Meltdown and Spectre MALWARE Overview from Vault 7 Intel AMD Security Exploits
'Meltdown' and 'Spectre' papers show pervasive memory leak security vulnerability across many CPUs produced over the last 20 years in modern processors. These hardware vulnerabilities allow programs to steal data which is currently processed on the computer. While programs are typically not permitted to read data from other programs, a malicious program can exploit Meltdown and Spectre to get hold of secrets stored in the memory of other running programs. This might include your passwords stored in a password manager or browser, your personal photos, emails, instant messages and even business-critical documents. Meltdown and Spectre work on personal computers, mobile devices, and in the cloud. Depending on the cloud provider's infrastructure, it might be possible to steal data from other customers.

How was Meltdown Found?
The Graz team’s discovery, an attack that would come to be known as Meltdown, proved a critical crack in one of computing’s most basic safeguards. And perhaps most troubling of all, the feature they had exploited was introduced into Intel chips in the mid-1990s. The attack had somehow remained possible, without any apparent public discovery, for decades.
Yet when Intel responded to the trio’s warning—after a long week of silence—the company gave them a surprising response. Though Intel was indeed working on a fix, the Graz team wasn’t the first to tell the chip giant about the vulnerability. In fact, two other research teams had beaten them to it. Counting another, related technique that would come to be known as Spectre, Intel told the researchers they were actually the fourth to report the new class of attack, all within a period of just months.

“As far as I can tell it’s a crazy coincidence,” says Paul Kocher, a well-known security researcher and one of the two people who independently reported the distinct but related Spectre attack to chipmakers. “The two threads have no commonality,” he adds. “There’s no reason someone couldn’t have found this years ago instead of today.”
The information security world is focused on two new security vulnerabilities, “Spectre” and “Meltdown”, that represent vulnerabilities embedded in computer hardware. Lawfare readers should respond in two ways: keep their operating systems up to date and, critically, install an ad-blocker for your web browser. (Here are guides on how to do so in Chrome and Firefox.) In fact, a proper response to Spectre should involve ad-blocking on all government computers. Other than that, don’t worry.
Readers who just wanted to know what to do can stop reading. But for those curious about some of the technical background on these vulnerabilities and why ad-blocking is an essential security measure for a modern computer, read on.

What is Meltdown?
Meltdown breaks the most fundamental isolation between user applications and the operating system. This attack allows a program to access the memory, and thus also the secrets, of other programs and the operating system.
If your computer has a vulnerable processor and runs an unpatched operating system, it is not safe to work with sensitive information without the chance of leaking the information. This applies both to personal computers as well as cloud infrastructure. Luckily, there are software patches against Meltdown.

What is Spectre?
Spectre breaks the isolation between different applications. It allows an attacker to trick error-free programs, which follow best practices, into leaking their secrets. In fact, the safety checks of said best practices actually increase the attack surface and may make applications more susceptible to Spectre
Spectre is harder to exploit than Meltdown, but it is also harder to mitigate. However, it is possible to prevent specific known exploits based on Spectre through software patches.
Malware exploiting Spectre and Meltdown flaws are currently based on available PoC
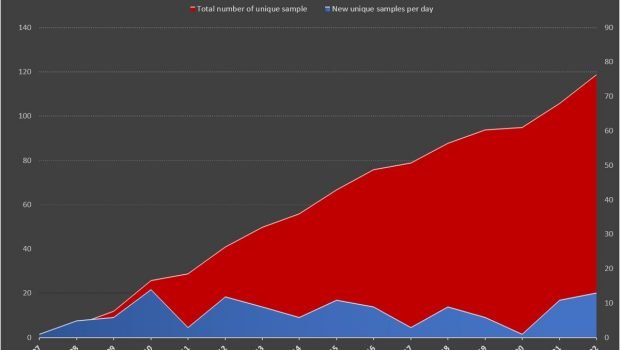
Researchers at the antivirus testing firm AV-TEST have discovered more than 130 samples of malware that were specifically developed to exploit the Spectre and Meltdown CPU vulnerabilities.
The good news is that these samples appear to be the result of testing activities, but experts fear that we could soon start observing attacks in the wild.
Most of the codes obtained by AV-TEST are just recompiled versions of the Proof of Concept code available online. Experts at AV-TEST also found the first JavaScript PoC codes for web browsers like IE, Chrome or Firefox in our database now.
“We also found the first JavaScript PoC codes for web browsers like IE, Chrome or Firefox in our database now.”Andreas Marx, CEO of AV-TEST, told SecurityWeek.
Exploits for the Internet-wide Meltdown and Spectre processor vulnerabilities disclosed yesterday are not yet in the wild, which means users still have a valuable window to apply patches to anything running an affected Intel, AMD or ARM processor.
It’s a familiar race for anyone who lived through the Heartbleed, Shellshock and POODLE bugs of 2014 as attackers feverishly prepare exploit code while vendors rush to get patches and mitigations in the hands of users. The scope of Meltdown and Spectre, however, may dwarf those incidents given that every desktop, laptop, mobile device and virtual machine in hosted environments may be affected.
“It’s pretty bad. It’s like Heartbleed for CPUs,” said Flashpoint senior malware analyst Ronnie Tokazowski. “Just about every computer is affected; phones, computers, you name it.”
The two vulnerabilities break kernel-level Address Space Layout Randomization (ASLR), a mitigation for memory-based code-execution attacks that makes it impossible for attackers to learn the address space of code objects and predict where exploit code might be most successful. The result is that a successful Meltdown or Spectre attack could leak enough memory where an attacker could learn secrets such as encryption keys, passwords and anything else that’s supposed to be protected in the kernel.
Intel, AMD, ARM, Microsoft, Mozilla, Google, Amazon, major Linux providers and others have already made statements and many have also made patches available. Users are advised to update immediately. Software-based fixes are the best bet at this time before hardware-level updates are available.
Meltdown affects almost every Intel processor manufactured since 1995 is easier of the two bugs to attack, according to researchers at Google’s Project Zero. Meltdown breaks isolation between user application and the operating system, exploiting out-of-order execution to leak physical memory to an attacker, and Meltdown is being patched through the Linux kernel under KAISER or KPTI.
Spectre breaks the isolation between different applications and is more difficult to exploit. It too takes advantage of the out-of-order instruction set, exploiting the vulnerability as it is aborted. AMD and ARM chips are vulnerable to Spectre as well, including the ability to affect mobile devices.
Cloud providers are also at risk, depending on how systems are structured and provisioned, Tokazowski said. Amazon, VMware, Citrix, Microsoft and others have made patches available.
Initially it was believed these vulnerabilities could only be exploited if an attacker had local access, however researchers at Mozilla have conducted tests and concluded that this could be exploited over the web using JavaScript.
More Info:
Meltdown and Spectre Kernel Vulnerabilities have created a headache for Intel and Operating Systems are being patched to try to address a problem that's at a hardware level.
According to recent reports, Intel and ARM processors suffer a serious hardware-level vulnerability that the vendors cannot patch via a microcode update. Addressing the vulnerability requires a significant retooling of operating systems, in particular Windows, Linux, and macOS, which reportedly causes up to a 30% reduction in performance in some workloads.
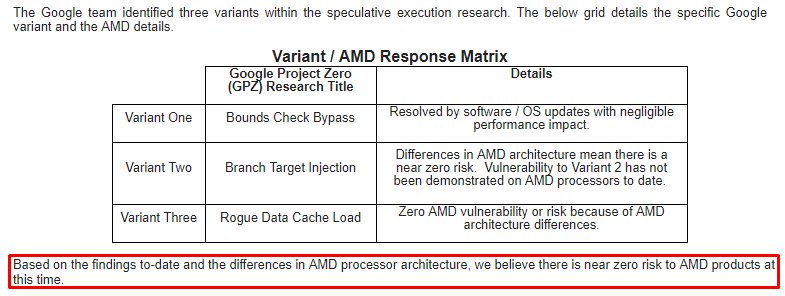
However, that number is likely overblown. The overall impact of the performance regression and the specific programs impacted are poorly defined. As with many pre-release security patches, the details surrounding the bug are under NDA for now, but we expect an official update from Intel soon. Both Microsoft and Linux already have patches in the pipeline. AMD's exposure to the bug remains undefined, with some reports indicating the company's processors are immune and others stating that some models are impacted.
Source
Admittedly, the impact on performance will be felt more in older CPUs. However, it could impact newer chips like the i7-8700k.

