) GitHub email address.
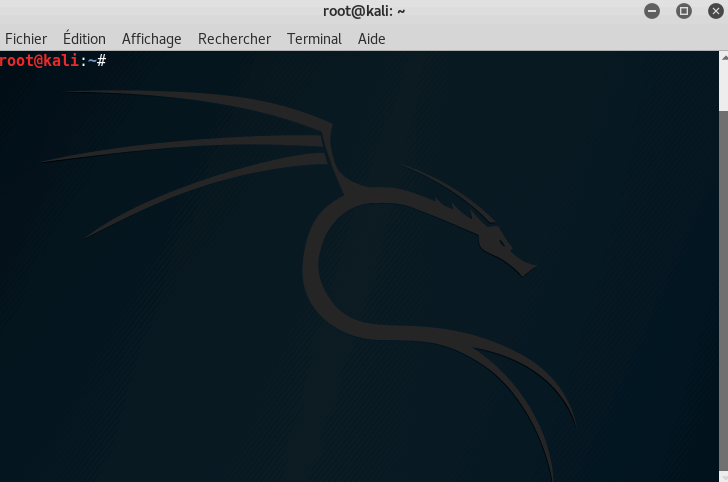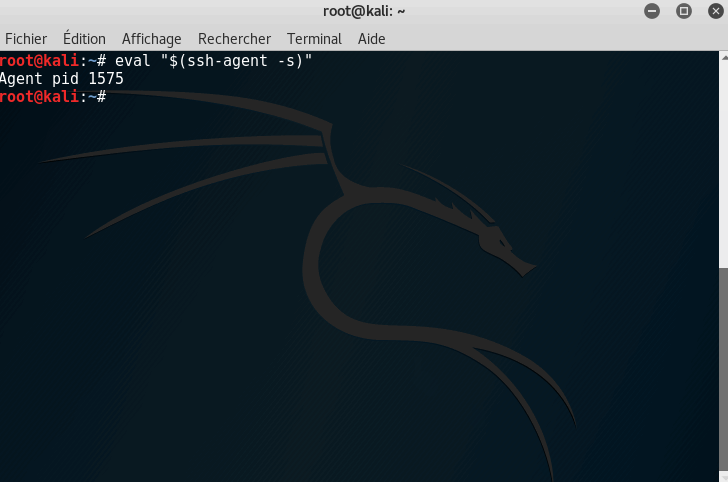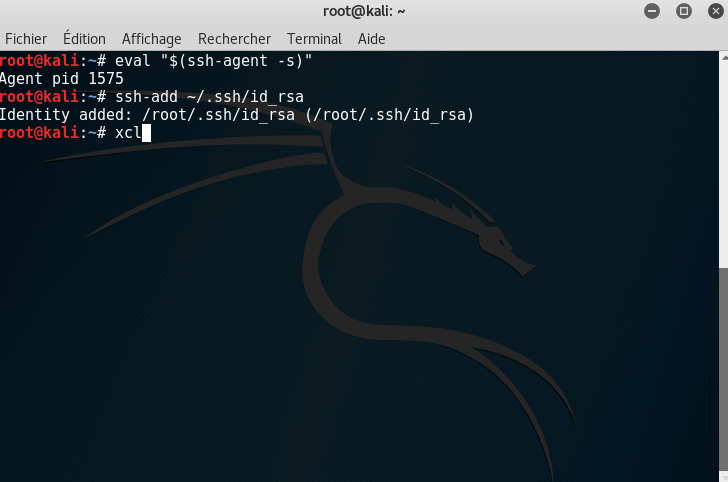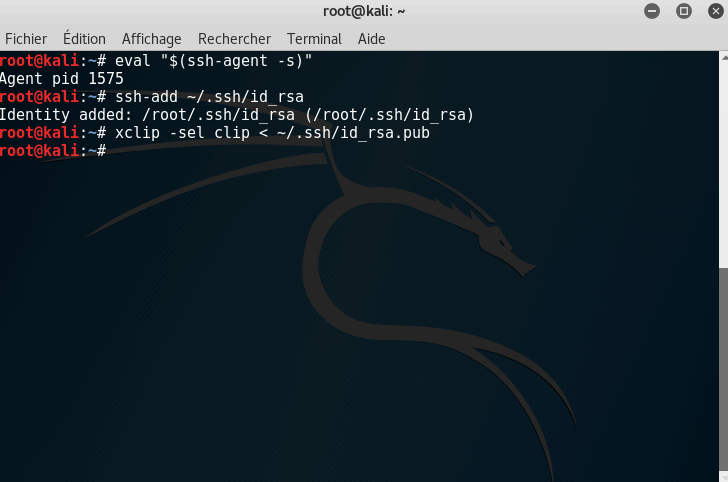
Run the ssh-agent
eval "$(ssh-agent -s)"
Generate a new SSH key
ssh-add ~/.ssh/id_rsa
Copy the generated key to your clipboard using xclip. This step avoids any mistakes when manually copying your SSH key.
xclip -sel clip < ~/.ssh/id_rsa.pub
