Privacy Workshop #4 - Know Your Address and Secure It
"When the going gets weird, the weird turn professional" - Hunter S. Thompson
I'm going to tell a story about a job I had and after that you are going to know who you are talking with, and if you have never worked at a data center or heard of one before, I promise this will blow your mind and you will understand the internet twice as much as you did before. In fact, by the end of this article, you will be able to look at screens that right now would look to you like this:

and actually know what's going on, and by the end of this article.
The internet is weird. It is big. It is potentially monstrous. It is a veritable Machine City working underneath us, invisible unless you really go looking for it, go through a few doors requiring biometric entry in the escort of a person who is well known to be a serious, studious, reputable person. I worked in a data center with around 200 rows of cabinets and 30 cages, and a public cage where anyone could rent a spot to put whatever computer then wanted. NC4 had a masked cage there(further study of NC4 will be rewarded). It was one floor above the 'cash vault' of the bank of america in downtown los angeles and I was making 45k. When they closed that vault, I felt it over my whole body, I would always laugh. (Like 'close it up for the night boys, just leave the new deposits next to my chair and ill watch them until morning') Gosh I liked that job, but my boss was a jerk secretly trying to set up a coin mining rig and didn't care about anything else like the frequently failing plesk server with the susan g komen foundation's Los Angeles homepage on it and a bunch of lawyers minimalistic stuff who you could tell, really, really did not like having to call me at 1pm on a Thursday with email trouble and there wasn't much I could to to push a button anyway. It was one of those servers failing so badly it would have a false alarm 10 times a day too. Really annoying Val. The funnest moment was when it failed and everyone on the entire server called me personally every day for about 2 weeks while Val tried to put this Plesk server back together out of backups that hadn't been completing for a few months at least. It was fun watching him have to deal with that. He was not happy and couldn't blame anyone. There were literally hundreds of emails of me notifying this server was going to fail, like comically so. Like it was some real poetic justice right there and also, and this is where I will brag a little bit, I Predicted The Future Using Obvious Facts About Reality.
On my first day there, they asked me to build a windows 200blah server and plug it in, put it on the network. There was only one socket open on the long socket board, basically a 6' long meaty extension cord with 20 plugs on it and a voltage readout you could monitor by ethernet if you wanted but I've never worked at a place with their shit together enough to do this although I would think it would be one of the best things to monitor for alarm but whatever. Instead we just had a ping to every server, as if every server should be configured to respond to ping or have the extra traffic, but whatever Val. The best I can say about Val is that I didn't have nightmares about him after I lost the job due to an unfortunate mildly disabilitating car accident that gave me severe headaches when I moved my shoulder for about 4 years. He was not the worst boss I have ever had and is kindof fun to impersonate when telling this story live. But I would call Val whenever something real bad was happening like Bill Orreilly's homepage being attacked by Anonymous, which happened I think 3 times while I was there. There are traffic charts of how much internet is going where and you will see what would be like a viral marketing campaign like 20 times the size of the blair witch campaign trying to load like a button image on his front page because it was comically large for a button graphic or something, and nearly the whole place would be about to shutdown because it was like 5-10 times the total traffic of the entire facility. There were fibers within 10 feet of my chair that went all the way to Tokyo and New Zealand, like if you were a tiny person, you could walk there open air through a tiny glass tube with lights blinking, like, way more times a second than you can possibly fathom.
There are like 8 of these rows with these outsized power strips strapped to the corners of these cages with rip ties, and the cable management is a mess. Cable management is important to me as a system and network administrator, and when I notice colleagues who have either never heard of it or do it without, idk, a certain finesse and, let's say, 'Zaszz' will receive my condescension and disapproving sideways glances.
This was a mess, I was not impressed and I had the sinking of feeling you got hired by a place that doesn't really care about doing good work, a low morale organization, but whatever. I plugged this puppy in and turned it on, the lights came on for a second and went out completely. As did the entire rack I plugged it into. Sinking feeling. I really felt like a mess up, like I moved some other cable or was a clutz and even though I wasn't even moving must have just with sheer bad luck tripped over the 4" diameter power cable with a plug the size of my whole hand.
