MEET THE PROTOCOL THAT'S POWERING THE INTERNET
"I can't connect to the internet", "I need to go to the internet", "connect me sharp sharp", these are some of the complaints I get when attending to customers on our cooperate internet connectivity solutions. When I see that the downtime has not caused much disruptions, I try to cheer them up by throwing a question like this to them, "where is the internet located?". Well none of them were able to answer the question as they quickly wave it off. I'm not here to answer that question today but to elaborate on the protocol that powers the internet. And this protocol is called INTERNET PROTOCOL popularly called IP.
Internet was born in the year 1983 following the discovery of Transmission Control Protocol/Internet Protocol (TCP/IP) by the ARPANET but took a more organized form starting from 1990. In a general term, the internet is me and you. It is located everywhere. And the protocol that makes this possible is the internet addressing system called the IP address. Many of us can recognize an IP address when encountered but there's more to those numbers than meets the eye.IP address in its initial design is a 32-bit address used to identify unique devices on the internet. ARPANET never knew that internet could get this big cause in their design, the initial address following laid down convention have unique
addresses of up to 65 million. IP address functions because each address is unique, that is, no duplicate address must appear on the internet. As at the year 1999 there were over a billion devices on the net! but the addressing scheme was still in use, even as I compile this post my address is still withing the 32-bit range. This was made possible by the introduction of Network Address Translation (NAT) which allows many devices to appear on the internet using one IP address. Sounds like a contradiction to the statement above about each devices on the internet using a unique address right? Well, NAT makes this possible by using port numbers to create what is called Socket. Two sockets might have the same IP address but definitely different port numbers. To see the sockets in use in your PC, open command prompt and type "netstat" then slap enter button.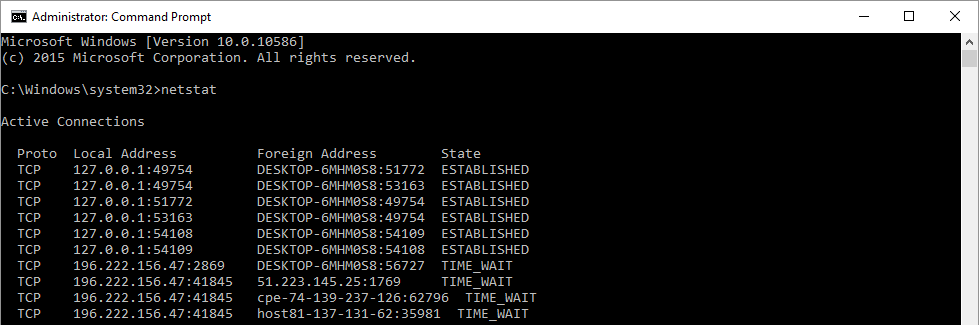
The number appearing on the right side of the colon is the port number while the number on the right, the IP address while the combination of both is called a network socket. For every process started in your PC, the operating system assigns a unique port number to that process, this why information on one tab a your browser does not flow into the next tab cause each tab has a distinct port number or process ID.
NAT saved us from the problem of address exhaustion for a while but not for good. This was why another version of IP address was introduced. The IP Version 6. This version was developed by Internet Engineering Task Force (IETF) in 1998. The version 6 makes use of 128 bit address as opposed to the 32-bit of the previous version, the Version 4 making available a whooping address space of 3.4 exp(34). Though all the addresses are not usable on the internet but the version 6 is big enough to allow each individual alive to have thousands of device active on the internet with a unique address.
If IP is this powerful, then there must be more to it than mere numbers. IP address is equipped with what we call Header.
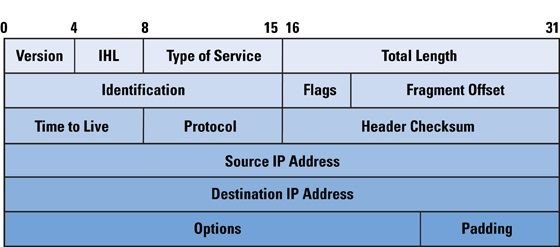
The image above is a header belonging to IPv4 but the version 6 is very much similar. The boxes contained in the header above are called fields. Each field is measured in bits and sums up to 32 bit which is the size of an IPv4 address.
The version field is 4-bit in size and maintains a constant value of "0100" in base 2 corresponding to the number 4 in decimal for the IPv4 and you guessed it right, it maintains a constant value of "0110" corresponding to the number 6 in decimal for the IPv6. This field dictates to the network equipment that the address it's handling is of the type version 4 or version 6 as the case may be.
The ToS field or simply the type of service field is divided into two. The Differentiated Services Code Point (DSCP) and the Explicit Congestion Notification. The ToS is used to specify the priority level of a packet. By this, packets can be directed or routed more efficiently. For example, voice packets are more delicate than data packets, when these two packets are given the same priority, the weaker one suffers some loss. In this case the voice packet often experience what is called Jitter, which is the delay in the actual arrival time of a transmitted packet. Another example where Tos is necessary in sizing network traffic. This is often seen in enterprise network where traffic for example coming from or going to a particular office is given preference to any other traffic. ToS is 6-bit in length.
Total Length field as the name implies is used to define the size of the entire packet and is 16-bit in length. The length defined includes the header of the address and data contained in the packet itself. The minimum size of a packet defined by the total length is 20bytes or 160-bits while the maximum packet size that can be defined by the total length field is 65,535 bytes or 524,280-bits, though developments has pushed these values further.
TTL or time to leave field is used as a loop control in the cause of data transmission. Loop in data transmission is a very serious conditions and this field help to prevent this by allowing network equipment decrements its value any time data arrives. Once the TTL field counts to zero(0), the receiving equipment discards this packet and hence is out of the system. TTL is 8-bit in size. Whenever we execute the "ping" command, the TTL value is displayed as a function of time and measured in seconds.
The Header Checksum is used to ensure that the data integrity is maintained throught the period the data is in transit. It is also a 16-bit sized field. This calculation is always carried out each time a network equipment receives a packet and if the result of the calculation carried out on the header checksum is not the same with the result it obtained in the checksum field, the packet is discarded and another copy may be requested for by the receiving device.
The Source address field contains the IPv4 address of the device sending the packet while the Destination field contains the IPv4 address of the device receiving the packet. These two fields are the only field with the ability to change value while the packet is on transit.
Flags field is a 3-bit field that is used to control and or accurately identify packet fragments. The first bit starting from the right or the least significant bit is the More Fragment flag used for a unfragmented packets and this is used when there is enough resource available for handling packet fragmentation. The next field(middle bit) is the Don't Fragment flag and is used when there are insufficient resources for handling fragmentation while the most significant bit is the Reserved flag and maintains a value of zero. The protocol field hold the internet protocol numbers. These numbers are assigned by the Internet Assigned Numbers Authority.
))
))

Well done. I remind a lot :) TY
Well done @henrychidiebere. Nice revelation
Your post just got wide recognition from @steemstem.
You've really added a lot of effort over the last few weeks.
Congratulations!!!
Thanks. Boss I appreciate the support.
YO! Tech boss! =)
Hahahaha. I don't think I am, just putting my experience to writing.