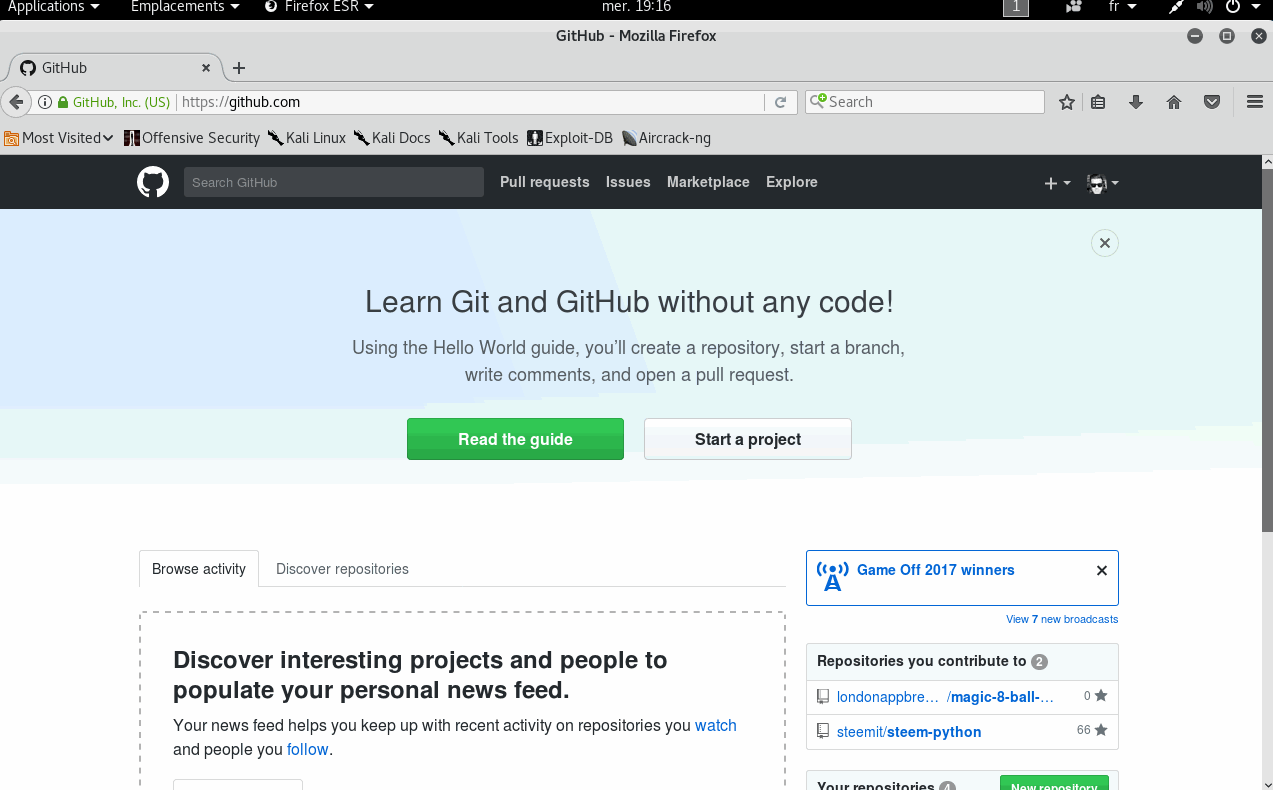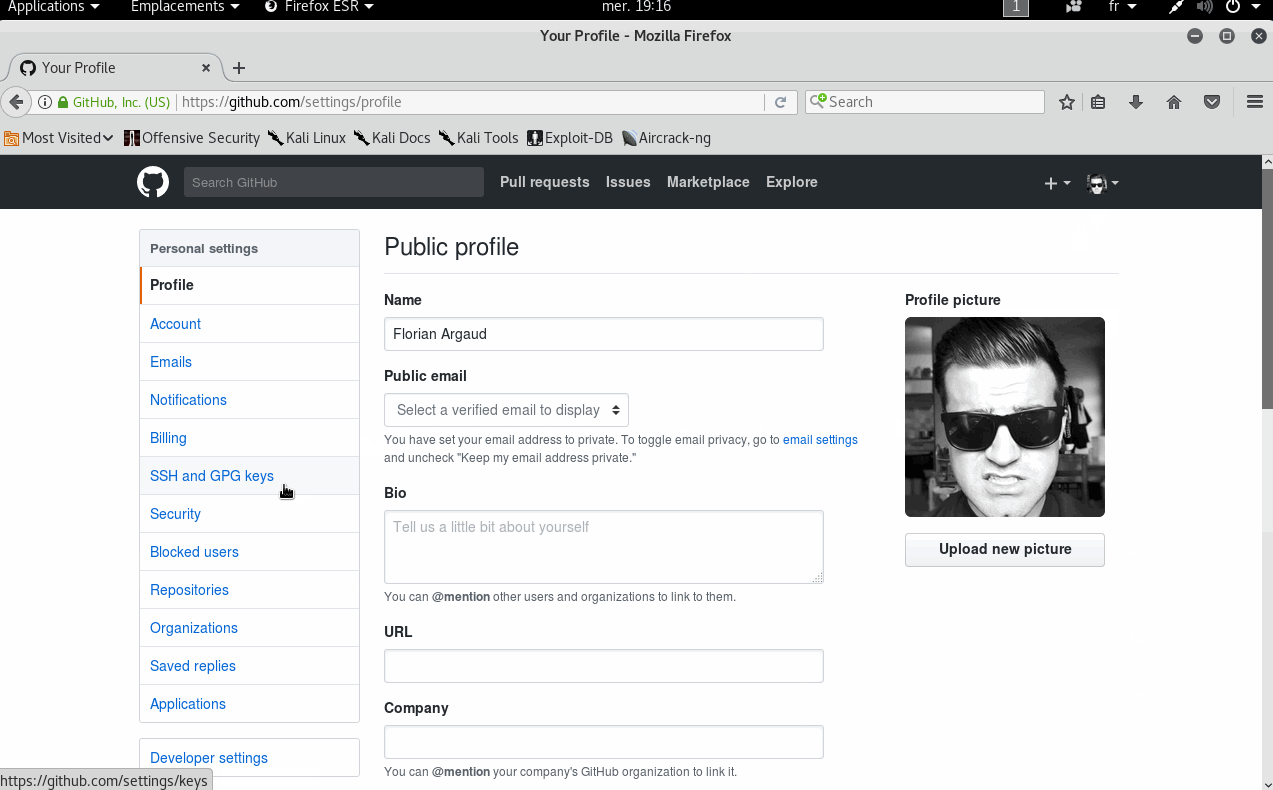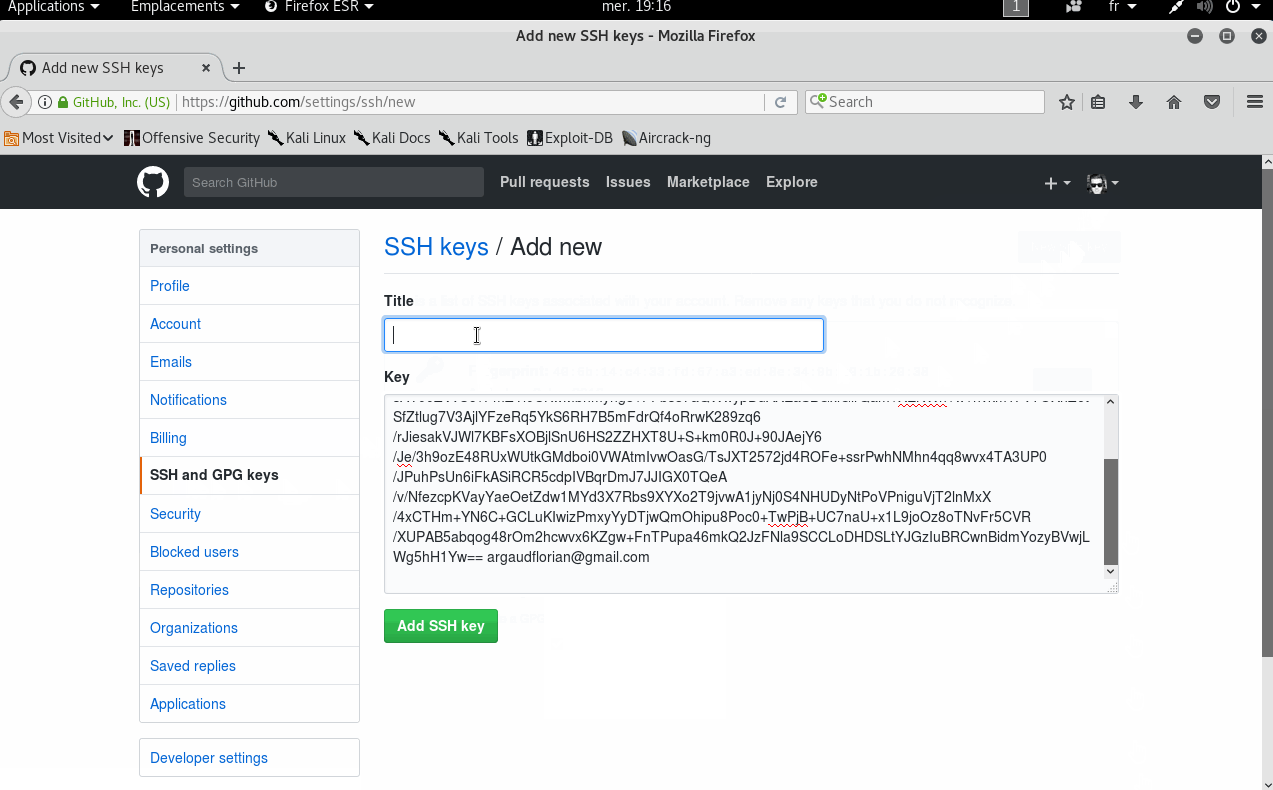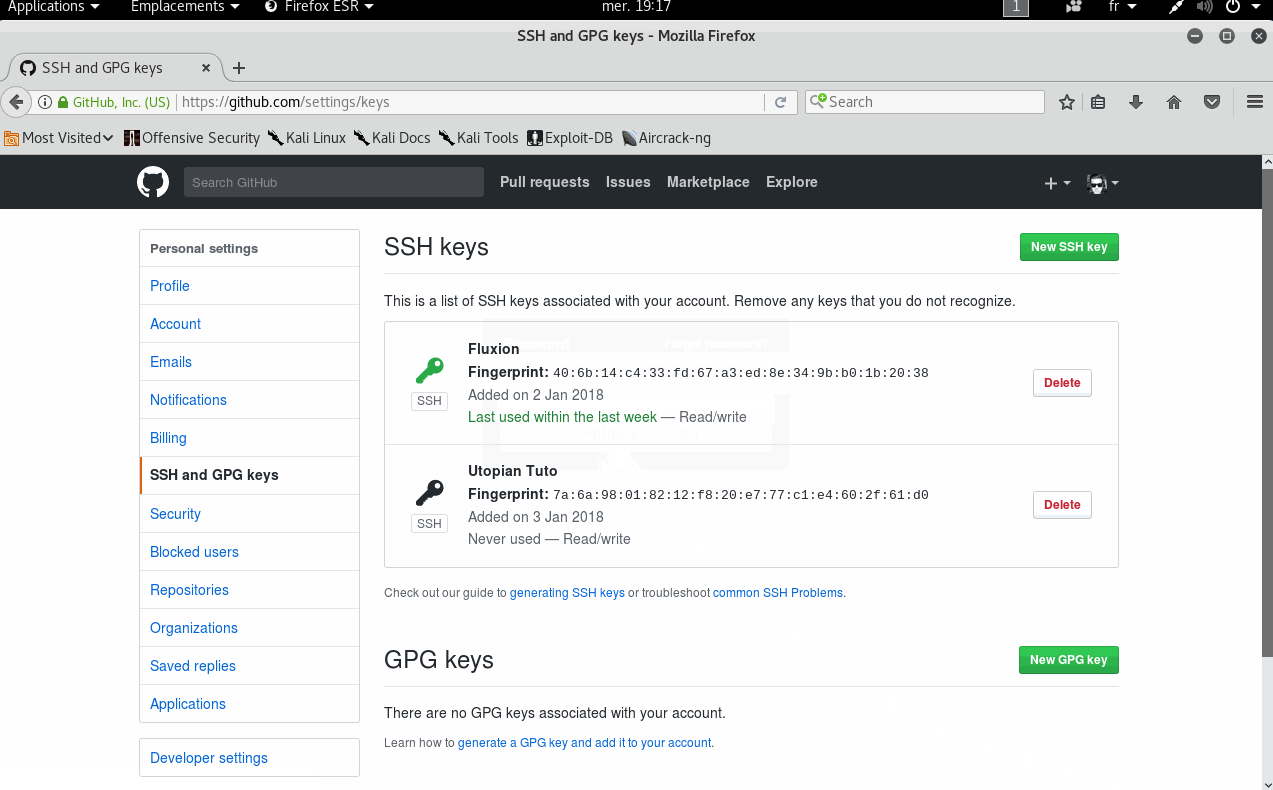
Once the key copied on the clipboard, it is time to create a new SSH key to GitHub. To do that, on GitHub, simply click on your picture, go to Settings, and click on "SSH and GPG keys."
Click on "New SSH key" and copy the key. The title is not essential.
Step 2: Install the latest Fluxion Network repository
