My Comments on Malware and Spams in Email when I was a young student
Note
This is the ninth assignment from my Masters Advanced Network Security Course which has never been published anywhere and I, as the author and copyright holder, license this assignment customized CC-BY-SA where anyone can share, copy, republish, and sell on condition to state my name as the author and notify that the original and open version available here.
1. Email Overview
The protocol that is defined to exchange email over the Internet is simple mail transfer protocol (SMTP). SMTP is used to send email to another email server which is then received through the procedure of post office protocol version 3 (POP3) or another procedure instant message access protocol (IMAP). It can be illustrated in Figure 1 that the email was send via SMTP, then authentication is handled by POP3 or IMAP. The authentication alone is unencrypted, to encrypt is to be send over secure socket layer (SSL) for more secure communication [1].
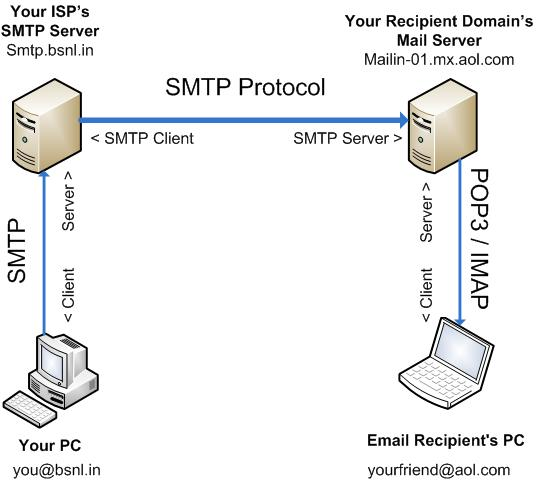
Figure 1. Illustration of email exchange [1]
Another technology is the mailing list where the clients subscribes so they're included into the mailing list. Materials will be send to the subscriber within the mailing list. Security issues on email other than malware mostly dealt with spams.
2. Spam
People defined the term email spam as bulk email or unsolicited email. It's very subjective how each person defines a spam. An example of a common spam is an advertisement sent to a mailing list or lot's of email address, in an indiscriminate way. A light spam usually contains advertisement only but a severe spam may contain threats that could harm the user like malware. The subtopic belows are example of how spam may occur and what measure that had been taken. Most of the below materials are based on [2] and most definitions are based on [3] (by each key words).
2.1 Open Relay
Open relay is a configuration on the mail server to accept all incoming emails either by known users or anonymous users. This was used to be the default configuration of all mail servers but it became unpopular since it was abused by spammers and malwares, refer to small illustration on Figure 2. Most open relay's are closed, or put on blacklist.
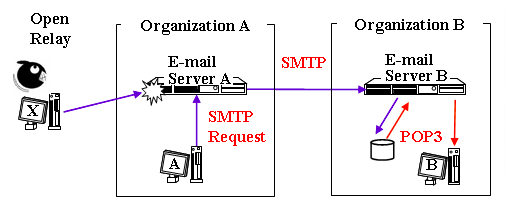
Figure 2. Illustration of open relay abused [2]
2.2 Impact of Spam
There many impacts of spams. It can be summarize in general as follows:
- Very heavy unnecessary network since spams fills the traffic.
- As a user it's a heavy burden in sorting the emails.
- Mis-classify an email (a clean email may be treated as spam or vice versa).
- Domain spoofed, your email domain might get registered as spam (blacklist).
- Worst case could be hijacked or denial of service.
2.3 POP before SMTP / SMTP after POP
To cope with Figure 2, POP before SMTP is implemented with the concept of allowing email transmission if able to retrieve email. In short you be able to access and retrieve your email first, then you're able to send an email. But today people tends to use SMTP authentication instead. Figure 3 is a general illustration.
