For those who want to be a hacker but have no idea where to start
A hands-on post aimed at giving you the exposure and the experience you need to get started.
I’ll guide you through the process of creating a virtual lab and setting up the tools to start hacking away.
Don’t be fooled though, Hacking isn’t all about targets and programs.
There are tools to help you out and boost your speed. but the moment you stop Learning, Discovering and thinking differently, you will become novice again.
So.. Keep at it, understand that at first things may not make much sense. but keep going till you fill all the puzzle holes in your head, through exposure experience and the will to not give up.
Let’s start. You will need to create virtual computers inside your computer or the computers in your network to gather more experience with computer systems and how to break in or secure them to keep people like you out.
"If you are serious about learning then it is the very first thing you
should do.
The reason being is that once you get your lab set up you will be able
to start running sample tests to see how they work. Every Hacker had one, and
reading about how to conduct penetration tests or watch hacking videos won’t get you anywhere… you will actually need to get your hands dirty."
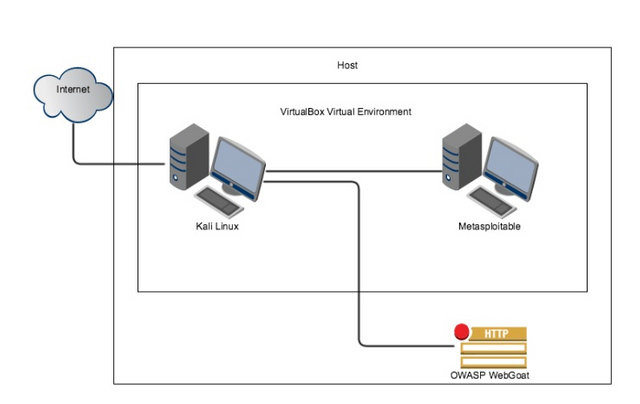
We are going to start with three machines:
-Kali Linux (which will be our attacking platform)
-Metasploitable 2 (a vulnerable Ubuntu Linux operating system)
-OWASP WebGoat. (a vulnerable Web Application with lessons within it)
We want to create a network where we have one platform for penetration testing, one platform that was built to be vulnerable and one web application that was built to be
vulnerable.
Kali Linux if you don’t know is the gold standard open source penetration testing
operating system created by Offensive Security. Operating systems don’t make
the penetration tester, but if you are serious, Kali Linux was developed solely for
this purpose and will make your life a whole lot easier. Many of the tools are built
right into it.
We will end up with something like this. That will suffice for now.
To do that you need to download VirtualBox https://www.virtualbox.org/wiki/Downloads
Kali Linux iso or https://www.kali.org/downloads/
(choose one of the XFCE iso’s whether u have 32 or 64bit windows as XFCE is lighter for your computer.)
Then we need to
Install virtualbox and open it when it’s done to create a virtual machine.
- press the “New” button
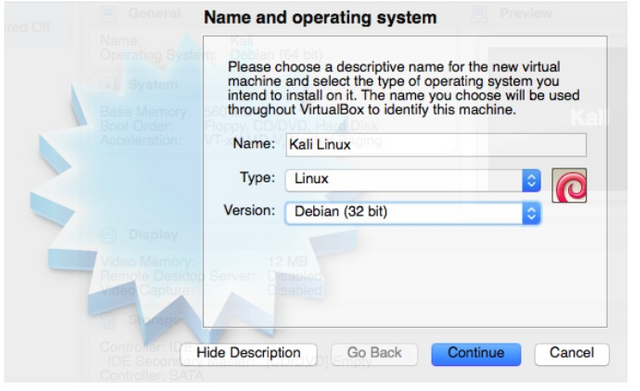
a) Put a name
b) Select Type (Linux in this case)
c) and version as well as architecture (depending on the iso you downloaded) Kali is based on Debian. and We Downloaded the 32 bit version because our CPU and Windows Install are 32bit also.
d) Press “Continue”
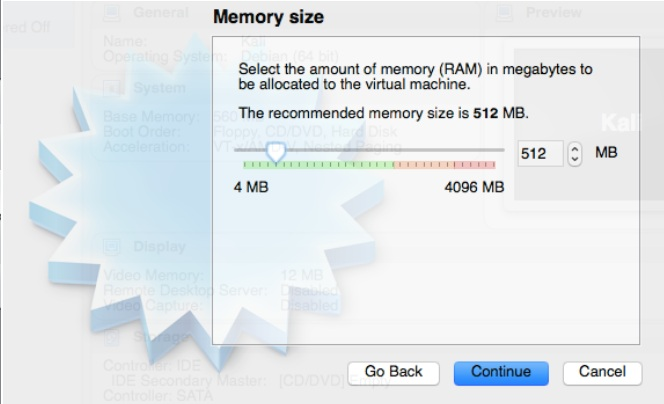
While 512 is the default and you may get away with this, it
is possible that you’ll get into some trouble later running certain applications so I
suggest you increase it to something higher if your computer can afford it, in other words if you have 4GB ram on your computer you could spare 1-2 GB to run our Attacker’s Virtual Machine.