In system administration I knew at least that there are two kinds of change you can make two a system, Reversible and Irreversible. And I also knew another principle that came into play, in the event of everything being borked and you have to do something fast, powercycle that shit.
So I pulled the plug back out, powered down that strip like an astronaut would flip a switch on the ceiling before launch, and started to see some activity on the other systems coming back up.
This sudden loss of ping to about 12 servers in the public rack brought the other NOC Admins out pretty quickly, wondering what kind of idiot this new guy must be to on his first unsupervised activity caused catastrophic failure doing what is basically the simplest task in the entire world.
Well, turns out those numbers on the giant power strips are important, and there is, gasp, a LIMIT to the amount of voltage that you can put on one of them.
If I had gone back there to the NOC hq and said, like spock or data, 'Hmm, I ran some calculations on this power strip output reading and if I put another 600 watts on this strip, it's going to cause all sorts of strange underpower conditions in the entire rack which is going to take several of these shady slovenian websites offline, which will really suck for our client. I think we need to find another power circuit for this one because that entire rack is about 200 watts from lighting on fire or opening a portal to the netherworld.'
Well, that wouldn't have flown either. But in hindsight, those guys knew that entire rack was mostly full and that there were potential overloads on those circuits. In other words,

So all those computers in the public cages, NC4, the rented out cages that serve viruses pretending to be 'PC Cleaning software', a major movie production company with every single medea movie's homepage, and just a bunch of random stuff like a high end clothing/design firm who Val always demanded a higher level service for than anybody in the whole place, were on our network.
I write all this to say, that all of these entities, millions of dollars worth of hundreds of computers, doing all sorts of various internet crap from banking to selling t-shirts to being the most idiotic propaganda and worst films ever seen by humankind in all of history(I mean, Bill Orreilly and Medea, these are not the epitomes of american culture although the two in a way deserve each other)....the same company made the hunger games also btw, which are also horribly unwatchable(and yes, it was I who copied the original first day promotional hunger games 'capitol city' website in the public folder and made it live, so I'm pretty much an important person in human history),
I Say All This to point out an incongruous and counterintuitive fact about how this entire operation worked. How big do you think the device was that all of the internet came into and out of for the entire giant room? There was a single device that was a single point of failure, how big do you think it was?
I'm curious what you think, only you can know what your intuition would have told you, but the answer is it was about the size of compact dishwasher.
When Bill Oreilly's absurdist propaganda theater of a homepage was taken offline on Sunday morning at 11 a.m., I was on the phone to Val, he came in, plugged into that device, studied the nature of the flood of traffic, isolated where it was mostly coming from and what type of packets they mostly were, and then set up rules to disallow those kinds of packets or limit the total number of them to something reasonable.
The entire field of Network Engineering is about what goes on inside that dishwasher. I suspect the sum total of knowlewdge required about that to be an expert could be on par with the total amount of knowledge a doctor has to have. It is difficult math, it is tons of arcane rules, it is being able to analyze and react to a situation in real time, and it is about not borking it up with fail keystrokes.
I can't teach you network engineering, but I can teach you everything else in that data center. I can teach you to be an operator.
You are the NOC of your own equipment. Your computer is not a block of granite with a holographic display. It has parts inside that obey the rules of physics as they interact with each other to perform design functions, the culmination of which is a keyboard and display that shows letters and plays music and movies and connects to what we know as the internet.
Your computer has an address. It has aggregate traffic. That traffic can be analyzed. You can build a logical block or filter against traffic you don't like or want known as a firewall. You can encrypt your traffic and files. You can make your computer alert you with alarms under certain conditions. The heat of your computer can tell you about what is going on with it as can the fan speed. Programs can be forced to quit or forced to run.
The question is, are you an operator or a user?
We need more operators. A lot more. The more of us there are, the less each individual one of us stands out. The more afraid they will be to go after any individual one of us. The more things we will know that they do not. The less they will feel they can predict us, the more they will have to bargain with and respect us, the less they will be able to resort to political violence against inconvenient individuals.
