Get to know Honeybot, a technological trap to unmask hackers
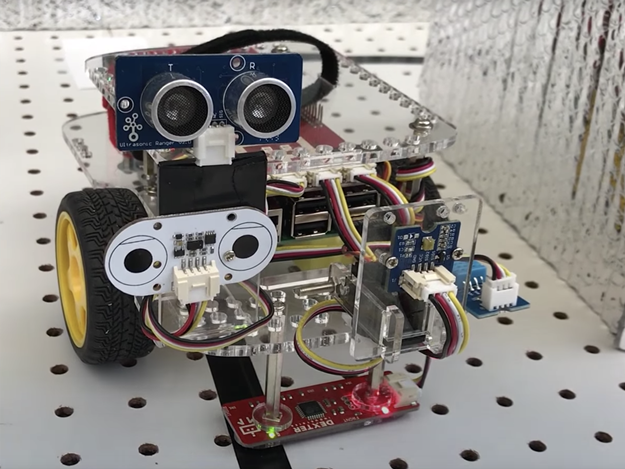
But for the honeypot to be effective, the attacker must believe that it is controlling a normal system. Otherwise you can search for other entries. The challenge of keeping good bits, however, is great, as hackers are increasingly skilled. Following that line, researchers at the Georgia Tech Institute in the United States have developed a robot that, according to them, is smarter than virtual pirates to be used in factories.
The idea is that, instead of just simulating a robot's operation, which may not convince an experienced attacker, the system allows the hacker to control the movements of the android. However, if he tries to do something dangerous with the machine, such as damaging a production line structure, he will disobey the command, but will send a simulation to the invader so that he continues to believe that he is controlling the invaded area, and to whom, from fact, commands the factory.
"A hacked robot inside a factory can not only compromise the integrity of the processes it has access to, but potentially compromise the integrity of the entire industry. Be it in the production line, in medicine, or in military uses, these robots cause unprecedented damage to themselves and the environment in which they are inserted, "says Celine Irvene, one of the authors of the security device, detailed recently in a published article in the Proceedings of the IEEE.
The device has been christened HoneyBot and can be integrated into any robotic system with internet connection. Type devices create game of cat and mouse between hackers and security professionals. However, there are always indications that a system is a trap, like too much ease in access.
In the case of using robots, the android's own formats and behaviors may raise suspicions. Therefore, the researchers decided to create a complete automaton capable of being controlled during an attack and sending compelling data about their movement and their sensors to hackers. "It will be identical to any robot in its environment, but it will use software that looks vulnerable," says Irvene.
The ingenious HoneyBot, however, can decide whether a given command can cause harm to itself or the environment, and by identifying such a situation, to obey the commands and use an artificial intelligence system to create false data and send them to the invader. That way, it can prevent hackers from looking for other vulnerabilities in the system.
- Test in maze
The researchers tested HoneyBot in a cardboard maze that contained several shortcuts that drastically reduced the distance to the exit. Volunteers were able to remotely control the robot using only the information sent by the device to complete the task as quickly as possible.
The shortcuts were marked by the system as dangerous locations, and when the experiment participants tried to cross them, the robot simply stopped. On the computer screen, however, the volunteers received false data indicating that the android was still moving. The deception convinced: people said they thought they were actually controlling HoneyBot for the duration of the test.
"To create a honeypot, you have to have computers, firewall and antivirus. The researchers created a robot that simulates all this, "says Sérgio da Costa Côrtes, coordinator of the data science and artificial intelligence course at the Iesb University Center in Brasilia.
According to Côrtes, strategy is a good alternative for systems connected to the internet. In a major industrial process, such as a production line, an attacker can decalibrate a robot, causing widespread damage. "This is the gain of artificial intelligence. You simulate inside that robot exactly your equipment. The attacker comes out victorious and you collect all the information you need to prevent that person from attacking you again, "he explains.
- Dangers
There are, however, some negative sides to this approach. "I do not see the technique as an attack mitigator. It ends up instigating, causing the attacker to feel challenged, "says Ulysses Machado, information security coordinator for the Federal Data Processing Service (Serpro). "You learn a lot about the behavior of this attacker, the environment must be configured properly and you never have an exact security on it," he explains.
According to Machado, a hacker tends to exploit the system and test everything he can do inside it. This is an opportunity for you, if you are in a simulated environment, to leave important information about how you behave. However, there is always the risk that the attacker will find a loophole and reach the real system.
"I found the experience to be fantastic; we, security and technology, love this kind of thing. The idea of generating for the attacker the feeling that he is unduly controlling a system is very interesting, but we avoid doing that sort of thing. It is a near-hacker process against hacker ", ponders the expert.
- Sugar bait
It is the English term for pot of honey. The idea is that, like the sugary substance, a simulated and vulnerable system will act as a bait for potential hackers and allow them to leave important information about their behavior.
Very interesting, a honeypot on wheels hehehe
A honeypot is a good resource to know how a system is vulnerable, and knowing that will give the keys to protect it, and in the field of iot/robots there is still a long way to know how to protect the systems.
Good post, thnx for sharing it!