Why cyber security in enterprises badly needs a rethink
We have come a long way since 1990 when the form virus made itself known corrupting the boot sector of the hard disk. It usually was transmitted when an infected floppy disk was plugged in. You booted the machine and before you could say “Holy Christ”, the machine was toast for the virus had camped in DOS resident memory.
Nowadays viruses/malwares are sophisticated, patient and incredibly destructive. Enterprises are investing in threat hunting, deception sandboxes and even artificial intelligence based security frameworks.
In fact with all those free AI tools floating around, we are seeing an increase in autonomous exploits. These basically create simulations trained to distract the machine learning models which many companies so thoughtfully deploy. In other words it is hacker AI versus anti-virus AI.
Who will win? More importantly does it really matter as long as we know that the war is relentless? Given that there are many open access databases like VirusTotal that have more IOC signatures than the Brexit referendum votes, one tends to wonder about where all of this is going. The usual preferred method is of course to beat complexity with even more complexity.
A Mano e Mano approach that may work wonders for Stallone in Rocky but does very little for CISOs and cyber security personnel.
I will not bother getting into the statistics of virus attacks and the usual fear mongering that accompanies it. If that kind of tickles your funny bone or makes you grab some popcorn then you can Google away to glory.
About thirty years and around 25 serious virus attacks later, the enterprise still thinks that the only way out is to build a better Fort Knox. Good luck with that!
There is no doubt that the enterprise is making things easier for hackers all the time. I am sure that average CISO will cringe on hearing that at least 1/4th of the attacks originate inside the organization techbeacon article on breaches.
Ironically ease of management is directly proportional to hackability
Ease of management is achieved today by centralizing data and the much over hyped single pane of glass management strategies. The single pane of glass metaphor will have your average hacker licking his lips in feverish anticipation. If you don’t believe it or you are just plain contrary then read up on the NotPetya virus that hit a bunch of companies. It is rather well known that it exploited an SMB protocol vulnerability and got onto an Active Directory server. Once it hit the AD service the entire company was down in a matter of hours.
Why would you ever use an AD service unless it simplified your control of the network? It is inevitably obvious that hackers know this little nugget of information as well.
We don’t have to end this diatribe here. We can think about all the wonderful things you can do with virtual datacenters, disaster recovery appliances, universal filers,etc. The hacker is focused on windows into the datacenter while we on the other hand are obsessed with just panes of glass. Go figure!
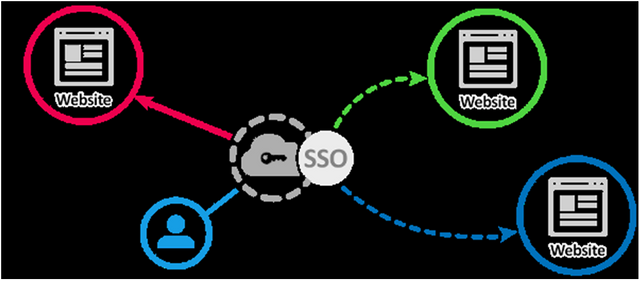
The all world login is a cornucopia of future illnesses
Every company out there is using single sign on. Some use a custom version of Shibboleth but a lot of them deploy RADIUS based solutions. There are less vulnerable solutions like Evidian. All the hacker needs to do is to somehow materialize a single set of credentials out of the rarefied air of the enterprise datacenter. This puts unbelievable stress on the password management infrastructure. The user is harassed into changing his/her credentials once in 90 days (if they are so lucky).
source: Oneall
You can bet your bottom dollar that all end users are sick of password management. The average Joe’s response is either a very simple password or a complex one written down somewhere. Any guesses as to which approach wins?
Hackers probably end up trying a few combinations of dates, family names and places to crack your password in a few hours. A weak password can be cracked using John the Ripper or some other tool in an hour. Maybe he/she can watch a rerun of GoT while your password is hacked! Once they get a password it means they have access to a lot of services using SSO and that spells trouble.
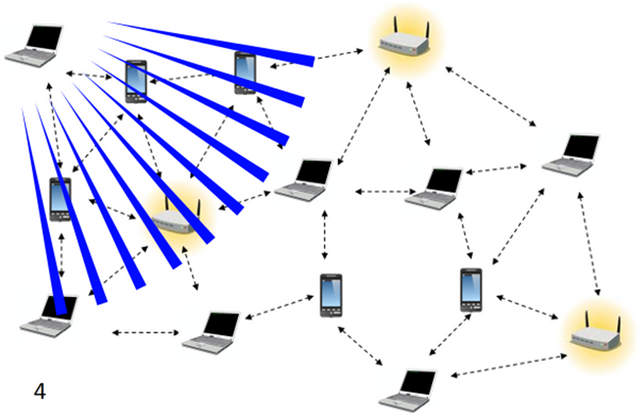
The easy peasy WiFi network
Walk into any corporate location and you will notice an absence of wired network cables. Everyone has a laptop and almost everyone is connected to a WiFi network automatically. Many employees don’t even know the network that they are connected as long as it works. Let us face it you are not going to have Mr Network Guy come down and explain everything to everyone. No Siree! He makes some complicated rules that automatically silo you out of other networks and assure the employee that he/she can only connect to networks provisioned for normal use.