The thing about being a good person is that it makes you inconvenient to bad systems, which can be dangerous. But it is the system that is inconvenient. Either all humans are inconvenient or none of us are, and I take the latter view.
Every operator is a potential team member against the people doing bad things in the world but the more users there are, well. You might as well volunteer to be part of a tornado that can be wielded as a weapon by the powerful against the weak or to get votes for someone like Hillary Clintoon or Donald Troomp.
Users are a tool in the hands of the too-powerful or 1% or institutional authority of whichever flavor, as they predict and manipulate you with mass media and full knowledge of everything you were curious about in the last year, telling you what you want to hear, managing your levels of shock like a cow whose meat the farmer doesn't want to spoil while he builds ever smaller cages for you just around the corner.
Users are the both the product and raw material, the people the powerful know aren't any threat whatsoever under any circumstances, that even if they saw the truth of the system they would forget it the next day.
Privacy workshop holds and asserts that the risk of being on a list of known operators is less than the risk of being completely naked to a system of pervasive surveillance.
Everyone wants to be an operator, but they have not been taught the proper attitude to approach the technology, so the things I am speaking about appear like dark shark infested water. But news flash, you are in shark infested water. This is 2018, bad people are in charge who don't care about your rights and hollywood producers can legally rape people and who knows what else, there are cartels, militias, private security firms spying on anyone who knows anything, and ok, reread #2 if you have to. I have made my point.
Networking 201 - IP Addresses, RFC 1918 ,the OSI Model, and Wireshark
When you turn on your router at home for the first time, it connects over the wire to your provider's networking hardware and requests an IP address.
It will be in this form: 245.144.56.125 (a truly truly random IP, but it belongs to someone out there.)
4 numbers, always 255 or less, never less than zero, separated by 3 commas. This is your public internet address just as much as you have a house number, it identifies the people at your physical location, although in the USA at least it does not identify a person. There are a limited number of these numbers, for math reasons that are fairly obvious, and there are not many IP's left although it is still totally doable to purchase them from resellers, so in my opinion the hype about address exhaustion isn't a big deal. But they invented IPv6 anyway so that every device in your house that uses electricity can have it's own address if it wants to also.
There are two kinds of address and this is a key point. RFC(request for comment, basically the way computer people come together and set a standard so their lives are easier) 1918, which is near and dear to my heart, describes what will be a public, or Wide Area Network address like the one your ISP gave your router, or it will be a Private Address for a Local Area Network.
You can identify Private addresses because it starts with the 192.168, 172., or 10., most people have seen these numbers at one time another on their home or work computer. Your router or your wifi device can distribute more private addresses than you can shake a stick at, regardless of if there are no more public IP's left available. (see note 1) Everyone in your house shares this public address, your computer, your ipads, your printers, your neighbor stealing your wifi to download pictures of boobs, whatever.
Guess what? By day 2 of everyone in your house doing their normal stuff on facebrak, amazn, microshaft, and etc every marketer in the world knows where you are. Not kidding. It is just true. If you do not obfuscate traffic going out of your public IP address, they all know the address associate with your facebrk profile, you know the one scary company that asks your friends if you are a real person or if that is your real name? Yeah them.
There is a company called Max Mind and a myriad of other advertising firms like doubleclick that are just going to store and analyze everything you do with that address and resell it all over the world, and resell it at market price to whoever is asking. If you fart in bed, you will get an advertisement for what you ate the day before. It is insane the way these people think and work. They have built a panopticon that claims to only want to suggest things that might help you in life, but it what is really being done is making a model of society that they can run simulations on, so that they can take away your rights or basically do to you whatever they want, like the population of a prison.
FusionGPS, Frank Lutz, you see these guys' work during the elections. The main thing that is happening in western countries is the hobby horse issues are the only things ever discussed on corporate media, abortion, race baiting, inexplicable violence, war propaganda, and they have carefully studied people like you and know what will motivate you, and how to motivate someone against you. It is very well calculated and it is a form of mind reading and mind control.

