Please be super-cyber safe; from experience and practice I’ve never fallen for none of these issues. Be safe, put into good use protection methods.
How often do you receive promotions, job offers and free travel which are some of the most frequent deceptions? How can we evade these cyber-criminal-hackers?
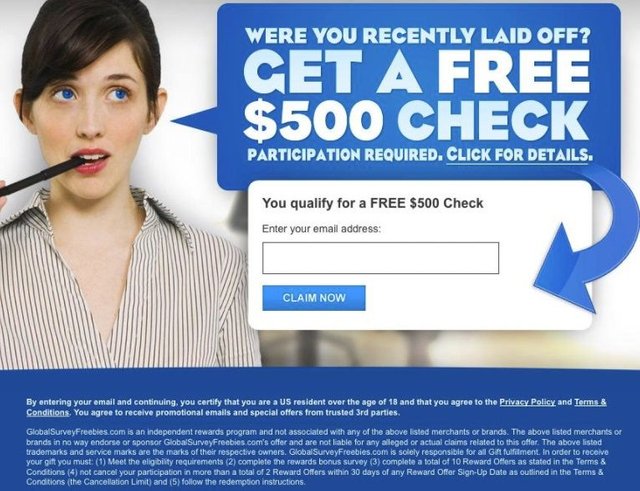
Everything starts in a simple and seemingly harmless way: you find in your social networks a link to participate in a promotion and win tickets in well-known airlines. Just fill out a short questionnaire and share the offer with your friends. The same goes for free trials, balances or job offers. The goal is always the same: to steal personal information.
Computer software specialists say that there is a 'virtual black market' in which large personal data files are marketed.
At present, the information about and of the people has a value. There are many computer threats that seek to steal data and then sell them. In fact, criminals create databases with identification numbers, names, surnames, addresses and emails.
Other security analysts warn that this type of attacks is not executed in a massive way and is not usually addressed. It's not that these crooks choose a particular person or group. The attacks are distributed via email, a technique known as 'phishing'.
In order to evade this type of scams and, above all, to generate a culture of prevention, here are some tips and recommendations that will help you avoid becoming a victim of cybercriminals.
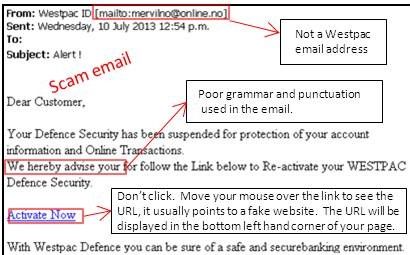
According to experts, a common mistake is to open the links of false promotions directly from the publication. Doing this generates a malicious code download (or 'malware') that is installed on mobile devices revealing all the information. The interaction with this malware is not something that always arises from a double click, it is enough to have 'open doors' (holes in security) in the operating system and once done, it is free entrance for who knows who.
As the well-known saying goes, 'not all that glitters is gold'. When you identify a promotion, do not be put off by the first impression. It is important to doubt, and that is why the main recommendation is to enter the official website of the brand in question to validate the information: do not copy paste; type the web address in a new window of a browser such as BRAVE or better TOR. Also, be aware that you can also access the social network profiles of the company that offers to confirm the promotion – if none, then delete. As a last resort, also remember that you can communicate directly with the company and ask if the offer is real. If information is not available at all, discard the message keeping in mind never to open it – just delete it.
Keeping in mind that fill-forms are one of the main tools that cybercriminals use to steal, avoid sharing information in unofficial locations. Care must be taken with the data that is shared on the forms online, especially on pages that are of dubious reputation. Do not enter the number of the credit card or the cellular if not sure that the site is one hundred percent legal.
In quite a lot of cases, scams are supported by fake sites. That is why it is important to read carefully the address of the page to which the link redirects, taking into account that in general, the link does not have a name related to the company that is offering the promotion for these scams. The deceptions are recognized because the web address does not contain the name of the company that is promoting the offer; on the contrary, it is composed of letters or numbers without a logical order.
Another factor that you must consider to offer greater security in your devices is to keep the applications updated. Typically, each update includes security patches that reduce or prevent the vulnerability of computers. Secondly, applications should be constantly cleaned up, since large amounts of data are often transmitted by them, even when they are not used. I use CCleaner, free version, simple and straight forward cleaner. I use it because it has always worked for me. You can also change the settings of your apps, as this allows you to manage the interaction with the device. For example, they can access sensitive information, track locations, and share user data with third-party servers.
According to a recent survey, it was noted that almost one-third of social network users share their messages, reservations and other personal information with everyone who is online, not just their friends. In addition, 12 percent add people they do not know and 31 percent do so if they have friends in common, even if they do not know the user. Another security-threatening issue is that a quarter (26 percent) of respondents would not hesitate to click on a link sent by a friend without asking what it is or consider whether the sender's account has been ' Hacked '.
In summary, always in doubt; ask yourself “how am I connected to this cyber-message that just arrived”. Remember that NOTHING in this world is free – those who forget this, fall for the scams.
NOTE: nothing of the above is ad; I use them and work for me. Do your own investigation and work with what you feel comfortable. By the way, the links in the reference, check them out first under safe mode, they might be scams !!!
References:
http://www.eset-la.com/
https://www.kaspersky.com/
https://www.mcafee.com/us/index.html
https://www.howtogeek.com/220232/how-to-use-the-built-in-windows-defender-antivirus-on-windows-10/
https://mackeeper.com/
http://rootofscience.com/blog/2017/sains-komputer/memancing-phishing-di-laman-maya/
http://www.businessinsider.com/the-new-breed-of-phishing-scams-its-complicated-2012-2
https://www.piriform.com/docs/ccleaner/introducing-ccleaner/what-is-ccleaner
https://www.torproject.org/
https://brave.com/
Are you into this type of topics, plus others like science, technology, human state, politics? Keep the conversation alive …. UPVOTE & perhaps, RESTEEM, and in addition you might want to click on the FOLLOW for further interesting posts. I do appreciate your comments,


Excellent post
good job