First, you need to get the newest repository from GitHub. To do that, on a Terminal, type this line of code:
git clone --recursive [email protected]:FluxionNetwork/fluxion.git
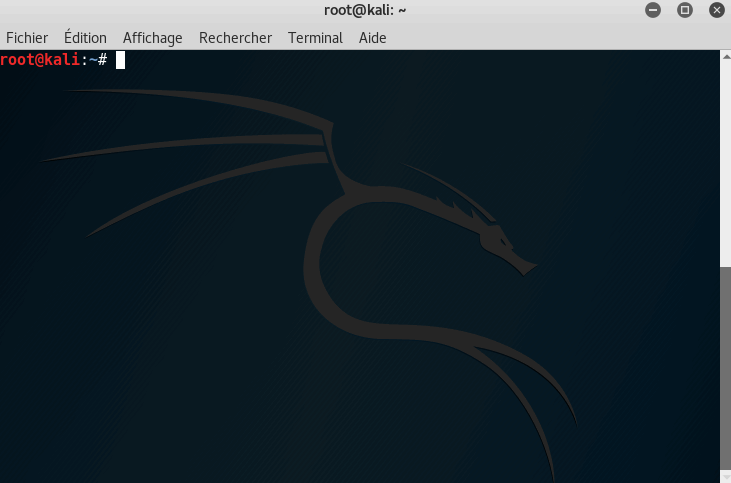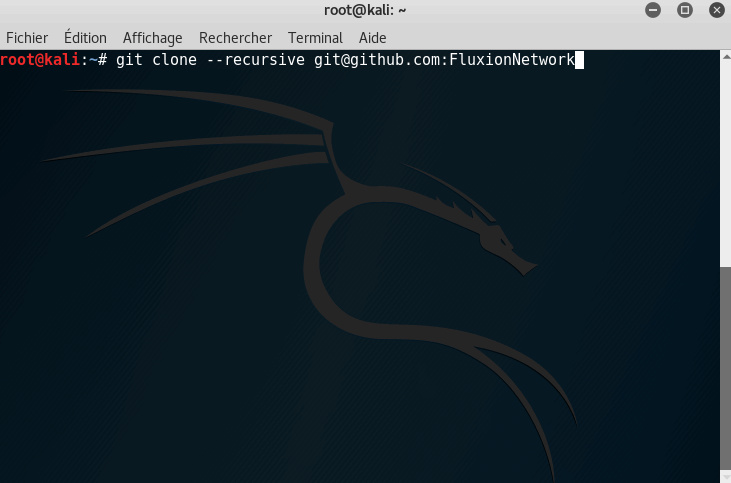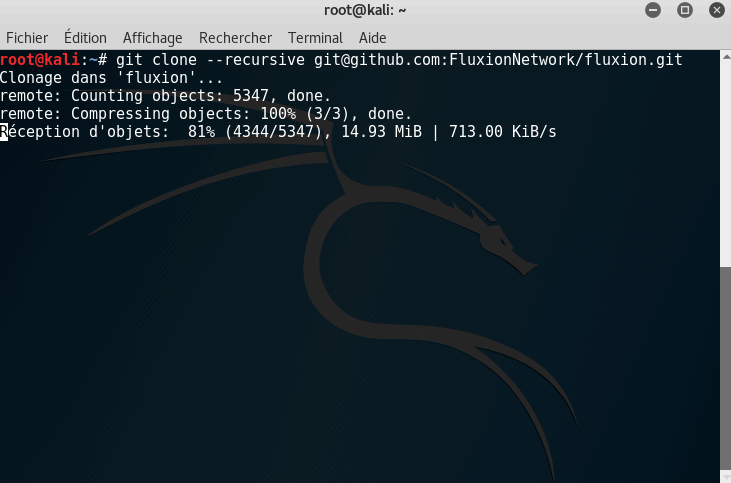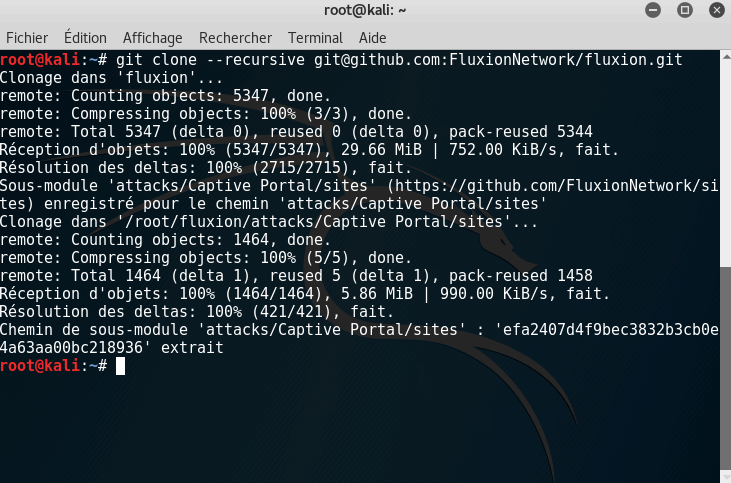
The installation can take some time, depending on your location and your network bandwidth.