This is what is written on the inside of this famous building in washington d.c., a monument to someone you might have heard of before:
I have sworn on the altar before god eternal animosity towards any form of tyranny over the human mind and bullshit in general. - Thomas Jefferson
The point of view where a person would subject himself to this is to me truly foreign and in the case where you have children who are going to be raised with every internet search they made from the age of 8 being permanently stored for analysis by AI, it is deeply, horribly unethical. You don't have the right to give all that away just because you don't have time to get around to it, that is not your choice to make and you are not doing your job protecting them, like, at all. And should be ashamed of yourself if you let your children be abused in this way, and yes it is a form of child abuse.
So your router has the public IP and your wifi gives you a private ip, like 192.168.1.5 and all is well. Having learned to operate at the level of security advised in Privacy Workshop #3, you open a connection to your VPN service in Timbuktu. Then you go to facbrook and those asshats see that your address is known, by max mind, to be that of a vpn provider, so they store the data but they put some check next to it that says 'he's not really in timbuktu tho guys' or they have softwares at doubleclick that do the same or something else, who knows the mind of madness.
If someone at some shady forum tries to attack your computer, they now also have to convince this vpn provider's firewall to let their attack or scan through, and vpn providers don't want that static so it's going to be difficult for them.
Scan? Attack? Well yes, you can be scanned and attacked from outside from the internet, as you can scan as well. Max Mind is meta data, but if someone really wants to have a look at you, they will use a program like Nmap, which sends a bunch of echo signals to all the ports on your computer.
Let's define some terms:
Packet - the significant unit level of internet information in IP (internet protocol) networking. A webpage is transmitted by breaking it down into packets of various sizes. IP networks are frequently redundant, so if one packet goes missing, both the sender and receiver know what to do. This is frequently what is happening when you are waiting for a web page to load and it is taking too long someplace you know the internet is not that hot.
Firewall - An application on your computer that examines packets that attempt to initiate connections from a remote location and shuts that crap down with a 'talk to the hand' type response, and can be set up to log the event, letting you now someone came by in the middle of the night and knocked on your door. Without a firewall set to log and report traffic events, you are essentially unable to operate your own defenses of your own home as you can not adapt if your security profile changes.
Port - There are 64000 ports on you computer, your browser uses 80, your email 443, your torrent client 52000 or something, IT pros like me memorize the first 1024 the best we can because it helps. Ports are how different services and applications share the single ip address your computer has. The port number is an important part of each packet.
Scan - Sending out a small, almost unnoticeable burst of packets, that examine which ports are on a computer and use that information to determine if you are a threat, if the operator of that system is competent, if the server is for instance a web server or an email server, or if there are security vulnerabilities. If you know which OS a person has, you just look up vulnerabilities like in a catalog if you are an attack specialist. This is why regular changes of operating systems can be advantageous. it makes someone who might be tracking you have to redo some steps before their beloved spreadsheet has a decent count on your taint hairs again.
Ping - the simplest way to test a connection, simply asking the remote computer to respond with a tiny packet saying 'i am here', accompanied by a latency in ms, which is useful for gaming. A good ping is under 30ms, a bad one is over 100ms for most games. The further you are from The Dishwasher, the higher your latency will be, same goes for aggregate traffic which is frequently related to the time of day.
Nmap - A program specifically made to scan and fingerprint remote systems. It is how I could know you are running a windows server or a linux server even though I didn't call you on the phone to ask. It is generally considered innocuous, and can also be used as a diagnostic step. Scanning and nmap are very very handy things.
DNS - The phone book of the internet, how you know bork.com has the public IP location of 253.12.36.33. (which I scan and see that port 80 and 135 is open and that tells you it is probably microshaft IIS, for example, and that the operator of this system isn't an operator at all, as my scan got through his firewall and there are non-essential ports open to attack vectors.)
Dig - linux command line command for finding out what website is at what IP. Dig -x command does the reverse, super handy aspect of linux.
MXToolbox - a polite way to do dns/reverse dns lookups, handy dandy site for many reasons. Use it.
