Web Penetration Testing: SQL and SQL Injection Basics on Kali Linux.
Hello everybody and welcome back to another tutorial in Web penetration testing.
If you will enjoy reading and contributing to the discussion for this post, will you please join us on the YouTube video above and leave a comment there because I read and respond to most comments on YouTube?
If you find anything helpful in this video or funny, will you please leave a like because you will feel great helping other people find it?
Right now we will start off by covering some of the basics of SQL and the basics of SQL injection.
So, first of all, for those of you who don’t know, with the SQL injection we basically make an interaction with the database itself.
Now, the database is mostly used to store information. For example, usernames and passwords can be stored in a database and once you type them in a form the server queries the database and compares the password you typed in with the password stored in the database and if they match it will allow you to log in.
So an example would be, for any login form that you encounter, whether it is on Instagram, Twitter or any social media account, what it will do is once you type in your password, first of all it will probably hash your password and compare the hash password with the hash password stored in the database and if they match you will be able to log in.
So the problem here happens if the person who created that website didn’t filter the user input well enough and didn’t forbid some of the characters used to query the database.
Now, it can potentially allow the user to send SQL queries and gather a bunch of the information that he shouldn’t really gather.
It can also allow the user to delete the entire database if he wanted to.
Now, before we begin let me just open Leafpad right here and explain a little bit more what SQL is and how you query the database.
First of all, the database is just a bunch of tables that are connected with the same system and that are also connected between each other.
Now, what I mean by tables is basically, a table is a list that contains information for the same type of elements, for example, table of users.
So facebook.com, for example, probably has a database with a bunch of tables of users and those tables are basically consisted of rows and columns.
So for example, you could have the row of users and below a row of passwords for the users then below a row of some of the other information for users such as mobile phone, email or basically any other information you want. It doesn’t have to be anything linked with the user itself.
It could be, for example, you visit an online shop and it sells flowers, for example, and you could have a table of different types of flowers right there and different types of information for those flowers.
Once you search the online shop, it queries for that database.
Now, how do we query a database? How do we actually interact with the database itself?
Now, there is the SQL language. It is not that hard to learn, but in the SQL injection it might seem a little tricky to get used to it. But once you learn some of the basic commands it is not that hard to continue learning it.
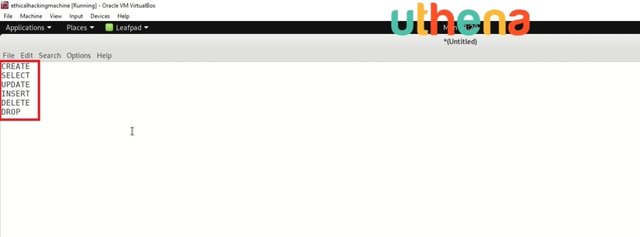
Now, some of the top commands could be CREATE, SELECT, UPDATE, INSERT, DELETE, and DROP.
Now, these commands are used to query the database and they basically do as they say.
‘Create’ will create database.
‘Select’ will select a specific table in that database or specific column or row.
‘Update’ will basically update the database.
‘Insert’ will insert a new element to the database or to the table itself.
‘Delete’ will delete a certain part of the database. For example, you want to delete a user. He decided to, for example, close the account and you want to delete it from the database. You will do it with the delete command.
‘Drop’ basically deletes the entire database itself. It can be very dangerous if the site is vulnerable to the SQL injection. So for example, let’s say that Facebook was vulnerable to the SQL injection and you just type ‘drop’ and the name of the database, you would basically delete the entire database of users and passwords.
That would become a really big problem, but luckily Facebook is not vulnerable to SQL injection and most of the bigger websites aren’t vulnerable to SQL injection either. But some of the less known websites could be.
So, one more thing. The commands ‘delete’ and ‘drop’ are not really used that much by the attacker since loss of information is not a preferred method of the attack itself since the attacker in most cases wants to gather information and not delete them.
Now, put yourself in the shoes of the attacker. What is valuable to the attacker is the passwords and usernames that he could gather for that account rather than deleting every account.
If he deleted every account he would just create a big problem. But if he gathered all usernames and passwords, he could basically log in as anybody to that website.
That could present a huge problem if that website was for example, PayPal.
He could send bunch of money to himself and he would probably get caught after some time, but that isn’t the point right here.
Now, the command out of all of these that you will use always is the ‘select’ command.
So this command is used to query the database. So for example, if you found a website that is vulnerable to SQL injection, you want to select the table with the passwords. You will do that with this command.
Read more on my website at https://jerrybanfield.com/sql-injection-kali-linux/
Love,
Jerry Banfield
https://jerrybanfield.com/
https://jerrybanfield.com/blog/
https://jerrybanfield.com/books/
https://jerrybanfield.com/contact/
https://jerrybanfield.com/freecourses/
https://jerrybanfield.com/masterclass/
https://jerrybanfield.com/partners/
https://jerrybanfield.com/podcast/
https://jerrybanfield.com/resources/
https://jerrybanfield.com/steem/
https://jerrybanfield.com/twitch2019/
https://jerrybanfield.com/wirecast/
https://jerrybanfield.com/youtube/
https://jerry.tips/emaillist1017
https://jerry.tips/songsbyme
https://uthena.com
https://www.facebook.com/jbanfield
http://itunes.apple.com/podcast/id915442105
https://www.patreon.com/jerrybanfield
https://soundcloud.com/jbanfield
https://teespring.com/stores/jerrybanfield
https://www.twitch.tv/jerrybanfield/
https://twitter.com/JerryBanfield
https://www.youtube.com/jerrybanfield


Thanks for the tips Jerry, this is useful information I will be sure not to overlook, and revisit. I have been using SQLALCHEMY for querying, speaking of querying, that is exactly what I was doing when I saw your post, lol!