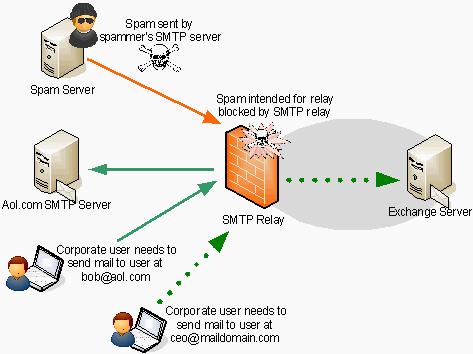
Figure 3. Using authentication for smtp [4]
Back then the POP before SMTP was implemented to cope with the open relay issue, still it's a method to allow email exchange from outside, spammers just need to find another way. (1) First they could gain control (spam bot) the user's PC that had authorization to the SMTP server through service attack worms (SAW) and mass mailing worms (MMS). (2) Second is a method called email error back scattering where on the envelop insert “reply-to: [email protected]” (if error will go to that email). This two are illustrated on Figure 4. How is it possible? It is because of direct SMTP.
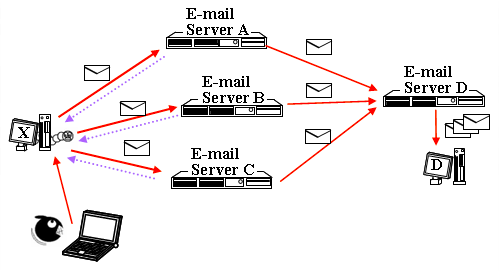
Figure 4. Other round-ways for POP before SMTP [2]
3. Anti Spam
To avoid spams the following are recommended, (note: there are more ways the below recommendation):
- Install email anti virus (AV) which could prevent hijacking and bot controlled.
- Use outbound port 25 blocking (OP25B) which rejects direct SMTP to port 25, instead allowing through authorized email server only (only the email server may use direct SMTP). On the other hand there is inbound port 25 blocking (IP25B) which means that it doesn't receive spam emails.
- Authentication which strengthens point 2. Use the SMTP authentication and over the SSL.
- There exist the sender policy framework (SPF) which registers the authorized email servers into the DNS server. When an email is received the server performs SPF which compares the sender's IP address, email server's IP address and domain. If it doesn't satisfy it will not receive.
- Another is domain key identified mail (DKIM) where a signature is added on the message header based on the secret key.
- Then there is Sender ID which uses SFP and caller ID advocated by Microsoft.
Reference
- http://www.ustudy.in/node/22
- http://md.kumamoto-u.ac.jp/mod/book/view.php?id=98629&chapterid=4984
- https://en.wikipedia.org/wiki/Spamming
- http://www.isaserver.org/articles-tutorials/articles/smtprelayinboundoutbound.html
Mirrors
- https://www.publish0x.com/fajar-purnama-academics/my-comments-on-malware-and-spams-in-email-when-i-was-a-young-xlyegxq?a=4oeEw0Yb0B&tid=steemit
- https://0darkking0.blogspot.com/2021/02/my-comments-on-malware-and-spams-in.html
- https://0fajarpurnama0.medium.com/my-comments-on-malware-and-spams-in-email-when-i-was-a-young-student-2d8f823ca8e
- https://0fajarpurnama0.github.io/masters/2020/07/14/comment-malware-spam-email
- https://hicc.cs.kumamoto-u.ac.jp/~fajar/masters/comment-malware-spam-email
- https://steemit.com/technology/@fajar.purnama/my-comments-on-malware-quarantine-when-i-was-a-young-student?r=fajar.purnama
- https://stemgeeks.net/technology/@fajar.purnama/my-comments-on-malware-quarantine-when-i-was-a-young-student?ref=fajar.purnama
- https://blurtter.com/blurtech/@fajar.purnama/my-comments-on-malware-quarantine-when-i-was-a-young-student?referral=fajar.purnama
- https://0fajarpurnama0.wixsite.com/0fajarpurnama0/post/my-comments-on-malware-and-spams-in-email-when-i-was-a-young-student
- http://0fajarpurnama0.weebly.com/blog/my-comments-on-malware-and-spams-in-email-when-i-was-a-young-student
- https://0fajarpurnama0.cloudaccess.host/index.php/9-fajar-purnama-academics/199-my-comments-on-malware-and-spams-in-email-when-i-was-a-young-student
- https://read.cash/@FajarPurnama/my-comments-on-malware-and-spams-in-email-when-i-was-a-young-student-0c2afe68
- https://www.uptrennd.com/post-detail/my-comments-on-malware-and-spams-in-email-when-i-was-a-young-student~ODYwMDU4