Uncloak: Innovative Approach to Cyber Security Solution
Introduction
The importance of a quality cyber security solution can never be overemphasized. Businesses rely more and more on the internet everyday. In fact, a few minutes without internet connection could have a negative impact on a business. Some of these threats are capable of shutting down a business for months before being neutralized. As a result, the role of cyber solutions for combating attacks become even more vital.
Existing Cyber Solutions Are Flawed
Over the past years, many businesses have come under cyber attacks. Some of these attacks have resulted into considerable economic losses to affected companies and eventual erosion of reputation.
The commonest factors responsible for major breaches could be grouped into 2 broad categories: human and hygiene.
While the human factor is associated with how employees use expert systems, cyber hygiene relates to how companies keep their systems secured and updated. Each of these categories involves mistakes, negligence, and several bad practices that contribute to security breaches.
Another risk factor is that many companies leave their source codes exposed to hacking. As an illustration, the infamous Yahoo data breach of 2013 is a classic example of what can occur when a company's source code is left unguarded.
Yahoo utilized a very weak algorithm for generating cookies which made it quite easy for hackers to predict the correct value of cookies assigned to users. Bad guys simply created new cookies to bypass Yahoo cyber security and pose as real users. This allowed them to acquire valuable information from unsuspecting clients.
Also, passwords protected cyber systems are highly vulnerable. These passwords could be detected by simply using any ingenious hacking schemes like key logging, phishing, sniffing, brute force, cracking of hashes, educated guesswork, or by bypassing
In another scenario, continuing using a default password is a major factor behind countless DDoS attacks. Mirai malware in 2016 exploited the tendency for users not to change default passwords on their systems.
This risk will increase as more systems interconnected with the Internet of Things (IoT) enter our businesses and homes.
Again, current cyber security are mostly configured to combat threats after attacks might have been launched. This approach suits hackers with their criminal mindsets. The fact is that damage caused by attacks can only be repaired but can never be forgotten and businesses remain the loser for it.
Besides, hackers are known to share hacking codes and collaborate to launch massive cyber attacks on targeted systems or websites. On the other hand, cyber security experts mostly work in isolation and develop virtually untested systems which have flaws that could easily exploited by those outside their working group.
No Company is Immune to Cyber Attacks
Sony's PlayStation Network, Staples, Home Depot, JPMorgan Chase, Michaels Stores, Target, Yahoo, eBay, and Uber are some of the notable companies that have fallen victim to cyber attacks in recent years. These security breaches resulted into unimaginable economic losses to businesses and users alike. In the Sony case, 77 million accounts were reported hacked and an estimated $171 million lost to the attack. This is despite the fact that Sony spends millions on its cyber security architecture and IT personnel.
Small business are even more vulnerable to attacks and hundreds of these experience such threats every blessed day.
The main reason behind this pervasiveness of cyber threats is that existing cyber security systems are incapable of detecting cyber threats before being launched. According to an FBI expert group, 90% of cyber attacks could be prevented if detected in real time. With this revelation, we can conclude that early detection is the only way by which cyber threats can be curbed effectively.
Blockchain Technology is the New Innovation in Cyber Security
As we all know, combating cyber breaches requires more than deploying firewalls and antivirus protection. If those things work, we wont be seeing more and more cyber attacks every day.
Furthermore, current cyber security solutions rely on custom-made techniques with little knowledge sharing among security companies. On their own, hackers freely share resources and expertise with one another and this enable them to be always one step ahead of security experts in the grueling duel.
Fortunately, blockchain is a highly secure, scalable and decentralized technology capable of being used to build expert security systems based on smart contracts which are well ahead of existing knowledge of cyber criminals. Unlike old cyber security systems, blockchain could be used to detect cyber threats ahead of time.
This is what prompted some tech gurus to develop an innovative cyber security tool like Uncloak.
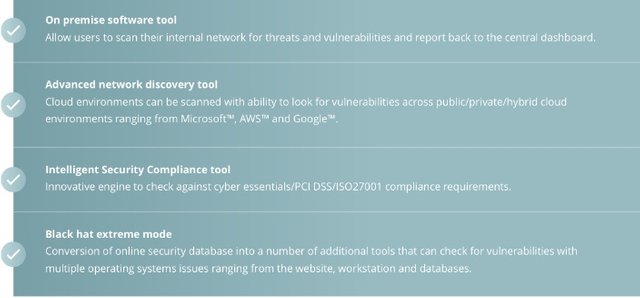
Launched in late 2016, Uncloak is a security solution that confers businesses with the power to monitor, detect, and eliminate cyber threats before being launched. With it, a business can effectively neutralize potential threats directly without depending on expensive 3rd party solutions.
The edge that Uncloak has over other cyber security tools is its approach of decentralizing blockchain based security solution. Invariably, this aggregates the knowledge of the entire community into a single system that transforms it into service for all users.
Moreover, Uncloak uses new generation Artificial Intelligence (AI) technology that scours the web looking for cyber threats and converting these into recognizable signatures which can be detected by end-users immediately. If the threats are innocuous, the information is discarded. By so doing, users will be fully in control of cyber security and thus always ahead of criminal elements.
