Learn Cryptography #1 - Hashing vs Encryption
Hey Guys!!....
In this tutorial series, we will be learning various Cryptography related concepts - both basic and core through examples.
The cryptography plays a major role in many day-to-day applications like Chat (Messaging) Apps, Password stored in database, Fetching the secure website i.e. HTTPS, etc. In many cases, we don't see the layer behind. It's actually cryptography used.
Now a days, we are seeing a lot of cryptocurrencies - Bitcoin, Ethereum, Litecoin, etc. In all these, the entire blockchain protocol (Mining algorithms) used is constructed using cryptography majorly. So, it's high time that we start learning this subject.
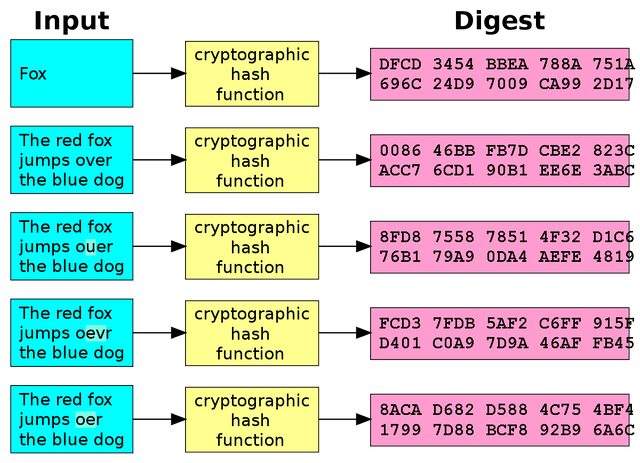
Hashing
Concept -
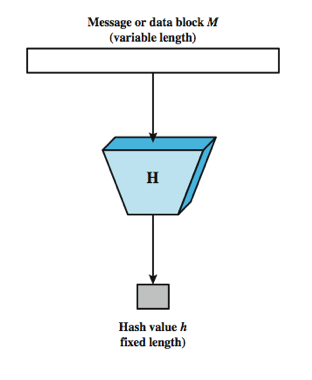
It is a technique of passing an input string (any size) into a "Hash Function" and generating a unique hash number (fixed length) out of it.
E.g. of hash function - MD5, SHA-1, SHA-2 (mostly used), etc.
Application -
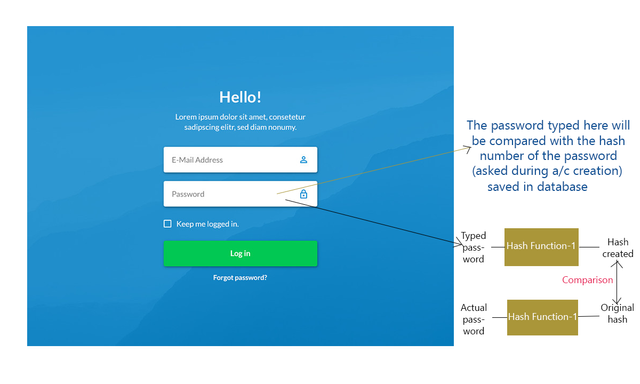
While storing password in database - when user makes login attempt, the entered password is compared with the stored password (hash numbers compared in this case).
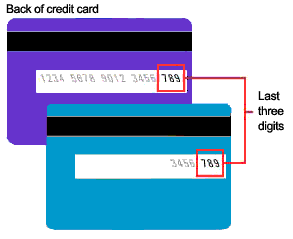
While entering the Credit card details, the last digits are compared with the stored credit card in the database.
NOTE: Basically, whenever we want to save any plain text in hidden form, we can use Hashing for that purpose.
Encryption
Concept -
A technique where an input is converted into an unreadable output of any length.
Here, the input is retrievable through decryption using key.
Types- Symmetric & Assymetric.
Symmetric - The keys for encryption and decryption.
Assymetric - 2 different keys. Public key for encryption and Private key for decryption.
Application -
It is used where any information is supposed to be retrieved by the receiver.
- In Chat applications, the messages sent are to be read by the receiver. In this case, if Hashing used, it is of no use because the user won't be able to understand the text due to it's property of one-way (irreversible).
In this, any message before sending is encrypted by sender using his public-key and the receiver retrieves the message and decrypts it using sender's private-key. Like this, the chat applications work in the behind.
Difference
Hashing - non-retrievable input, used for storing and comparison.
Encryption - retrievable input, used where the input is to be read by the receiver e.g. Chat Apps.
That's all.
View in Github
Stay tuned for the next tutorial.
A series on "Cryptography Programming with Python" is on the way.
Thanks for reading....
Posted on Utopian.io - Rewarding Open Source Contributors

good post @bijoy123
Your contribution cannot be approved yet because it is attached to the wrong repository. Please edit your contribution and fix the repository to reapply for approval.
Explanation:
So please try to improve your post, and when you feel ready, reply to this comment, so I can review again. As a Utopian Moderator I must follow the rules. Check https://utopian.io/rules before posting and make sure your contribution meets all criteria.
You can contact us on Discord.
[utopian-moderator]
Your contribution cannot be approved because it does not follow the Utopian Rules.
You can contact us on Discord.
[utopian-moderator]