All you need to know about ATM Security (Part 2 of 5)
Part II
This was a research I made with a Russian colleague year ago and thought it might help someone out there.
Kindly note that at the end of this part you would find References section for the whole paper ( the 5 parts) this part and the upcoming ones, as it would be difficult to separate the references of each part
Also be noted that this paper was written to address Non-technical folks to give them an overview of Securing the ATM
Backup Security Measures
Backup security measures need to be in place for both information security control and physical security. This is to ensure that integrity is maintained for the information and physical security systems. Backup security in the case of ATM's may involve a reserve of power set aside to maintain physical security features such as alarms and CCTV cameras. (APHIS,2014)
Risk Management, analysis and Computer Security Incident Management
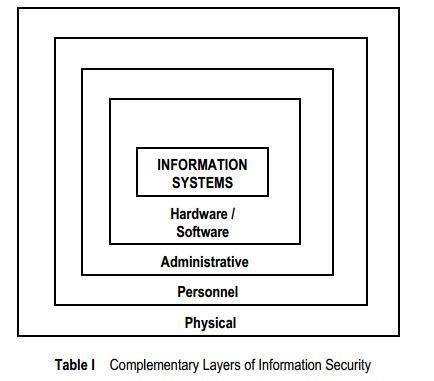
The objective of an information system security program is to protect an organization's information by reducing the risk of loss of confidentiality, integrity and availability of that information to an acceptable level. A good information security program involves two major elements, risk analysis and risk management. In the risk analysis phase, an inventory of all information systems is taken. For each system, its value to the organization is established and the degree to which the organization is exposed to risk is determined. Risk management, on the other hand, involves selecting the controls and security measures that reduce the organization's exposure to risk to an acceptable level. To be effective, efficient and reflect common sense, risk management must be done within a security framework where information security measures are complemented by computer, administrative, personnel and physical security measures.
Risk management becomes a senior management issue. A balance has to be reached between the value of the information to the organization on the one hand and the cost of the personnel, administrative and technological security measures on the other hand. The security measures put in place need to be less expensive than the potential damage caused by the loss of confidentiality, integrity and availability of the information. Many formal risk analysis methodologies on the market require technical expertise in the area of information technology and relevant controls and availability of precise threat frequencies that may be beyond the reach of many audit offices, at least initially. The objective is to build up over time the necessary expertise and resources. (INTOSAI, EDP Audit Committee, 1995)
A risk assessment is carried out by a team of people who have knowledge of specific areas of the business. Membership of the team may vary over time as different parts of the business are assessed. The assessment may use a subjective qualitative analysis based on informed opinion, or where reliable dollar figures and historical information is available, the analysis may use quantitative analysis. The ISO/IEC 27002:2005 Code of practice for information security management recommends the following be examined during a risk assessment:
• security policy,
• organization of information security,
• asset management,
• human resources security,
• physical and environmental security,
• communications and operations management,
• access control,
• information systems acquisition, development and maintenance,
• information security incident management,
• business continuity management, and
• regulatory compliance.
(Sattarova, F. Y. and Prof.Tao-hoon, 2007)
Computer Security Incident Management.
The National Institute of Standards and Technology (NIST) describes a computer security incident as ―resulting from a computer virus, other malicious code, or a system intruder, either an insider or an outsider‖. Similar to responding to natural disaster incidents, computer security incident management requires a process and a team to follow the process. The new player would be an individual well versed in information systems technology and security. In the event of an incident caused by an attack, the entity should have response procedures in place to recognize an event. Some attacks are detected by a sensor, a network analyst or a user reporting something unusual with the computer. Containment is critical for stopping malicious network traffic or a computer virus, the spread of which could be terminated by taking the computer(s) off-line, if the IT department or service provider performs these functions. This would include ensuring the destruction of any hard drives that still maintain security information and that any breach is acted upon to mitigate losses. (APHIS,2014)
Training
Employee and contractor behavior is the primary source of costly data breaches. It's also the best way to prevent loss.
Security can't be guaranteed.
As Clint Eastwood once said, "If you want a guarantee, buy a toaster." The only secure system is one that's unplugged, turned off, and in a locked room. Since it's not practical to leave our systems turned off, we need to understand the risks to our systems and prepare ourselves to defend them. Preparation begins with understanding — and that's where awareness comes in. With all the news stories about hackers and breaches involving personal information and ATM Security, it's easy for the security message to sound over-used and tired. It's easy for people to say, "It won't happen here." Yet, studies and surveys repeatedly show that: the human factor (what employees do or don't do) is the biggest threat to information systems and assets.