Q's:
Am I affected by the vulnerability?
Most certainly, yes.
Can I detect if someone has exploited Meltdown or Spectre against me?
Probably not. The exploitation does not leave any traces in traditional log files.
Can my antivirus detect or block this attack?
While possible in theory, this is unlikely in practice. Unlike usual malware, Meltdown and Spectre are hard to distinguish from regular benign applications. However, your antivirus may detect malware which uses the attacks by comparing binaries after they become known.
What can be leaked?
If your system is affected, our proof-of-concept exploit can read the memory content of your computer. This may include passwords and sensitive data stored on the system.
Has Meltdown or Spectre been abused in the wild?
We don't know.
Is there a workaround/fix?
There are patches against Meltdown for Linux ( KPTI (formerly KAISER)), Windows, and OS X. There is also work to harden software against future exploitation of Spectre, respectively to patch software after exploitation through Spectre ( LLVM patch, MSVC, ARM speculation barrier header).

Which systems are affected by Meltdown?
Desktop, Laptop, and Cloud computers may be affected by Meltdown. More technically, every Intel processor which implements out-of-order execution is potentially affected, which is effectively every processor since 1995 (except Intel Itanium and Intel Atom before 2013). We successfully tested Meltdown on Intel processor generations released as early as 2011. Currently, we have only verified Meltdown on Intel processors. At the moment, it is unclear whether AMD processors are also affected by Meltdown. According to ARM, some of their processors are also affected.
Which systems are affected by Spectre?
Almost every system is affected by Spectre: Desktops, Laptops, Cloud Servers, as well as Smartphones. More specifically, all modern processors capable of keeping many instructions in flight are potentially vulnerable. In particular, we have verified Spectre on Intel, AMD, and ARM processors.
Which cloud providers are affected by Meltdown?
Cloud providers which use Intel CPUs and Xen PV as virtualization without having patches applied. Furthermore, cloud providers without real hardware virtualization, relying on containers that share one kernel, such as Docker, LXC, or OpenVZ are affected.
What is the difference between Meltdown and Spectre?
Meltdown breaks the mechanism that keeps applications from accessing arbitrary system memory. Consequently, applications can access system memory. Spectre tricks other applications into accessing arbitrary locations in their memory. Both attacks use side channels to obtain the information from the accessed memory location. For a more technical discussion we refer to the papers ( Meltdown and Spectre)
Why is it called Meltdown?
The vulnerability basically melts security boundaries which are normally enforced by the hardware.
Why is it called Spectre?
The name is based on the root cause, speculative execution. As it is not easy to fix, it will haunt us for quite some time.
Is there more technical information about Meltdown and Spectre?
Yes, there is an academic paper and a blog post about Meltdown, and an academic paper about Spectre. Furthermore, there is a Google Project Zero blog entry about both attacks.

X0A0