Router - The Dishwasher in this story, the nexus of nexuses of the internet. These are the backbone of how the internet functions. Their processors are optimized for network calculations, so they decide where packets go at the speed of light and send them there. Routers talk to each other in complicated adaptive protocols that are more complicated than any actual human could understand at this point. Here be dragons. Russia was able to route a huge amount of traffic through its own routers to capture it all, for about 10 minutes a few months ago, it was a huge failure of american security as they own an entire snapshot of all american traffic. ( see note 2) The russians planned this for years, Years, and it is one of the greatest coups in the history of information warfare and it was reported to americans like it was just a rainy day on the internet.
Switch - Multple routers and computers plugged into the same switch will all be able to talk to each other over the LAN(192, 172, 10. IP's right?) at a very fast rate, very useful for moving files around on a network, but also, for analyzing network traffic at a low level.
Whaa? Analyze network traffic at a level of wha?
The OSI Model and Wireshark and How to Audit your Network Traffic
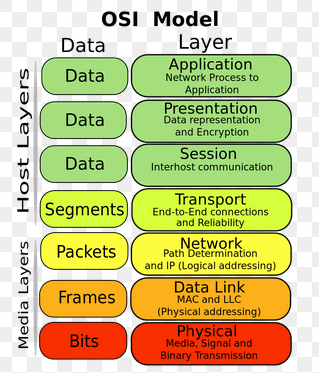
At the network layer, two devices on the same switch all actually see the same traffic. And there are ways to make an application in the application layer look down into the network layer and report on what that is doing on the local machine.
The way to do both is called, Wireshark. Download it now and keep a copy in your important programs folder. It is a program that in a truly dystopian future may become difficult to find or dangerous for peole to know you have. Not kidding. This is the point at which someone watching your download activity would say, oh, this person is getting serious about something.
Users do not use wireshark. They trust that all that is going on down there below must just be fiiiine, why should I worry about any of that.
Loopback - the computer talking with itself, don't be confused by this, every system has it, it's ok to ignore for now.
There are two ways to use wireshark, one is to let your local computer run it and in this way your computer watches itself. Pros are it's easy, cons are, it might miss certain types of traffic designed to elude wireshark, which the people who make viruses have unfortunately also heard of before. The backdoors in intel chips themselves may be able to elude wireshark.