Example
Late one night in Kiev, an ATM started dispensing cash seemingly of its own accord. In its investigation of the matter, Kaspersky Labs discovered that the bank’s internal computers were compromised. These computers were used by staff responsible for processing book keeping and daily transfers. Malware called Carbanak was installed in the computer by a targeted phishing attack and allowed the attackers to view everything done on an infected system. Once the system is infected, Carbanak logs keystrokes and takes screenshots every 20 seconds so it disclosed to the hackers routine banking operations and procedures. Training employees to identify phishing attacks and social engineering is of paramount importance. It is difficult to protect against an employee with malicious intent, but at the very least, awareness training can reduces the risk of malisons attack. Kaspersky has disclosed that more than 100 banks across 30 nations have had their accounts compromised by Carbanak. (Perlroth, 2015)
The best way to achieve a significant and lasting improvement in information security is not by throwing more technical solutions at the problem — it's by raising awareness and training and educating everyone who interacts with computer networks, systems, and information in the basics of information security.(APHIS,2014)
CIA
For over twenty years, information security has held confidentiality, integrity and availability (known as the CIA triad) as the core principles of information security. Many information security professionals firmly believe that Accountability should be added as a core principle of information security.
Confidentiality
Confidentiality is the term used to prevent the disclosure of information to unauthorized individuals or systems. For example, an ATM transaction requires the card to be physically present at the ATM, from which the customer enters his PIN to authenticate the transaction and the ATM processes the transaction through a secured network. The system attempts to enforce confidentiality by encrypting the card number and PIN during transmission, by limiting the places where it might appear (in databases, log files, backups, printed receipts, and so on), and by restricting access to the places where it is stored. If an unauthorized party obtains the non-physical details in any way, a breach of confidentiality has occurred. Breaches of confidentiality take many forms. Permitting someone to look over your shoulder at the ATM screen while you are entering your PIN on it could be a breach of confidentiality. If a laptop computer containing sensitive information about a company's employees is stolen or sold, it could result in a breach of confidentiality. Giving out confidential information over the telephone is a breach of confidentiality if the caller is not authorized to have the information. Confidentiality is necessary (but not sufficient) for maintaining the privacy of the people whose personal information a system holds. (Sattarova, F. Y. and Prof.Tao-hoon, 2007)
Integrity
In information security, integrity means that data cannot be modified without authorization. This is not the same thing as referential integrity in databases. For example, integrity is violated when an employee accidentally or with malicious intent deletes important data files, when a computer virus infects a computer, when an unauthorized user vandalizes a web site, when someone is able to cast a very large number of votes in an online poll, and so on. If an automated process is not written and tested correctly, bulk updates to a database could alter data in an incorrect way, leaving the integrity of the data compromised. Information security professionals are tasked with finding ways to implement controls that prevent errors of integrity. (Sattarova, F. Y. and Prof.Tao-hoon, 2007)
Availability
For any information system to serve its purpose, the information must be available when it is needed. This means that the computing systems used to store and process the information, the security controls used to protect it, and the communication channels used to access it must be functioning correctly. ATM systems aim to remain available at all times. Which means preventing service disruptions due to power outages, hardware failures, and system upgrades. Ensuring availability also involves preventing denial-of service attacks. In 2002, Donn Parker proposed an alternative model for the classic CIA triad that he called the six atomic elements of information. The elements are confidentiality, possession, integrity, authenticity, availability, and utility. (Sattarova, F. Y. and Prof.Tao-hoon, 2007)
Potential Impact on Organizations and Individuals
FIPS Publication 199 defines three levels of potential impact on organizations or individuals should there be a breach of security (i.e., a loss of confidentiality, integrity, or availability). The application of these definitions must take place within the context of each organization and the overall State interest.
The potential impact is LOW if The loss of confidentiality, integrity, or availability could be expected to have a limited adverse effect on organizational operations, organizational assets, or individuals. Clarification: A limited adverse effect means that, for example, the loss of confidentiality, integrity, or availability might:
● Cause a degradation in mission capability to an extent and duration that the organization is able to perform its primary functions, but the effectiveness of the functions is noticeably reduced;
● Result in minor damage to organizational assets;
● Result in minor financial loss;
● Result in minor harm to individuals.
(DoIt, State of Maryland, Department of information technology,2008)
The The potential impact is MODERATE if The loss of confidentiality, integrity, or availability could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals. Clarification: A serious adverse effect means that, for example, the loss of confidentiality, integrity, or availability might:
● Cause a significant degradation in mission capability to an extent and duration that the agency is able to perform its primary functions, but the effectiveness of the functions is significantly reduced;
● Result in significant damage to agency assets;
● Result in significant financial loss;
● Result in significant harm to individuals that does not involve loss of life or serious life threatening injuries.