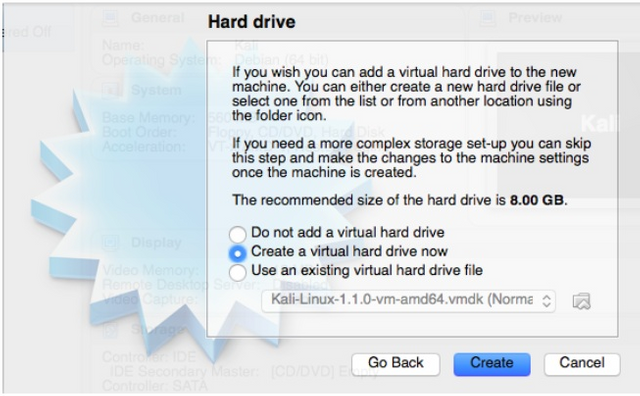
We will be creating a virtual hard drive so select that and click “Create”
For this example we will be using the VirtualBox Disk Image. “Continue”
We want a Dynamically allocated hard drive for this example. “Continue”
For the size you probably want to increase it to at least 15GB Since with 8GB you may encounter problems…
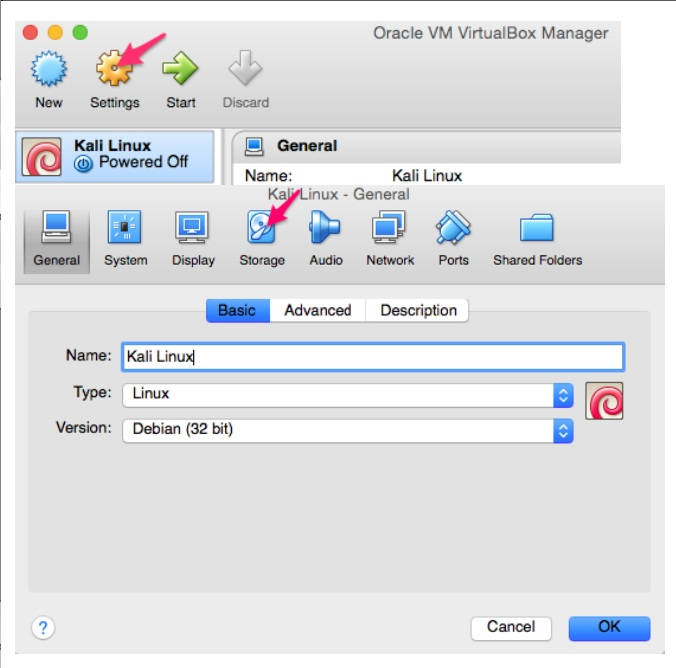
We now need to add the ISO that we previously downloaded. We do that by
highlighting the are
a you see selected below. At first this should say “Empty”.
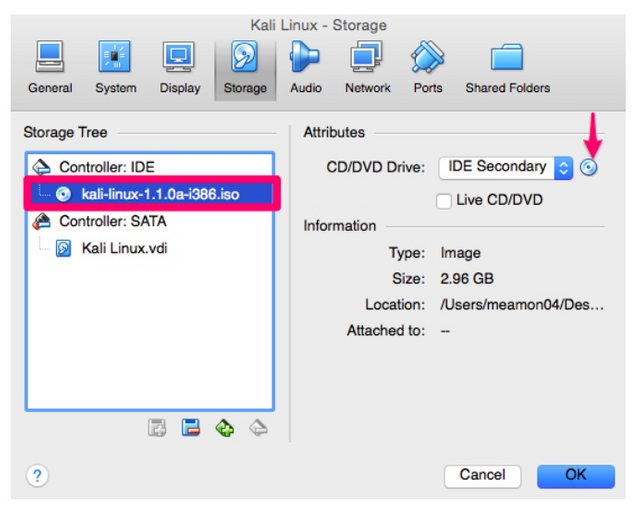
After “Empty” is highlighted you then need to click the CD where you see the
arrow below and browse/select where you have your ISO located.