When the installation is completed, go to the Fluxion directory by typing:
cd fluxion
You can now start Fluxion by entering:
./fluxion.sh
Note: Even if Kali comes with many pre-installed tools, some dependencies could be necessary. Fluxion AUTOMATICALLY install them if needed.
Once Fluxion is started:
- Choose your desired language (English recommended)
- Choose your hardware device (wlan0)
Step 3: Scan your target
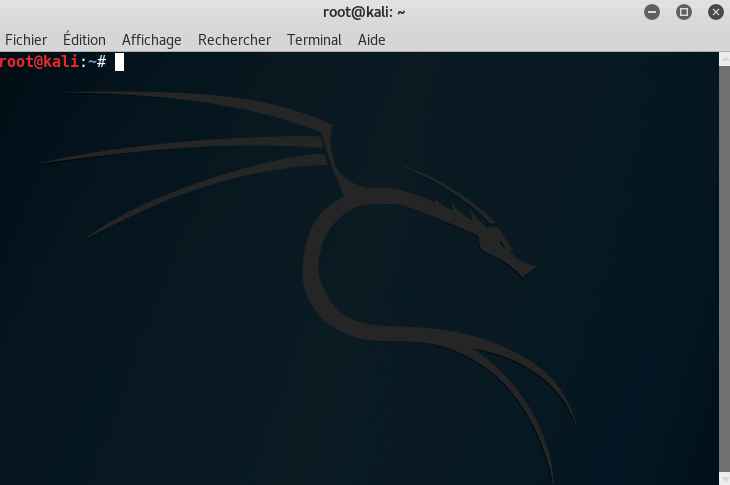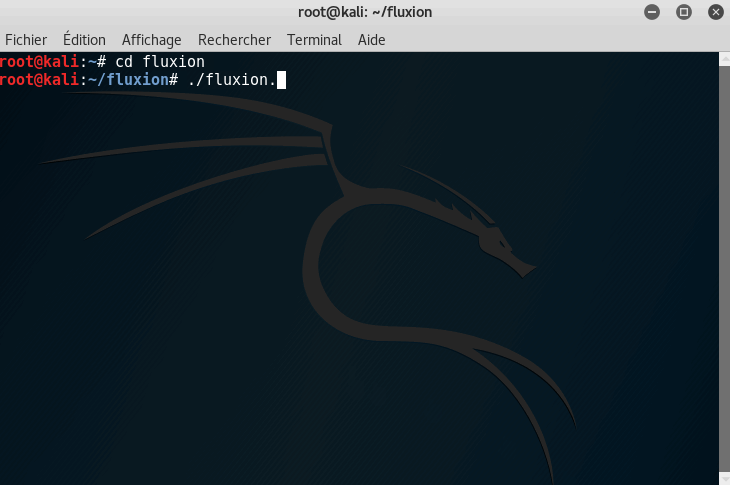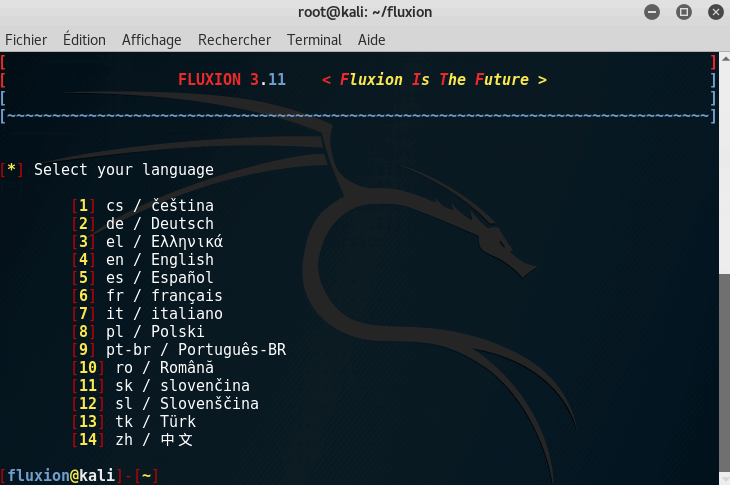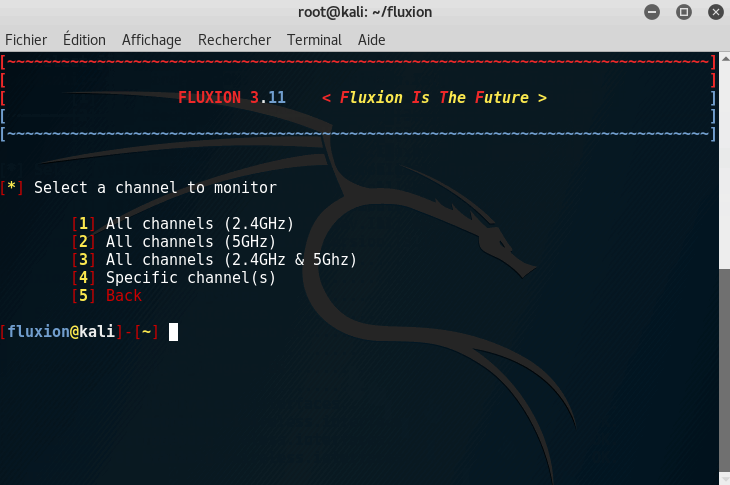
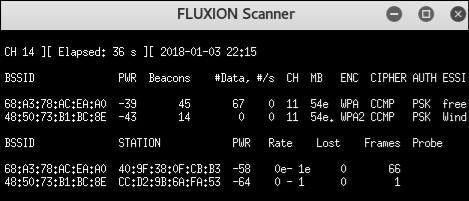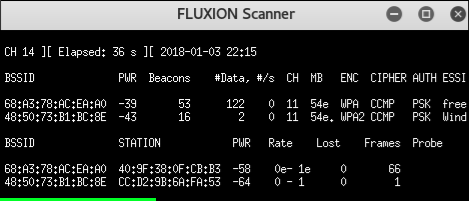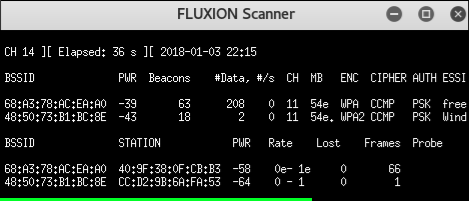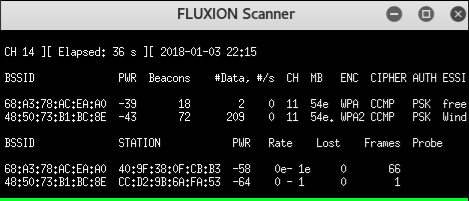
It is now time to scan every network around you. We are going to use your device to listen to all networks passively.