(DoIt, State of Maryland, Department of information technology,2008)
The potential impact is HIGH if The loss of confidentiality, integrity, or availability could be expected to have a severe or catastrophic adverse effect on agency operations, organizational assets, or individuals. Clarification: A severe or catastrophic adverse effect means that, for example, the loss of confidentiality, integrity, or availability might:
● Cause a severe degradation in or loss of mission capability to an extent and duration that the agency is not able to perform one or more of its primary functions;
● Result in major damage to agency assets;
● Result in major financial loss;
● Result in severe or catastrophic harm to individuals involving loss of life or serious life threatening injuries
(DoIt, State of Maryland, Department of information technology,2008)
Controls
When Management chooses to mitigate a risk, they will do so by implementing one or more of three different types of controls.
Administrative controls – Policies, Procedures, Standards & Guidelines
Administrative controls (also called procedural controls) consist of approved written policies, procedures, standards and guidelines. Administrative controls form the framework for running the business and managing people. They inform people on how the business is to be run and how day to day operations are to be conducted. Laws and regulations created by government bodies are also a type of administrative control because they inform the business. Banking sectors have policies, procedures, standards and guidelines that must be followed, the administrative controls applied to ATM's involve securing card data and customer PIN's. Other examples of administrative controls include the corporate security policy, password policy, hiring policies, and disciplinary policies. Administrative controls form the basis for the selection and implementation of logical and physical controls. Logical and physical controls are manifestations of administrative controls. Administrative controls are of paramount importance. (Sattarova, F. Y. and Prof.Tao-hoon, 2007)
Logical controls
Logical controls (also called technical controls) use software and data to monitor and control access to information and computing systems. For example: PIN's, passwords, network and host based firewalls, network intrusion detection systems, access control lists, and data encryption are logical controls. An important logical control that is frequently overlooked is the principle of least privilege. The principle of least privilege requires that an individual, program or system process is not granted any more access privileges than are necessary to perform the task. A blatant example of the failure to adhere to this principle of least privilege is logging into Windows as user Administrator to read Email and surf the Web. Violations of this principle can also occur when an individual collects additional access privileges over time. This happens when employees' job duties change, or they are promoted to a new position, or they transfer to another department. The access privileges required by their new duties are frequently added onto their already existing access privileges which may no longer be necessary or appropriate. (Sattarova, F. Y. and Prof.Tao-hoon, 2007)
Physical controls
Physical controls monitor and control the environment of the work place and computing facilities. They also monitor and control access to and from such facilities. For example: doors, locks, heating and air conditioning, smoke and fire alarms, fire suppression systems, cameras, barricades, fencing, security guards, cable locks, etc. Separating the areas that are freely accessible from those that should only be accessed with sufficient authorization (Eg. wall mounting the ATM to deny back panel access) is a very important measure for ATM security. An important physical control that is frequently overlooked is the separation of duties. Separation of duties ensures that an individual can not complete a critical task by himself. For example: an employee should not also be able to authorize himself to inspect/reload the ATM. Collusion between employees is still possible, but the risk is smaller than giving all controls to a single person. An applications programmer should not also be the server administrator or the database administrator - these roles and responsibilities must be separated from one another. (Sattarova, F. Y. and Prof.Tao-hoon, 2007)
References
Animal and Plant Health Inspection Service (APHIS). Information Systems Security Control Guidance Document (2014 February 12). Federal Select Agent Program. Clarke, J. (2009). SQL injection attacks and defense. Burlington, MA: Syngress Pub. http://www.selectagents.gov/resources/Information_Systems_Security_Control_Guidance_version_3_English.pdf