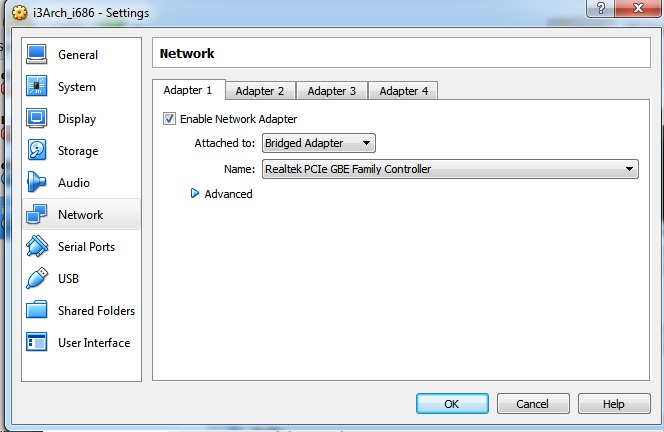
For Network Adapter We will be using Bridged Adapter which makes our virtual machine having its own IP and seemingly physical state on our actual network the one your home router serves.
Doing this to a Vulnerable/Target Virtual Machine might be dangerous. it’s like putting a hackable computer in your network.
For the most part it wont hurt us as we learn tho.
But in the future remember to not attach your targets to your actual network.
Who knows any hacker with access to our network may use them to compromise the rest of the network while we are absent.After that we are ready to start our attacker’s Virtual Machine for the first time.
The Virtual Machine will start booting our iso.
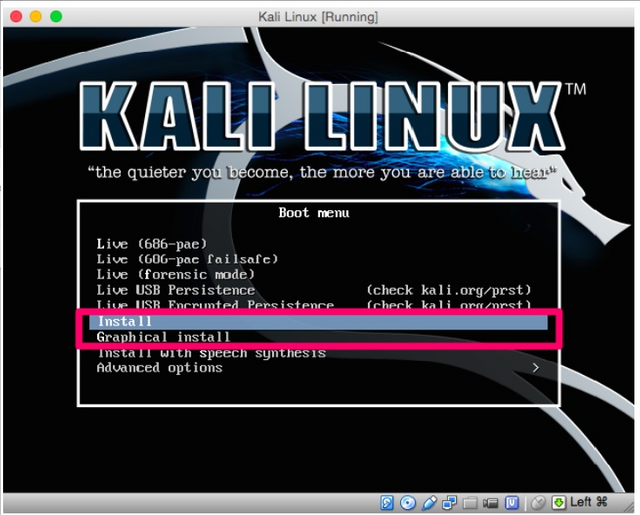
Which gives us some choices. Live will get us to a temporary kali linux install which may let you use its tools but wont save anything to your virtual machine as it rans of cd. any shutdown/reboot attempt will make your data to be lost.
I suggest that you actually install Kali Linux on to the virtual machine. Choose the Install or Graphical Install below and follow the steps.
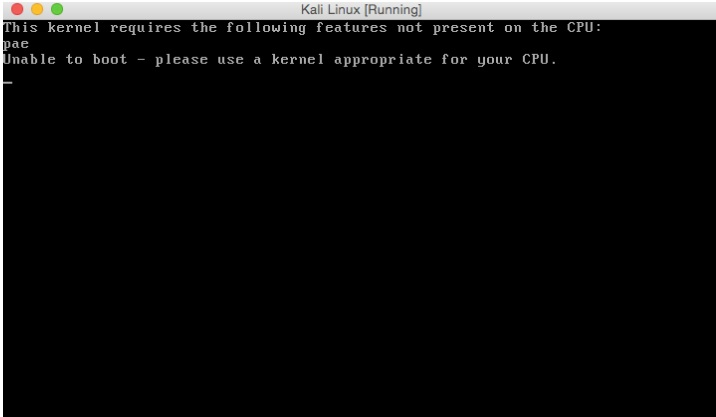
Depending on how you are installing your system and what version of the install
you are using, you may encounter the following error when starting up the install:
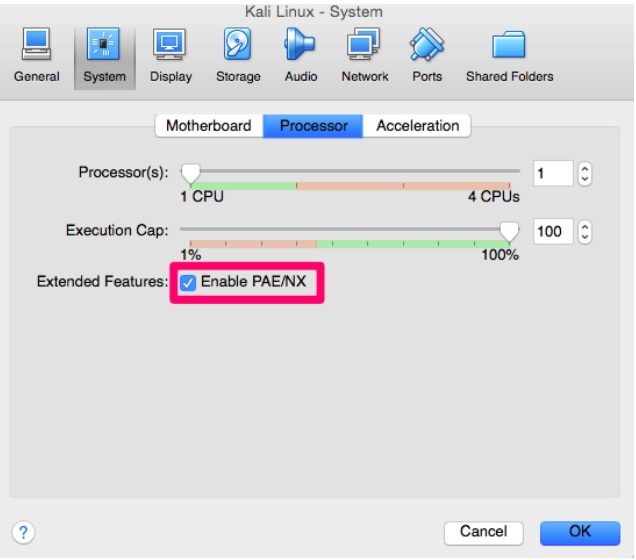
If you get this error go back to settings, System, Processor and select “Enable
PAE/NX”.