Uncloak isn't designed to respond to threats after attacks might have been initiated. It's rather configured for early detection of cyber threats and this makes it a viable alternative for existing cyber security solutions. Indeed, Uncloak is a step forward towards achieving a threat-free cyber environment.
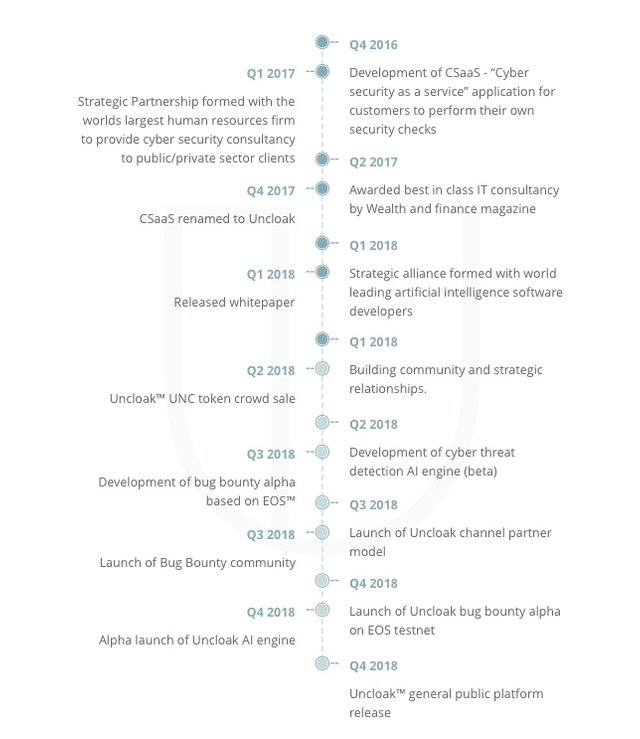
Roadmap
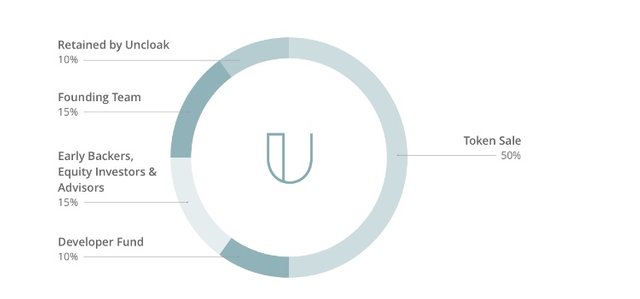
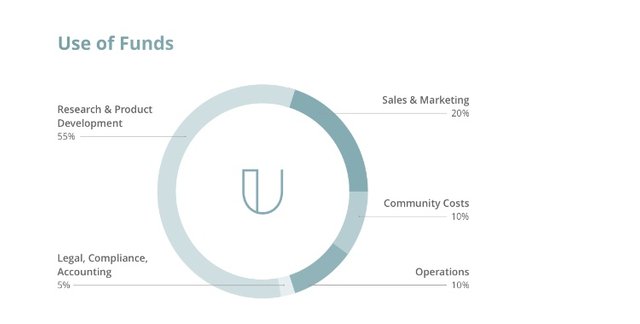
ICO OVERVIEW AND TOKEN DISTRIBUTION
TOKEN SALE: 25TH SEP – 2ND OCT
TICKER : UNC
TOKEN TYPE: ERC20
TOKEN PRICE: 1 UNC = 0.01 USD
FUNDRAISING GOAL : 21,000,000 USD
TOTAL TOKENS: 4,200,000,000
AVAILABLE FOR TOKEN SALE: 50%
Questions or enquiries regarding the Uncloak platform are welcomed from our esteemed readers.
A single article isn't enough to cover everything about this innovative cyber security tool called uncloak. However, if you desire to know more about it , feel free to contact any one of the company representatives through any of the following links listed below.
SOCIAL LINKS


As a software developer I would love to collaborate with uncloak in discovering a lot of cyber threat vulnerabilities, and get paid in their tokens.
The cost of cybercrime damages has been predicted to increase yearly, if uncloak doesn’t solve this issue on time, so many companies would suffer losses and may shut down.
Are there competitiors in this field ?
Yes competitiors such as polyswarm, Qualys and Tenable but uncloak would stand out as it’s aimed at taking a proactive approach to tackling cyber security threats on all fronts, rather than relying on a reactive solution.
Uncloak is a really solid project that has the power to shape the future. Am glad to be an early supporter of this promising project.
What is testnet and mainnet?
Testnet was initially scheduled for Q4 2018 but is now likely to be brought forward to Q3 2018. Main-net will be Q4 2018.
Just joined telegram adding it to the list of projects on my radar to watch out for, glad I saw this project before the end of the ICO.
So much money and information has been lost to hackers, it’s glad to know uncloak is providing a means to curtail this issues
How come there’s no github codebase that can be viewed?
All code is private and not publicly available.
My Business website has been attacked a lot of times by hackers, ill love to implement Uncloak’s cyber security vulnerability scanning system, so as to be able to know the present security weaknesses that are on our computers and networking equipment.
Does uncloak have an MVP?
Uncloak already has spent one year developing an MVP which is available as a demo right now.