All that is peachy keen but the upshot is that the plethora of networks that are floating around mean diddly squat to the average user. If it connects then he/she will use it. I did a simple test and walked out of a company’s building and powered up my laptop. I saw a bunch of networks available that I could connect to if I knew the password.
The first problem is that earlier, hackers could only get into the company network through the internet but now they must be going mad with the gourmet basket of internal networks presented to them. Even if you turned down the signal strength to -60 dBm (decibel milliwatts), the hacker could turn up his/her broadcast signal strength and still try to connect.
But wait there is more! Hackers are great at setting up ad hoc APs (access points) that an employee inside the building may connect to if they are not careful. You could also DDOS user connections to drop out of the correct network and instead the user may try the other network which is actually just a packet gateway. All it takes is one little misstep and Elvis has entered the building!
Calling for Mr Goldfinger, anyone?
Enterprises are focussing on tightening up the security for primary data to unholy levels and then turning around and handing off all of the data to a universal storage gateway appliance. Ostensibly the single window approach will ensure that data management responsibility is now irrevocably abdicated. The gold copy of data for an organization has now achieved immortality!
This is exactly what your wannabe hacker has been waiting for. It must be so inspiring to be one step away from cyber manna! I am exaggerating a little bit but it is painfully clear that they could not have dreamt up a better scenario. It is evident that they would focus all their attack on such an eventuality. Why bother to write a complex virus that will proliferate itself to thousands of machines?
Picture this; Single Sign On and universal storage dancing around on the datacenter floor looking dreamily into each other’s eyes. But alas, that romance was rudely interrupted by our dandy hacker dude. Perhaps it takes three to tango.
Archive everything forever
Since every piece of data is critical and storage has no limits, why bother to delete anything at all? Talk to any enterprise company and ask them if they have a digital trash policy? You would be surprised at the results of that little survey.
Let us assume that a single file that is 10 years old has been infected before it was inserted into the archive. One day an assiduous researcher pulls it out on the verge of some breakthrough discovery or maybe the legal eagles are trying their best to be the company’s proctologists. Either way the odds are that the infected file is restored and the virus scanner has completely forgotten about its existence. In fact our faithful malware detector probably threw the signature out into the trash because it was obsolete.
Remember the plague?
Did you see Arnold saying I will be back in Terminator? Well he has nothing on this baby because no one is prepared for it anymore. It will wreak havoc and cause a whole lot of grief. In today’s world, old data seems to be as valuable as its latest cousin.
Let us orchestrate our way to the hacker hall of fame
Every enterprise is completely sold on the idea of an orchestrator waving its magic wand and making things fly around. Orchestrated actions are at the core of data management, resource provisioning, audits, DevOps activities, policy based event responses, etc. Imagine if a hacker somehow air dropped a few custom actions into orchestration land.
Remember that most orchestration frameworks do not validate actions that invoke files and hence once the action is defined, any file can be invoked. This is an entirely new exploit type and can be hidden deep within the action database of the orchestration engine. Granted that custom knowledge is required but an insider could easily assist because even a little knowledge is dangerous with an orchestrator. This could easily happen
The sound that you hear is a train wreck in progress right from the top of the Angel Falls basin.
A hacker would adore an orchestration exploit because it would give him/her unlimited power to conceal, destroy or even ransom information.
It is time enterprises stopped building monuments to their past
Every enterprise is saying that a breach is imminent and they have accepted that that there will be more than one incident. It is ironic to think of them spending all this money on their datacenter and then visibly bracing for malware impact.
There are solutions for every potential problem but:
Albert Einstein once said “The definition of insanity is doing the same thing over and over again, but expecting different results”
Look outside the window and you will find that the world is changing. Decentralization is the key. If nothing else blockchain has taught us the diminishing value of core networks. It is time for every enterprise to be agile. The mantra is clear; if you don’t adapt, you die. Or worse first you get robbed and then you die!
It is a painful change away from the datacenter mentality but I guess the world is not a pleasant place and our hacker brethren are not going out of their way to be courteous.
Replace your two factor authentication with hardware security keys using U2F authentication. Software deployments need to be authorized using smart contracts automatically decentralizing certificate management. Storage needs to be on decentralized nodes sitting somewhere without a singular way of hacking its contents. Data access must be driven by using trustable certificates rather than logins/roles. Smart contracts are immutable and bring the promise of untainted access enforcements. Focus on speed of recovery since there has been enough spent on protection from malware and intrusion detection/response.
For Pete’s sake, get a grip on the digital garbage that is piling up.
There are many aspects of the enterprise datacenter that needs massive changes to combat the next cycle of cyber terrorism but that is a long and never ending story in itself. We can all agree that it is way better to embrace the change rather than being Santa Claus to our friendly neighbourhood hackerman!
Blockchain is particularly adept at bringing machine level trust and with the advent of IoT, its ubiquity in the datacenter is assured. Why not embrace it all the way?



@adarshh Thank you for not using bidbots on this post and also using the #nobidbot tag!