After logging into your fresh Kali Linux install the first thing you will want to do
is verify that you can reach the internet by opening up your web browser.
If you cannot browse the web you need to enable DHCP from your command prompt
with: dhclient -v
Now that everything has been set up properly we need to update Kali Linux so
that we KNOW that we have the most recent distribution and tools. You can do
that with the following at the command prompt:
apt-get update && apt-get upgrade
Metasploitable:
To start you will need to download the files from here:
https://information.rapid7.com/metasploitable-download.html
Installing your vulnerable Metasploitable 2 operating system is very similar to
how you installed Kali, just with fewer steps.
Again, create a new virtual machine:
Again, set your memory size.
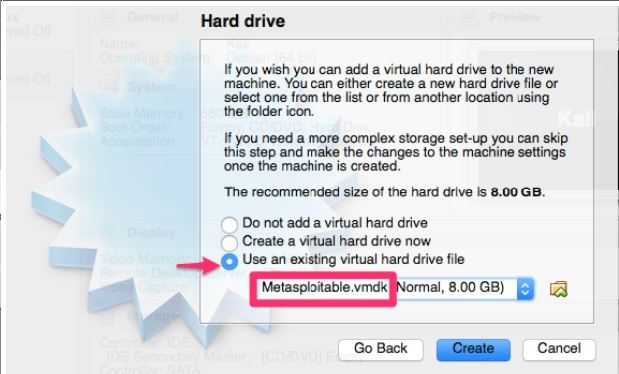
Hard Drive is slightly different than the Kali Linux setup because we will be using an
existing virtual hard drive as you can see below. Just select where you see the
arrow and then browse to where you saved the highlighted file.
|
Like we did for the Kali Linux setup we will need to click on settings once again.
We need to make a modification in the network section as we did for our Kali
Linux platform.
After that…
Start your new Metasploitable 2 virtual machine.
Now For OWASP Broken Web Applications Go to VulnHub a place with a collection of resources to study and virtual machines you can hack. the press Download for OWASP Broken Web Apps. this will give you a zipped file which inside it has a virtual machine.
Try to put it in virtualbox on your own. we Already used virtualbox to create to virtual machines. I believe you have what’s needed and you can create the third one.
https://www.owasp.org/index.php/OWASP_Broken_Web_Applications_Project
If you installed all three of these platforms then you have plenty to get you started
on your journey of learning how to hack in to the information security and
penetration testing space.
This network is now the perfect venue for a student like yourself to test out their
skills and techniques without the fear of permanently damaging or destroying
your own network/systems, or someone else’s for that matter.
I'll try to keep posting content like that. and everyone is welcome to reach out to me for any extra help that might be needed ccya steemians!

Nice post man. I have always wanted to get into pen testing as a bit of a hobby but never had the time to learn and more importantly keep learning.
Well used to be my passion, but last for years (after my first job landing as an ethical hacker) I turned into web development. My country doesn't really pay much for security whereas web development I get more projects for the time being here. anyway you are more than welcome to reach out for just about anything tech..or non-tech :)
Very great post! /applause
Meatsploitable2 is a great starting place for anyone wanting to get introduced to pentesting. http://www.securitytube.net/ has all sorts of video resources to help you learn to tricks.
My advice to anyone practicing with this particular VM:
Once you successfully exploit the machine one way, start over and try to exploit it differently. This vm has plenty of vulnerabilities. Once you get comfortable and understand the concepts a bit better, start trying to automate your exploits.
I'm planning for a write up for more resources in the future like http://www.securitytube.net/ , https://www.vulnhub.com which has more vms to hack into on ur own, and online wargames like https://www.hackthebox.eu where you can pwn virtual computers uon your own or with your friends/team thank you for your comment ! :)
Excellent! It sounds like we will get along wonderfully. Gave you a follow. Hackthebox.eu is a new one for me! I will have to check it out.