iptables in great details (with examples, pictures and a video)
When you are trying to run a new server in operation mode, one of the first priorities is security.
A lot of companies bring up the level of security by spending big money on different hardware and software. that is completely fine and even necessary, But what if you want another layer of security (you cannot be too careful after all) or your company is not that big and does not have a place for such expenses? In this case you wouldn't have that much options, would you?
If your OS is Linux then do not worry about expenses or having another layer of security because Linux has taken care of this by a powerful tool which is called iptables.
What is iptables anyway?
Generally you can look at iptables as a firewall that by considering some built-in or user-defined rules and chains, is going to ACCEPT, DROP, FORWARD, etc… the traffic.
This part is the description for iptables when you open the manual page
Iptables is used to set up, maintain, and inspect the tables of IP packet filter rules in the Linux kernel.
before getting to details lets see how we can stop/start iptables
ubuntu(Debian based)
CentOS(redhat based)
service iptables /stop/start/status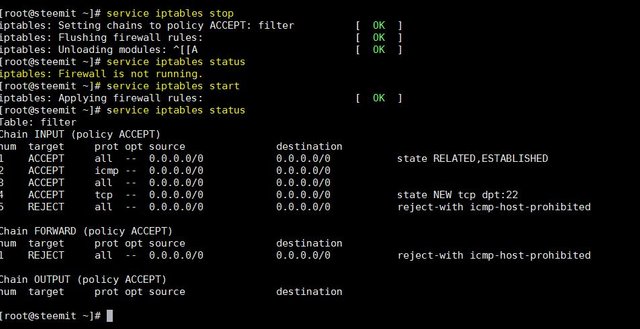
Iptables contain different tables, chains targets, options and other different parameters
by the way if you found this post by searching internet, gotta say you have been lucky, read about Steemit too(our wonderful community : ) )
Tables
You can specify the table in your command by the option –t
iptables -t tablename
Filter
The default table in iptables is which contains different chains such OUTPUT (can be used to control locally generated traffic), INPUT (incoming traffic) or FORWARD (traffic that is supposed to be routed).
NAT
This table is used when you want to NAT a packet through network, it is divided to three part
- PREROUTING: for altering packet the moment they come in
- OUTPUT: altering packets before leaving the host
- POSTROUTING: for altering packets that are about to leave the host
We have two other tables two, mangle (to change the packets) and raw, use of them is not that common and I am going to omit them at the moment.
Targets
To simplify it targets are actions that are going to happen to the packet, they can be user-defined or standard targets as following:
ACCEPT: as obvious as the name is, ACCEPT lets the packet through.
DROP: will drop the packet and does not let it to pass the server (out or on).
QUEUE: will ne send to userspace, handling packets in userspace differ related to Linux kernel.
RETURN: means stop going down the iptables rules and resume at the next rule in previous chain (I myself don’t use it, sometimes does not work as you expect).
REJECT: Reject the packet and notify the sender
LOG: Log the packet, and continue processing more rules in this chain.
you can use --log-prefix and --log-level options with LOG target.
Options
-S
To list all the active iptables rules by specification
sudo iptables –S
To limit the output of a specific chain
sudo iptables –S INPUT
-L & -Z
To list all the active iptables rules by table
sudo iptables –L
Target: what happens to packet.