I highly recommend you to choose 2.4GHz; it has a more extended range, and it is more used than the 5GHz.
Wait at least 5 seconds when you see your desired target. When you are done, you can close the Fluxion Scanner.
Note: You need to choose a currently active network.
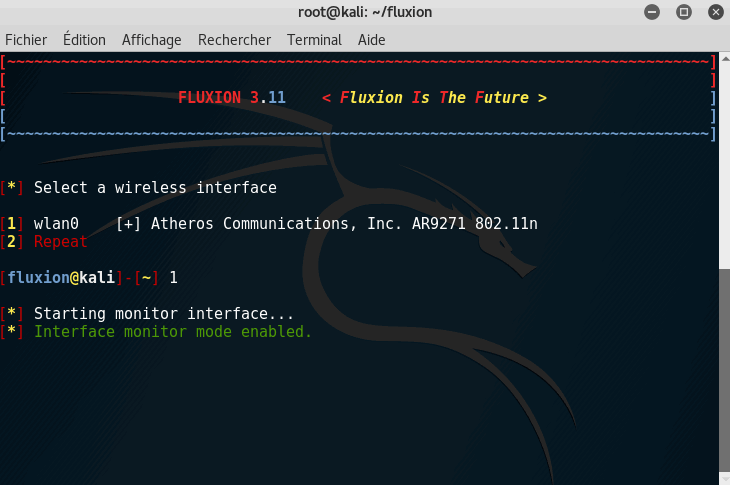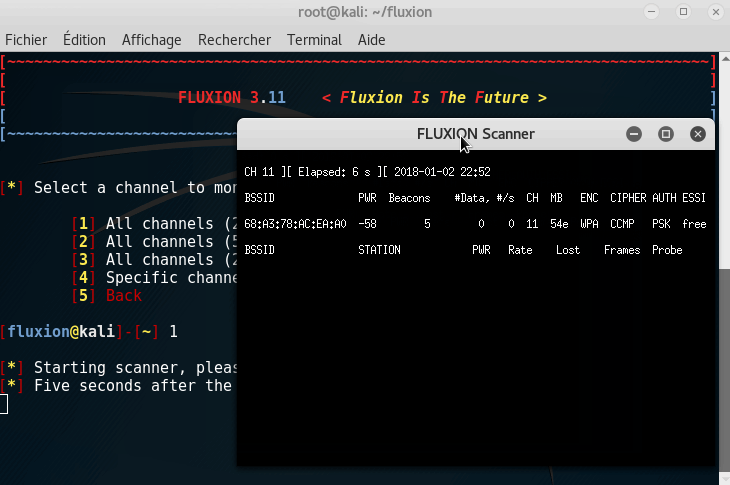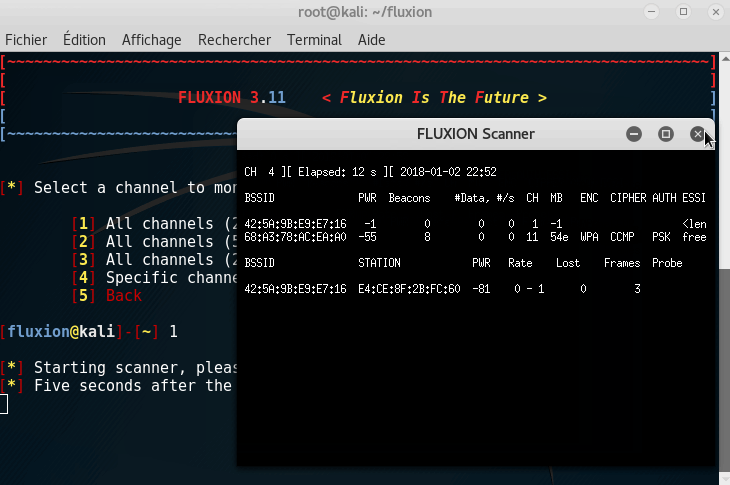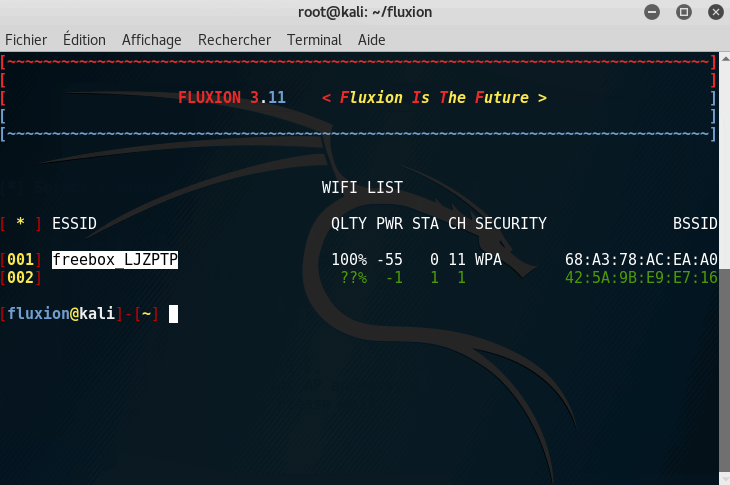
Tip: Your target needs a high QLTY(Quality) score. This point is crucial because, after the attack, your target devices automatically reconnect to the more powerful access point.
Tip-bis: Want to know if there is currently someone active on the network? Check the Beacons and the Data: if they are moving, that means someone is currently using it.