However, with method #2, they would not be able to. In this method, you use a switch to put two computers and a router on the same network, then as the computer whose traffic you want to inspect sends packets to the router, the second computer will copy those to its local hard drive for analysis. The same method could be used by someone in the network closet to attack another person on the network, so always know where your switches and network equipment are and keep some eye on them. You don't want mystery devices on your network.
Watching wireshark capture traffic is the moment you realize that you have become an operator.
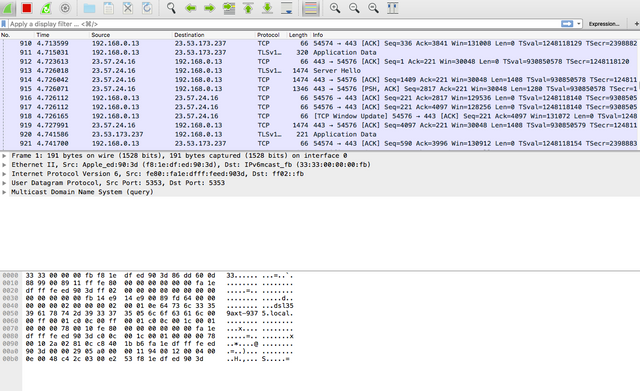
This is some torrent traffic prior to my vpn activating, usually a big no-no but I'm out of reach of the MPAA
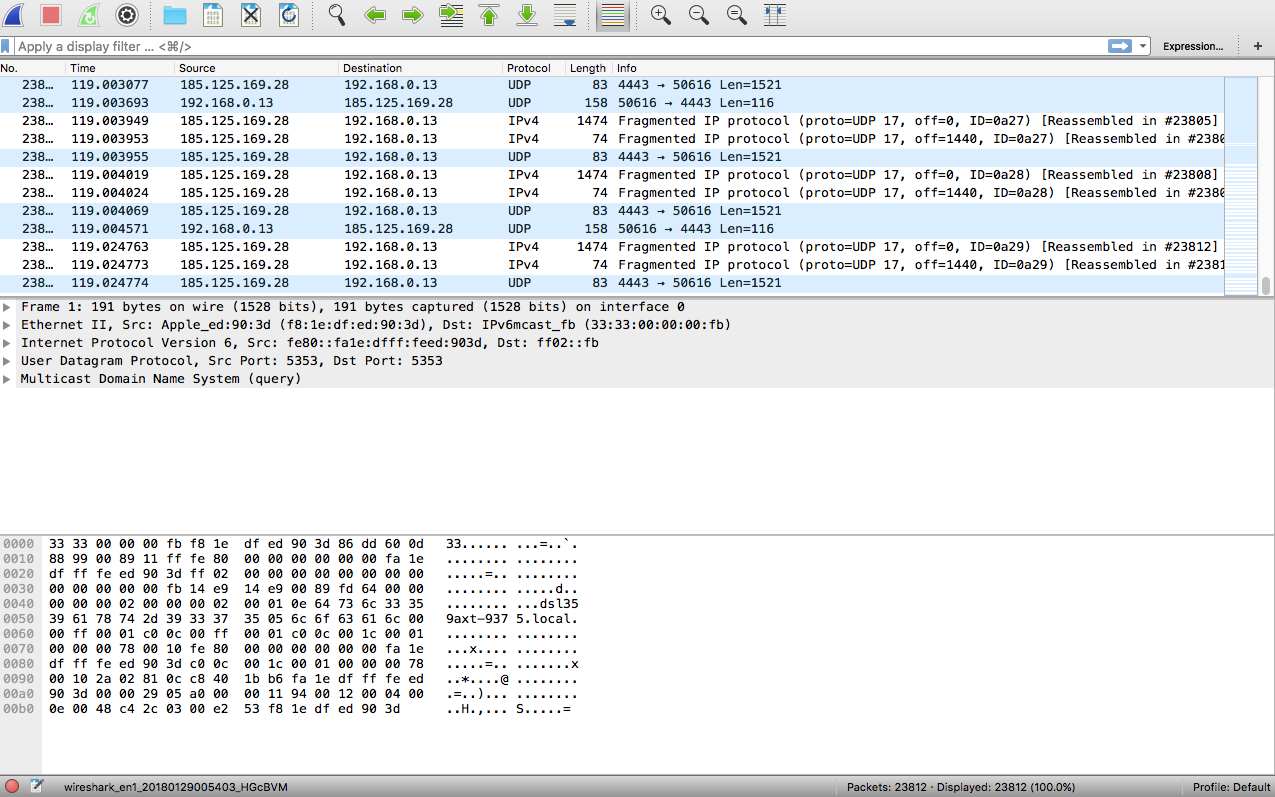
This is the locked down vpn traffic showing the remote ip of my vpn service provider and that all the packets during that snapshot of time are talking with it.
Any state actors who are surveilling me already know I use that company, for now, and like heck if im going to ever use this company again after my contract runs out soon now that i posted that lol, but I want you guys to see what the guts of the internet look like.
Homework challenge 1:
a.What is the nationality of that ip address?
b. What company owns this IP?
Homework challenge 2:
a. Download and install wireshark (and not from softpedia or cnet! from teh project page ffs)
b. Turn your computer completely off in such a way that the internet will not turn on immediately when you boot it up(people using microshaft will not be able to complete this assignment...)
c. Once you are into your OS, turn on wireshark and set it to capture all traffic on whichever interface you use.
d. Now, turn on your internet and watch the fireworks. Dozer will be proud.
e. Let it go for ~3 minutes. Then press the square to stop the capture.
f. Lookup each of those ip addresses, find out who owns them. make your own spreadsheet and figure out what ip addresses your computer reached out to without being asked to by you and try to figure out why your computer thought it should do that.
g. Look for anomalies or interesting things and then post in comments what you find.