Prot: protocol (tcp, icmp…)
Opt: IP options (not common)
Source: source IP or source subnet of packet
Destination: destination IP or destination subnet
Last column which has no name is for other rules and specifications that are not listed to the previous columns like connection state etc…
You also can use the option –v to get the number of packets that match the rules, and –Z to clear the counter for all or a specific chain by name of the chain or number of the rule
sudo iptables –L -v
sudo iptables –Z INPUT 1
-A & -D
You can use –A to append a rule to iptables (don’t worry about other options)
Sudo iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 235 -j ACCEPT
To delete a specific rule simply run the iptables –S command and use the output and option –D to delete desired rule
I want to delete access to port 235(by iptables –S you can see it in the picture)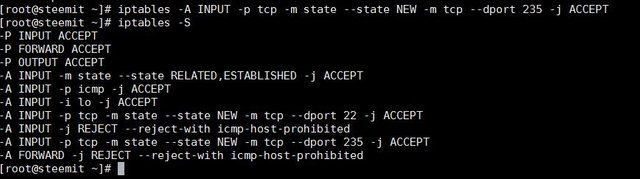
Now simply I run this command
Sudo iptables -D INPUT -p tcp -m state --state NEW -m tcp --dport 235 -j ACCEPT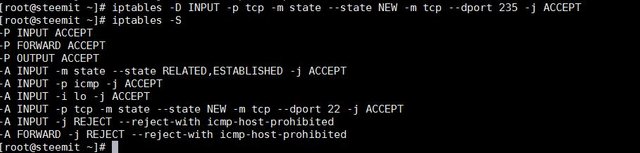
as you see the rule that ACCEPT port 235 is gone now.
-I
takes two options as chain and number that the rule should sit on
sudo iptables -I INPUT 7 -m limit --limit 1/min -p tcp --dport 240 -j ACCEPT
-R
to replace a rule with another(here I am replacing rule number 6 in INPUT chain from port 235 to port 236
sudo iptables -R INPUT 6 -p tcp -m state --state NEW -m tcp --dport 236 -j ACCEPT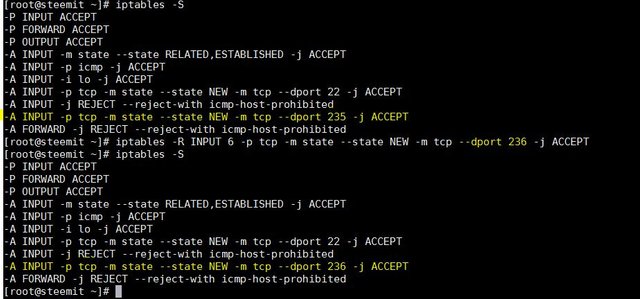
-m state --state
allows to add rules based on connection states like(NEW, RELATED, ESTABLISHED, INVALID)
INVALID: The traffic couldn't be identified.
RELATED: The connection is new, but related to another connection that is already permitted.
NEW: a new connection.
ESTABLISHED : already established.
-m limit --limit
allows the rules just for a limit time(default is 3 hours)
-p
specify the protocol used
--dport
specifying destination port which you want to set the rule
-j
jump to specific target (ACCEPT, DROP, ...)
-i
specifying the interface
-s & -d
setting the -s source and -d destination
to save your config(not loosing them after reboot.etc...) you should use following command
Ubuntu
sudo sh -c "iptables-save > /etc/iptables.rules"
CentOS
/sbin/service iptables save
or
iptables-save > /etc/sysconfig/iptables
remember by using 'man iptables' you can see the list of all commands, options,tables,parameters, etc ...
here you can see a very short demonstration about opening a port on the server
what I provided for you is only the introduction to iptables tool, there is a lot more into it .although if you want to set a basic configuration(yet powerful firewall)for your server, you are good to go.
if you liked this post please up-vote and possibly re-steem it, or even make me feel great by following me at @meysam :)
This post is powered up 100%
Let’s bring our knowledge to the community where anyone can find anything they desire
have fun :)
Tue Jan 10 17:09:41 IRST 2017
Hello @meysam,
Congratulations! Your post has been chosen by the communities of SteemTrail as one of our top picks today.
Also, as a selection for being a top pick today, you have been awarded a TRAIL token for your participation on our innovative platform...STEEM.
Please visit SteemTrail to get instructions on how to claim your TRAIL token today.
If you wish to learn more about receiving additional TRAIL tokens and SteemTrail, stop by and chat with us.
Happy TRAIL!