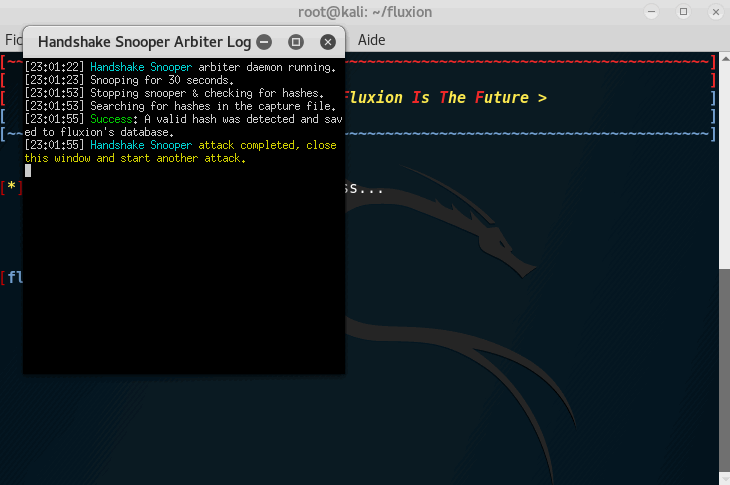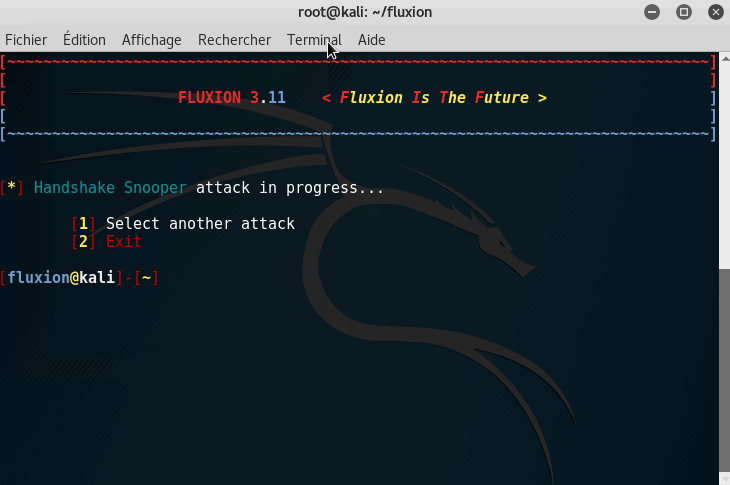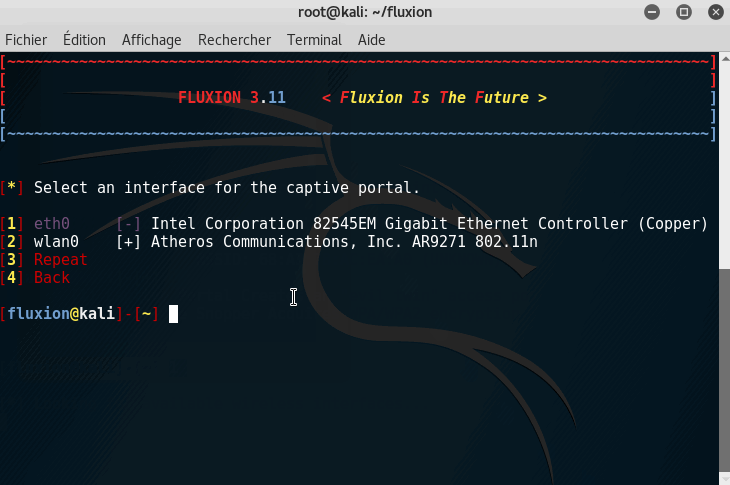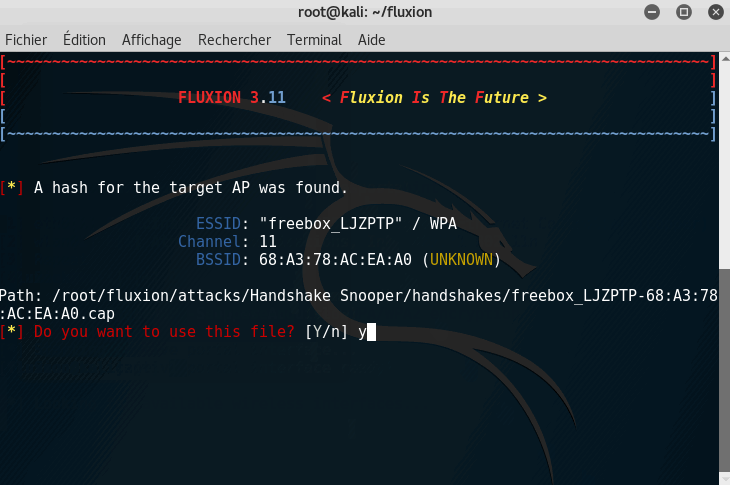
Step 4: Listening for handshake
It is now time to listen for a handshake; to make it short, every time someone connects to the network, there is an SSL verification to check if the user is already registered to the network. We need to capture this handshake.
To do that, select the following options:
1. Choose your network target
2. Handshake Snopper
3. Monitor
4. Pyrit Verification
5. Every 30 seconds
6. Synchronously
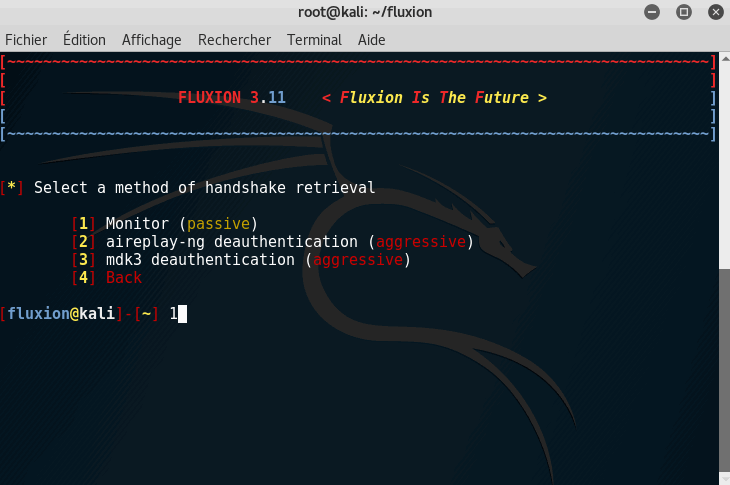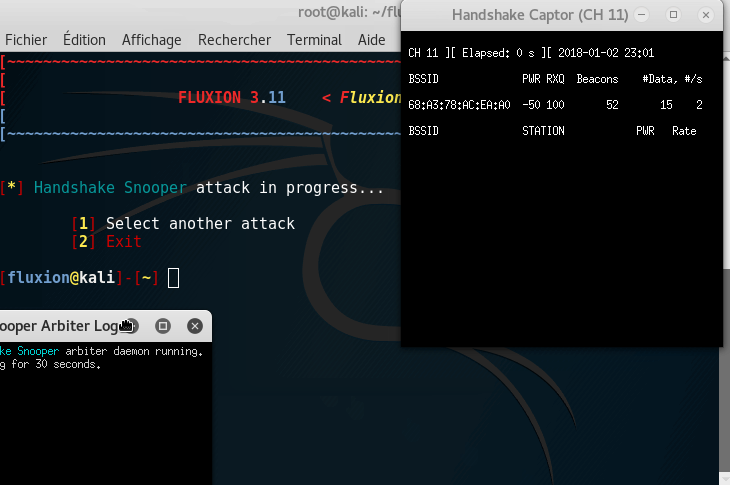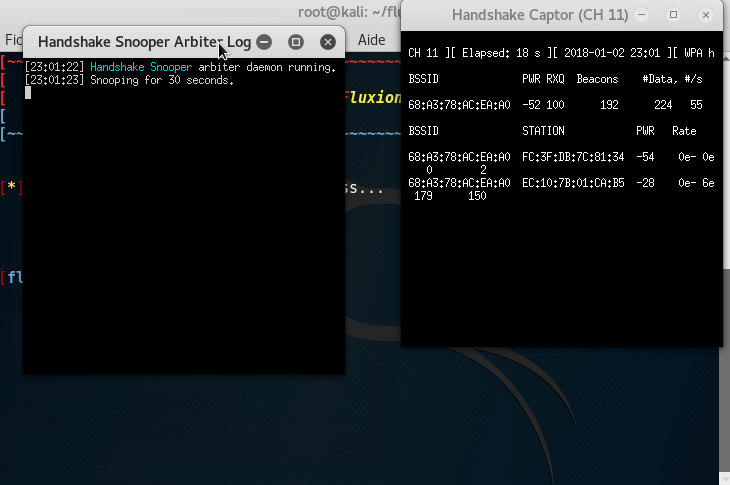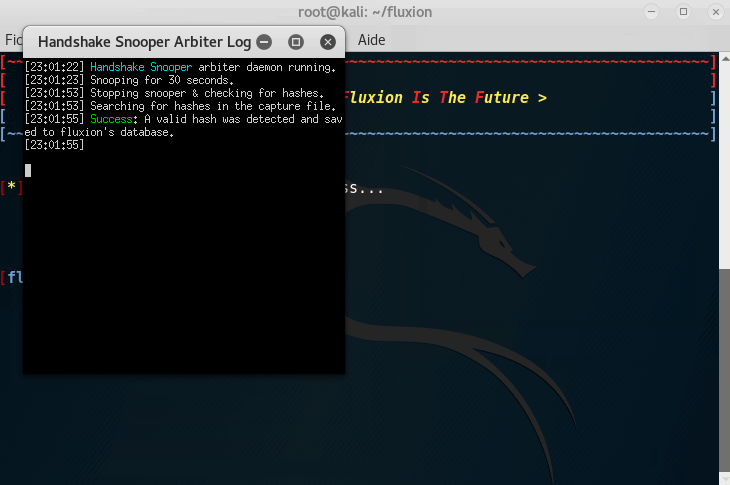
Tip: If you are trying this at home, try to disconnect one of your device (Your phone for example) and reconnect it to the Wifi.