Someone who doesn't know what an ip address is watching the hundreds of packets per second scroll by with their different flagging colors is going to think that what you are doing is pretty awesome, you should get a kick out of this and pat yourself on the back for getting past 'internet 101' and into operational tactics, which is currently the only way in this world to have what humans call privacy. And then teach everyone you know to do the same. Help them hop off the silver platter upon which they are being served to people who want their data and to give nothing in return for it but vulnerability.
note 1: so why does anyone think our refrigerators and microwaves are going to need more than that, unless the people who made ipv6 are planning on a fully dystopian future where we aren't allowed to have private networks in our homes, only fully public devices?)
note 2: Warning, there will be cursing ahead: It is for this and other reasons listed in Privacy Workshop #1 that america is losing the information war horribly and I truly, truly cannot help them other than by helping the actual citizens of the country protect themselves. You NSA/CIA/FBI/DIA people have failed the american people horribly, shamefully, and you should all be fired for spending a trillion dollars to be completely inneffective, and to yourselves be just as bad of an enemy. You are serving the people you are trying to protect on a platter. You inbred 1% elite dickwipes and your fucking student loans and H1B visas, you threw out the chance to raise millions of network engineers if you just would have invested in the actual people of your country who have a 20% unemployment rate rather than preying on them with usurious student loans, and then also the fucking drug war bullshit which makes it impossible to get a clearance unless you hate or can lie about liking all of the best drugs. I don't know how any of you fuckups sleep at night.
This concludes Privacy Workshop #4
Kudos for all who participated in actually doing the stuff, post results in comments. I know this was some work, but there is no faster way to get there than just sitting down and reading. All I can do is explain what I know in the clearest terms possible.
Thanks also to anon donor 1, you made my week, you truly made the good vibes get a lot stronger. I take back all that stuff about the community not coming through for me. Remember I am trying to do this as an occupation and I am putting, I think, full time hours into it at this point, and happily so.
I am continuing because I got the support I asked for, and if these upvotes and good vibes continue, I'll see you at Privacy Workshop #100 in a year or two :)
I may post an essay about crypto tomorrow, it may be a few days til I get to #5 where I will write extensively about Piracy and Jamming.
I need community support to keep putting these you, if you found this helpful upvotes, resteems, and gifts are welcome and appropriate:
BTC:
14yW3eWq8yiyJYBBkZyNrQFaBDxFEFTs6f
ETH:
0x8c2898c560f23a92dc5a5cfd20080d9af053a579
LTC:
LPGKb88s3w4cXbzcU1MpzQ6UpPPhPJr4ru
BTS:
actual-mindhawk
Peace! Liberty! Reason!
Wow, you have written it all, This content is great and an eye opener to some if not all. Thank you for sharing.
Hi Mindhawk... I wish I had seen this kind of stuff a week and a half ago. I'm poor. Like -- Living on a very limited budget poor and when my laptop started doing funky things 10 days ago, which indicated to me that the end of it's 2 year lifespan had drawn near, I upgraded to a new laptop that has the Windows 10 system on it... I didn't want to go to Windows 10 (for all the reasons you have explained i.e. no control and keystroke logging etc), but it was the cheapest machine I could buy. Believe me, I don't want to be "just a user". I want to have the knowledge to know when my machine is being surveilled. My 11 year old son wants a computer and my husband and I have decided to start saving to get him his own machine for his 12th birthday that runs Linux.... so he won't be a "user" either....
I have to confess, it's scary to take the plunge with this. I'm the kind of person that after I've smoked a fine sativa (I have a med marijuana prescription) - I can find myself stopped at an intersection at 12:30 at night (while out for a walk) - debating to myself about whether JayWalking would be a good thing to do.... Asking myself about the CCTV at intersections, thinking about the history of Ireland during "the troubles" where the Police targetted people based on who obeyed the traffic signals even when there was absolutely no traffic to be seen.... Do you get what I'm saying here? I know that once you start to encrypt your communications that THIS, in and of itself puts you "on a list" -- and therefor, I've decided that if I ever do start to become more than a "user" -- It's not something I would ever discuss online in any way that could ever be traced back to me....I'd never log onto any of my accounts on a machine that logged into my email, social media or even steemit accounts. I'm that paranoid... Does that make sense to you? Then again... maybe I am already security conscious -- and this discussion is a little like my standing on a street corner at 2:30 in the morning, at an intersection - debating whether or not it looks better to the CCTV that I'm obeying the traffic lights or not... In any event... I'm going to start saving up for a new computer so that I can someday actually do the homework for your classes here, and do it in a way that does not actually let anybody know I am doing it. I hope that does not sound too paranoid and suspicious. I used to have pgp on my machine back in 2000. I stopped using encryption with my communications after Sept 11th for obvious reasons. And it's been 17 years since I've had contact with people who have been seriously involved in security culture. It's going to take a little while to come in from the cold. Bear with me please. Cheers for now. And thanks for laying all this out. It's good stuff. I've resteemed it.
