[Tech Tuesday] Applying Industry Security Controls to Personal Information Security #1: Keeping Track of Things.
I would like to start a series on Tech topics and would be posting them every Tuesday. Technology covers such a wide spectrum of topics and I will blog on what I'm most interested in or have actual personal experience. I hope Steemians would benefit from this series as much as I would enjoy posting them.
Applying Industry Security Controls to Your Personal Information Security
(Or -- "What the big corporations do to protect themselves, you can do better.")
Big corporations spend big money just to protect their information assets. Information is power as the saying goes. But more than just having a big budget, corporations are guided by a set of best practices for protecting and securing their information assets. These are called the 20 CIS Controls. (CIS stands for Center for Internet Security). It is the de facto standard used by CIOs/CTOs/CSOs when implementing their security solutions and the same standards commonly referred to by auditors to check if industries are properly protecting themselves.
You can find the complete list here:
https://www.cisecurity.org/controls/
If these are good enough for industries, surely any individual should apply the same principles to protect themselves.
What I would like to do is to translate some of these principles or controls from what was only applicable to enterprises to easy principles that any person can use.
The first five controls are as follows:
- Inventory of Authorized and Unauthorized Devices
- Inventory of Authorized and Unauthorized Software
- Secure Configurations for Hardware and Software
- Continuous Vulnerability Assessment and Remediation
- Controlled Use of Administrative Privileges
Corporations have IT personnel working across multiple shifts and thousands of dollars worth of technology in order to meet these controls. The first two are about being aware of all devices that are brought in and out of the company, which ones are company owned and which ones are B.Y.O.D (bring your own device). It is also being notified the moment an unauthorized computer or device like a router or tablet has been plugged in the office network. Control #2 works the same but for software. It's not a good idea to be running TOR or W.O.W. on a company device, or at least would be very bad for the company if they get hacked because of a freeware filled with holes and malware was on the IT manager's laptop.
So how does this translate to the normal Steemian or Internet user?
Keeping Track of Things
1. Know which devices you own.
Use only your own devices to access Steem, facebook, crypto exchange sites or any site that requires you to enter a username and password! You never know what malware may be running on a friend's computer or the PC in the public library or the office. Some malware have keylogger functions and keep track of all the characters typed in or start recording when it detects a login field. You may also forget to logout completely when you're using an "unauthorized" (meaning not yours) device.
Even when using your own device, don't use public wifi to access your personal secure sites. Use them to get directions, check product reviews, etc. but if it can be helped, never login to your secure sites.
2. Don't share your wifi
This is a bit on the paranoid side and sound selfish. Do not share your home's wifi or personal hotspot. It is possible for someone to collect data passing thru the wifi / router. They can "sniff" your passwords and gain access to your social media sites or your online wallets. People with malicious intent will employ all sorts of technique in order to get that valuable piece of information.
One of the hardest to protect from is social engineering. Someone who's out to get you can introduce you to a friend or insurance agent or whatever and would pretend to need access to your wifi. Or say you're having a party and offer wifi even to people you don't even know. Or if you have a kid and they bring a friend over. You never know who among these people have a special set of skills, tools and enough motivation to sniff as much information they can and profit from it.
3. Don't just install any software or app on your computer or mobile device
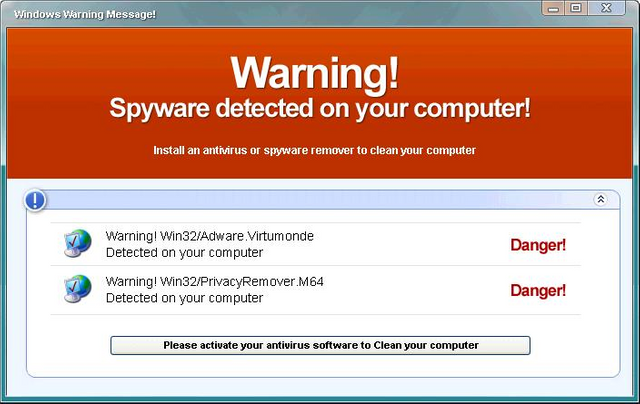
Have you ever seen something like this pop up your screen?
It's a bait for a fake Antivirus installation. Fake AV = malware galore.
Don't be fooled by anything or anyone that urges you to install their tool, productivity software, game or crypto wallet without doing your due diligence. Check reviews, consult with a trusted techie friends that know their stuff.
If you're on Android, use only the official App store for app downloads. Unless you really know what you're doing, it is better to stick to the official than use third party app stores.
4. Keep track of your family's software and application
Sure you kept away strangers from connecting to your wifi. Sure you don't download malicious software. But what about your spouse or kids? You might think what they install on their devices won't affect you. Well we already established that information can be sniffed off the network. You never know when one lovely night and you're logging in to Steem, facebook or your online banking site, when your kid is playing his new favorite android game which turns out to be malicious.
It's like being in a diner full of art thieves and you openly talk about your art collection with a friend.
So how do you do this? Well if your family members are sensible enough, tell them of the dangers of using untrusted software or app. Talk about their favorite apps on their devices. If you have toddlers, secure your devices to enable further verification whenever an app is being installed. If you're the controlling type, require them to submit their devices for 'auditing' and keep a list of the apps. Or you may tell them to ask for permission or second opinion before installing an app.
What did you think about this post? Please share your experiences or questions or tips. I will post controls 3,4, and 5 next week entitled "Get your house in order."

Great idea for a series of posts, I look forward to reading more!
One question I have.... those pop-under adverts. I'm always scared they are running some process in the background.. is that possible?
It is possible. You need to check if the pop up is 1.) a new browser window 2.) A frame/image within the webpage you're currently on 3.) A new window generated by its own process. While all three are potentially dangerous, the third is cause for concern. It means that something has been downloaded and installed on your device and it is likely to have been infected.
Don't get easily tempted to click on the buttons (Close, OK, Yes, No, Cancel, Ignore, and the [X] on the top right corner.) These are click baits. Either close the entire browser or press Alt-F4 if you're on Windows.
Thanks for the question and stay safe!
Cheers for the in depth answer!
Thanks!
Thank you @crytokash for posting this well written and useful article.
A series concerning such matters sounds like an excellent idea.
Appreciate the reSteem......thank you.
Cheers.
Thanks for the encouragement. And I will make sure I complete the series and with more useful info.
keep on with that !!
Thanks, i will!