Step 5: Create a captive portal
A captive portal is a phishing method to retrieve the WPA/WPA2 key. It shows a webpage, very similar to the ISP of the targeted network, asking for the key.
1. Select another attack
2. Captive portal
3. WLAN0
4. Rogue AP - hostapd
Step 6: Create the evil twin
This is the final step. We are going to create the evil twin, and try to force any devices to connect to this fake access point. When a new device is connected, every DNS requests are redirected to the previously configured captive portal.
1. Yes
2. Pyrit verification
3. Create SSL certificate
4. Disconnect
5. Choose an option from the list
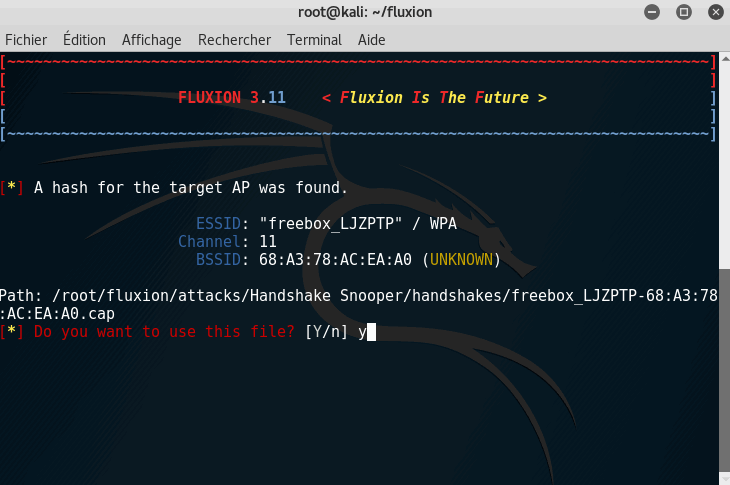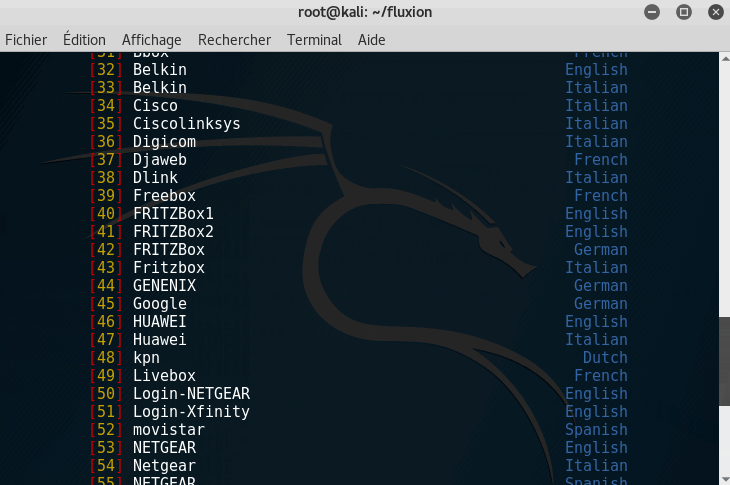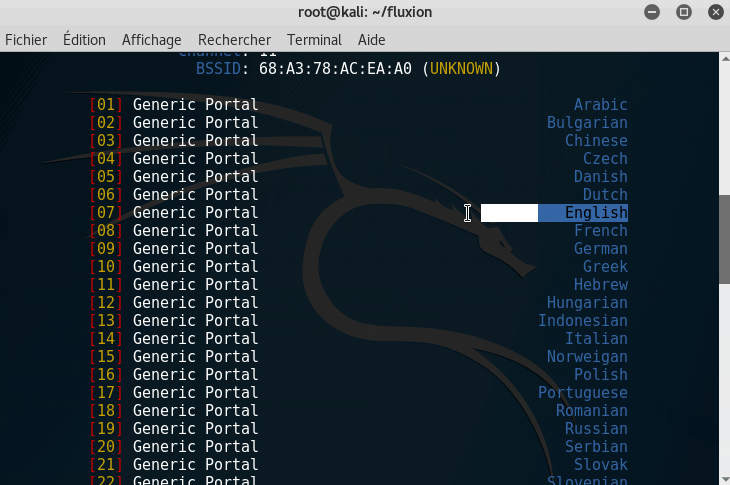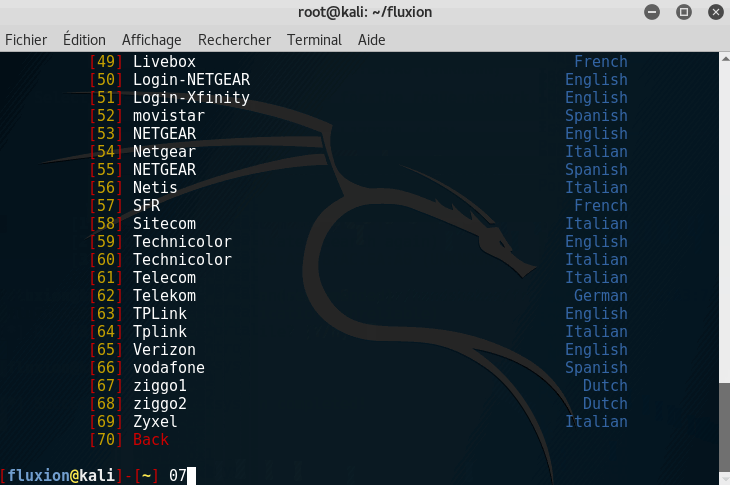
Again, this step required some patience. Let times for the devices to reconnect to your access point.
