Flaw in Microsoft Outlook could be exploited to steal Windows Passwords
An 18-month-old CVE-2018-0950 vulnerability in Microsoft Outlook could be exploited by hackers to steal the Windows Password.
Users are advised to apply the following mitigations:
- Install the Microsoft update for CVE-2018-0950.
- Block ports 445/tcp, 137/tcp, 139/tcp, along with 137/udp and 139/udp used for SMB sessions.
- Block NT LAN Manager (NTLM) Single Sign-on (SSO) authentication.
- Always strong passwords.
- Never click on suspicious links embedded in emails.
“Microsoft Outlook will automatically retrieve remote OLE content when an RTF email is previewed. When remote OLE content is hosted on a SMB/CIFS server, the Windows client system will attempt to authenticate with the server using single sign-on (SSO).” states the CERT. “This may leak the user’s IP address, domain name, user name, host name, and password hash. If the user’s password is not complex enough, then an attacker may be able to crack the password in a short amount of time.”
The attack scenario sees a remote attacker exploiting the vulnerability by sending an RTF email to the victim, the malicious message contains an image file (OLE object) that is loaded from a remote SMB server under the control of the attackers.
“Here we can see than an SMB connection is being automatically negotiated. The only action that triggers this negotiation is Outlook previewing an email that is sent to it.” The following screenshot shows that IP address, domain name, Username, hostname, SMB session key are being leaked.
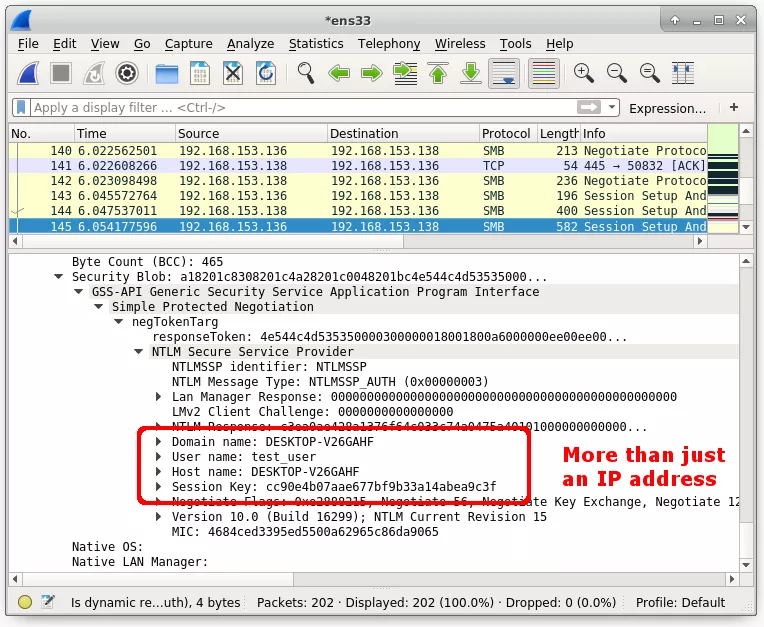
Microsoft Outlook automatically renders OLE content, this means that it will initiate an automatic authentication with the attacker’s controlled remote server over SMB protocol using single sign-on (SSO). This will cause the leak of NTLMv2 hashed version of the password that could be cracked by the attacks with commercial tools and services.
Microsoft attempted to address the flaw in the last security updates, but it only successfully fixed automatically SMB connections when it previews RTF emails, any other SMB attack is still feasible.
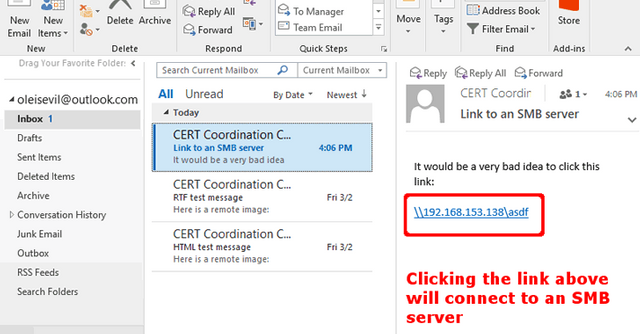
“It is important to realize that even with this patch, a user is still a single click away from falling victim to the types of attacks described above,” Dormann added. “For example, if an email message has a UNC-style link that begins with “\”, clicking the link initiates an SMB connection to the specified server.”
Source: https://securityaffairs.co/wordpress/71302/hacking/microsoft-outlook-cve-2018-0950.html