used laptop, 150-250 cash, good models are thinkpads and dell inspiron or latitude
these are all over the place, sitting in stacks, 5 years old hardly used. on your security machine you just need basic performance.
you can overwrite windows 10 tonight with the fedora download if you have an 8gb stick.
courage is the virtue that makes all the others possible. i wouldn't suggest trying to do this unless you had two computers side by side, one to follow instructions with.
ssd drives are under 100 dollars now too, how tos to replace them per model are easy to find.
there is an attitude among americans that they should just wait and see, or that in a few weeks ill get the gumption to do this.
it is a learning disability, it is like talking with people with brain rot. do or do not, there is no try. but forget being an effective activist if you can't even take this time in your own home, why would you think you can change the world if you can't change your computer? why are you using a tool that is used more against you than for you? you'd be better off without it.
facebork and windows 10 extends the police station into your home. (amazon and gorgle are also on my list, apple will soon be on it probably too.)
I want you to be your best self somena, you are making it harder than it is though, which is kindof good news. The workshop is not here to resolve the rest of these issues, it's beyond the scope. what i'd prefer to see is a question i could answer about your next step to implement your privacy.
I simply do not have any extra money laying around unless I cashed in some steem, which I am loathe to do. Maybe I can crowdfund. I dunno. It's rough. I'm divorced, on a fixed and very strict limited income and taking an employment program which is eating up all my time and energy atm. I don't offer this as an excuse... and I agree with you about my computer being weaponized against me. This is all a much longer conversation than I am comfortable having on a non secure line. I get the peril we are in. I get the urgency of the need to raise awareness and educate people before things go much further. Let me say this... I don't have a cell phone. I don't use VOIP. I don't use google when I do any investigative reporting /journalism because I personally don't want to give google what I might know or find out in the course of a pursuance/investigation to feed it and make it all the better to spy on more people with and sell their data to the highest bidder. There are certain topics that I don't discuss with anybody online and I rarely will allow myself to get pulled into a private chat with anybody. I had a hard adjustment to the idea that everything about my life online and in telecommuinications was up for grabs and could be used against me. I never want to be lulled into a false sense of security about privacy again. I've had a couple of nervous breakdowns over this (among other things) over the last 18 years.
I'm going to re-read the documents you have posted and just keep familiarizing myself with the material until such a time as I have the means to get a machine that I would be comfortable using for secure communication and data storage. It's a big step to go dark. For the time being, I'm just barely getting by putting food on the table and a roof over my head. It will take awhile before I have a couple hundred dollars. (ps... I'm in Canada, not the US)
well that's just where you are stuck today. maybe post and ask steemit if anyone can help, idk.
The method: break bigger problems down into smaller ones.
don't get ahead of yourself, one step at a time, utopia won't be built in a day :)
canada is actually by its nature a much safer place to live and be than the USA, don't be ruled by fear, don't give in to negative self-talk, and you are aok where you are at right now and no one is here is judging you.
Just want to let you know that this has been read. It's too much info for someone without a technical mind like myself, but the steps you gave are easy to follow. I know you are right.
"The point of view where a person would subject himself to this is to me truly foreign and in the case where you have children who are going to be raised with every internet search they made from the age of 8 being permanently stored for analysis by AI, it is deeply, horribly unethical. You don't have the right to give all that away just because you don't have time to get around to it, that is not your choice to make and you are not doing your job protecting them, like, at all. And should be ashamed of yourself if you let your children be abused in this way, and yes it is a form of child abuse."
Excellent! 100% Agree
@originalworks