Step 7: Getting the key
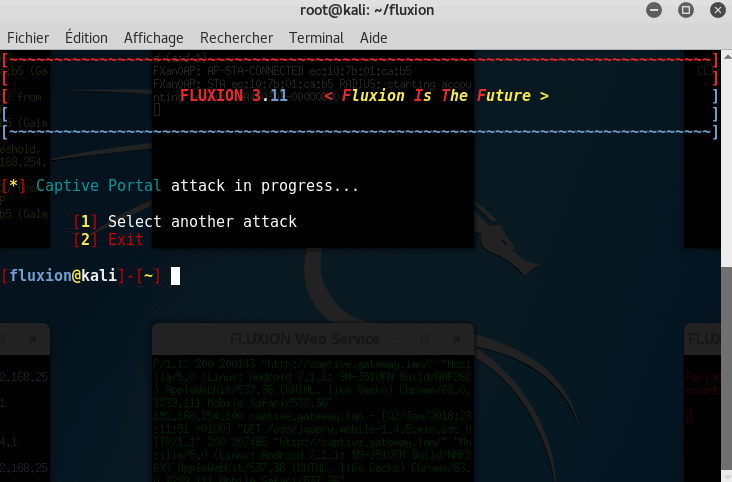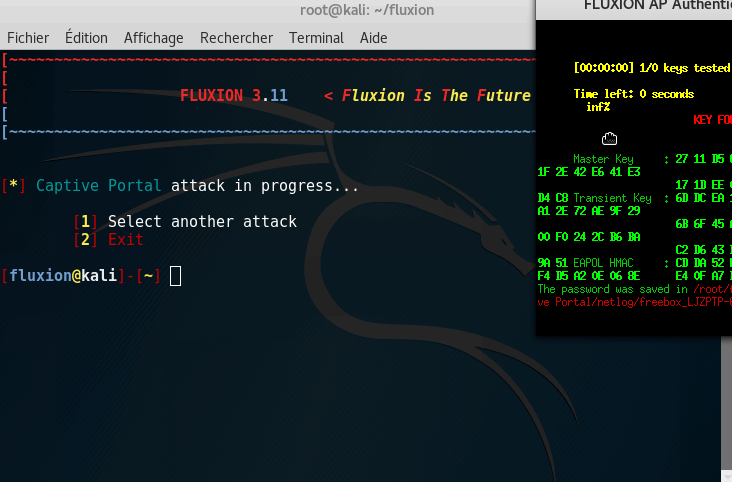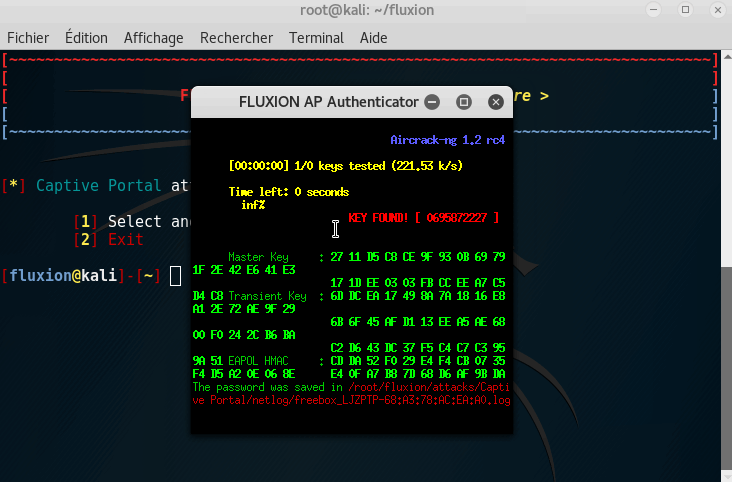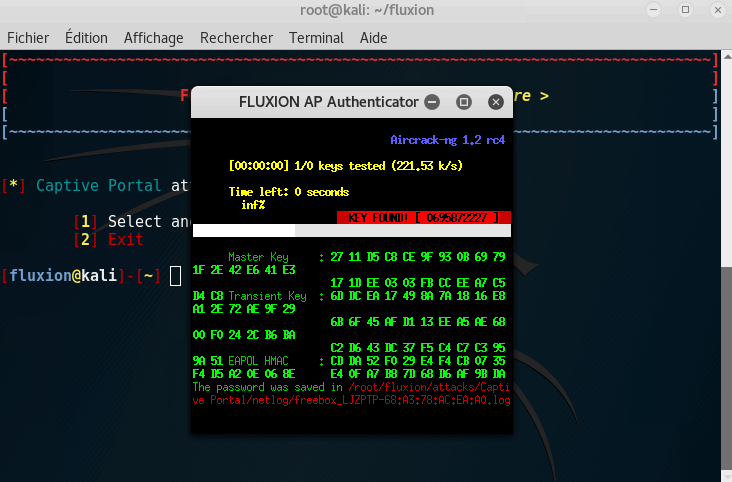
If you get the key, **Congratulations **on following this tutorial, you were able to retrieve the key!
If you don't, Keep in mind that you will not get the key every time. This is a phishing method. But if you set up every right, and if the power of your Wifi adapter is enough, this is probably the best way to get a WPA/WPA2 key.
# Important notice regarding this tutorial:
Using this tutorial on networks that you do not personally own is illegal. Unless you have the consent of the targeted network, you should NOT use Fluxion.
NOTES:
(1) What is a Man-in-the-Middle Attack and How Can You Prevent It? - https://www.globalsign.com/en/blog/what-is-a-man-in-the-middle-attack/
(2) What is evil twin? - http://searchsecurity.techtarget.com/definition/evil-twin
(3) Definition of a Captive Portal - http://searchmobilecomputing.techtarget.com/definition/captive-portal
Posted on Utopian.io - Rewarding Open Source Contributors
Thank you for the contribution. It has been approved.
You can contact us on Discord.
[utopian-moderator]
Thanks @shreyasgune ! Any personnal suggestions to improve my future Tutorials ? :)
Hey @folken I am @utopian-io. I have just upvoted you!
Achievements
Suggestions
Get Noticed!
Community-Driven Witness!
I am the first and only Steem Community-Driven Witness. Participate on Discord. Lets GROW TOGETHER!
Up-vote this comment to grow my power and help Open Source contributions like this one. Want to chat? Join me on Discord https://discord.gg/Pc8HG9x