Atmsecurity.com,. (2015). Acketts Anti-Theft Device protects ATM attacked at Total Garage in Binchester, County Durham | ATMSecurity.com ATM Security new. Retrieved 24 March 2015, from http://www.atmsecurity.com/articles/atm-fraud/acketts-anti-theft-device-protects-atm-attacked-at-total-garage-in-binchester-county-durham.html
(5/20/12). BBC. HSBC cash machines hit by IT failure. Retrieved from: http://www.bbc.com/news/business-18140620
Bankinfosecurity.com,. (2014). Malware Attacks Drain Russian ATMs. Retrieved 24 March 2015, from: http://www.bankinfosecurity.com/russian-malware-attacks-drain-atms-a-7412/op-1
Berson, T. Kemmerer, R. and Lampson, B. (1999).Realizing the Potential of C4I: Fundamental Challenges. Retrieved from Microsoft research website http://research.microsoft.com/en-us/um/people/blampson/63-C4ISecurity/Acrobat.pdf
Brad, G. (2005,January 12) .The Role of the Security Analyst in the Systems Development Life Cycle. SANS Institute Retrieved from http://www.sans.org/reading-room/whitepapers/awareness/role-security-analyst-systems-development-life-cycle-1601
Clarke, J. (2009). SQL injection attacks and defense. Burlington, MA: Syngress Pub. https://books.google.co.in/books?id=KKqiht2IsrcC&printsec=frontcover&dq=Clarke,+J.+%282009%29.+SQL+injection+attacks+and+defense.+Burlington,+MA:+Syngress+Pub.&hl=en&sa=X&ei=zQ8PVdPNEdLauQTYrICoAg&redir_esc=y#v=onepage&q&f=false Shirley, R.(2009, April) THE SYSTEM DEVELOPMENT LIFE CYCLE (SDLC). Computer Security Division, Information Technology Laboratory (ITL), National Institute of Standards and Technology. http://csrc.nist.gov/publications/nistbul/april2009_system-development-life-cycle.pdf
Daniel, K.(2011-2015). Various topics about Security systems. Retrieved from http://theinfopro.blogs.451research.com/index.php/tag/secureworks/
DoIt, State of Maryland, Department of information technology.(2008, September). Standards for Security Categorization of Information Systems. http://doit.maryland.gov/support/Documents/security_guidelines/Security_Categorization.pdf
Dunlap, S. (12/1/14). Silver City Sun-News. ATM machine stolen, dragged through streets of Silver City. Retrieved from: http://www.scsun-news.com/silver_city-news/ci_27046565
(3/19/09). InfoSecurity. Russians hack Diebold ATM software. Retrieved from: http://www.infosecurity-magazine.com/news/russians-hack-diebold-atm-software/
INTOSAI, EDP Audit Committee. (1995, October). Information System Security Review Methodology. International Organization of Supreme Audit Institutions. http://www.issai.org/media/13024/issai_5310_e.pdf
John, R. (nd). Firewall Planning and Design. York Technical College Retrieved from http://yorktech.com/department/itdept/rouda/PDF/IST292/Chapter%201.pdf
Kaufmann, L. (8/10/12). IT Security Community Blog. Exploiting ATMs: a quick overview of recent hacks. Retrieved from: http://security.blogoverflow.com/2012/08/exploiting-atms-a-quick-overview-of-recent-hacks/
Kukiewicz, J. (8/30/11) Choose.net. Anger grows over HSBC's online banking 'Secure Key'. Retrieved from: http://www.choose.net/money/guide/news/hsbc-secure-key-online-banking-problems.html
Joe McMahon. (2015).Secure Your ATMs. Retrieved from McAfee website http://www.mcafee.com/fr/resources/technology-blueprints/tb-securing-atms.pdf
Marianne, S. and Joan, H. and Pauline, B. (2006, February). Guide for Developing Security Plans for Federal Information Systems. Computer Security Division, ITL, National Institute of Standards and Technology. http://csrc.nist.gov/publications/nistpubs/800-18-Rev1/sp800-18-Rev1-final.pdf
(nd) Paragon Applications Systems. Diebold (US) Enhances ATM QA Testing with Paragon Tools. Retrieved from: http://www.paragonedge.com/news/case-studies/diebold-enhances-atm-qa-testing-with-paragon-tools.html
PCI, (2010, October), PCI DSS Quick Reference Guide, Retrieved from https://www.pcisecuritystandards.org/documents/PCI%20SSC%20Quick%20Reference%20Guide.pdf
PCI Security Standards Council. (2013, Jan). PCI PIN Transaction Security Point of Interaction Security Requirements (PCI PTS POI). Retrieved from PCI website https://www.pcisecuritystandards.org/pdfs/PCI_ATM_Security_Guidelines_Info_Supplement.pdf
Perlroth, D. (2015). Bank Hackers Steal Millions via Malware. Nytimes.com. Retrieved 24 March 2015, from http://www.nytimes.com/2015/02/15/world/bank-hackers-steal-millions-via-malware.html?_r=0
Sattarova, F. Y. and Prof.Tao-hoon, K. Vol. 2, No. 2. Security Review: Privacy, Protection, Access Control, Assurance and System Security. Retrieved from International Journal of Multimedia and Ubiquitous Engineering http://www.sersc.org/journals/IJMUE/vol2_no2_2007/2.pdf The Government of the Hong Kong Special Administrative Region. (2008, February).AN OVERVIEW OF INFORMATION SECURITY STANDARDS. Retrieved from: http://www.infosec.gov.hk/english/technical/files/overview.pdf
Weight, A. (Sept 2009). ATM Security Working Group. Best Practice for Physical ATM Security. Retrieved from: http://www.link.co.uk/SiteCollectionDocuments/Best_practice_for_physical_ATM_security.pdf