[EN] U2F - Universal Second Factor - The basic functionality
I have already mentioned the TOTP procedure for 2-factor authentication in another article. In this one I would like to mention U2F.
I will sketch out and explain the individual mechanisms step by step.
What is U2F

Source
Universal Second Factor is an open standard driven by the FIDO Alliance[1] for 2-factor authentication devices. The second factor is to be achieved by ownership. In principle, USB, NFC and Bluetooth are supported.
The standard is based on the principle of public-key cryptography[2] and the challenge-response method[3].
Public-key cryptography
At this point I would like to explain the basic approach of a challenge-response procedure. Based on this model, further mechanisms are to be taken up afterwards.
The device holds a private key that never leaves the device. When registering, the public key is handed over to the server (I will describe exactly how this works later on, as some procedures need to be explained in more detail).
The basic procedure is as follows:
- The server generates a challenge that is transferred to the device via the browser.
- The device signs this challenge with the private key
- The server checks the signature with the public key
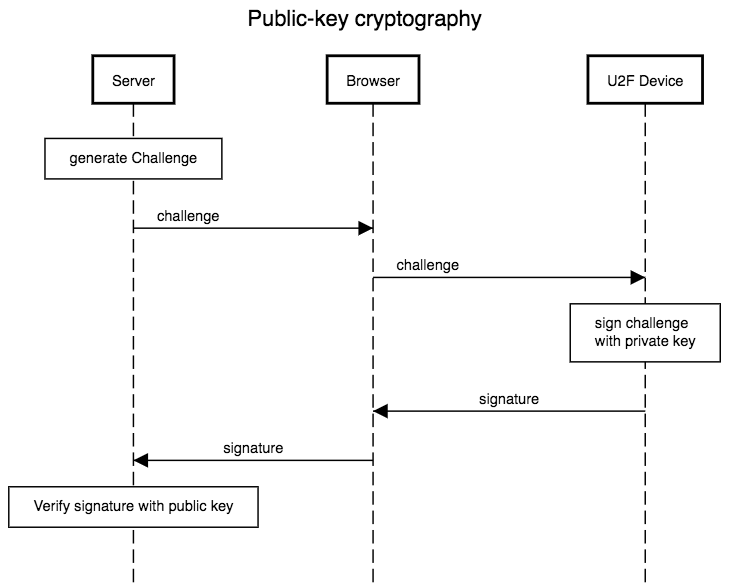
Starting from this sequence diagram, further functions and procedures of the U2F standard are explained below.
Phishing protection
In our picture above it would be easy to perform a phishing attack [4].
To prevent this from happening, this phishing protection procedure has been developed:
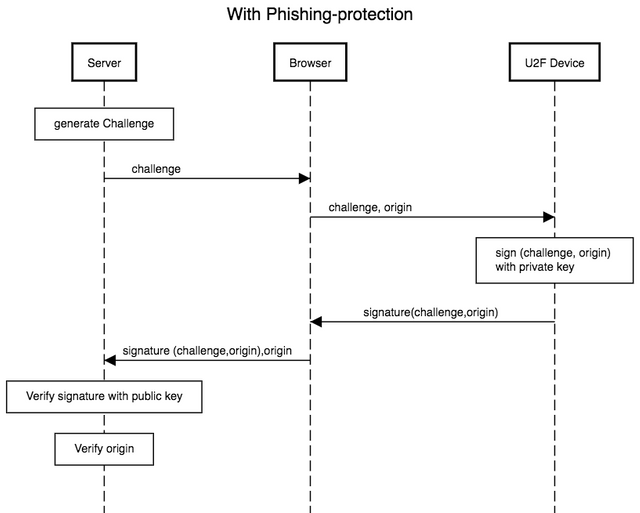
Due to the fact that in addition to the challenge, the origin is also signed by the device, the server is able to reject the authentication if a phishing attempt exists and this is therefore faulty.
Tracking protection
In the figure above, it is possible to track the user according to his or her key or to find out on which services he or she is using it. This is why we have added the following to our sequence diagram in this step:
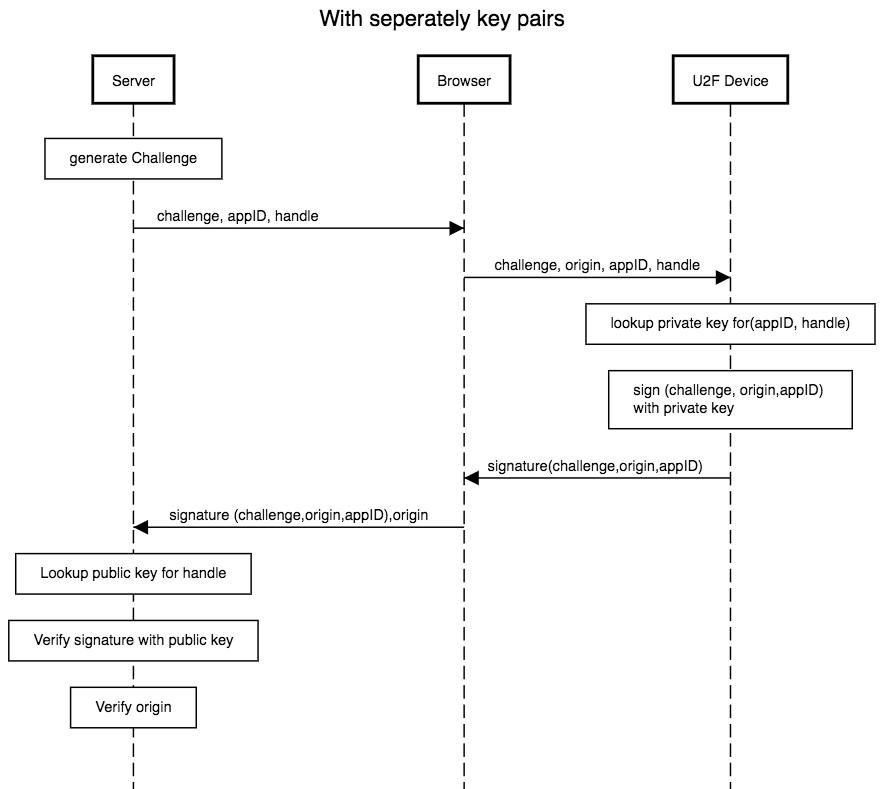
A separate key pair is used for each service. Using the appID and handles, the device can sign with the appropriate private key. This means that the device has no unambiguous external identification. Even if the login data of a service becomes public (for whatever reason).
Cloning protection
For this purpose, a counter (counter) is also implemented on the device, which increases with each signature.
The server stores the last counter value and checks whether it is higher than the previous one.
If this is not the case, there is a problem or the device has been cloned in some way.
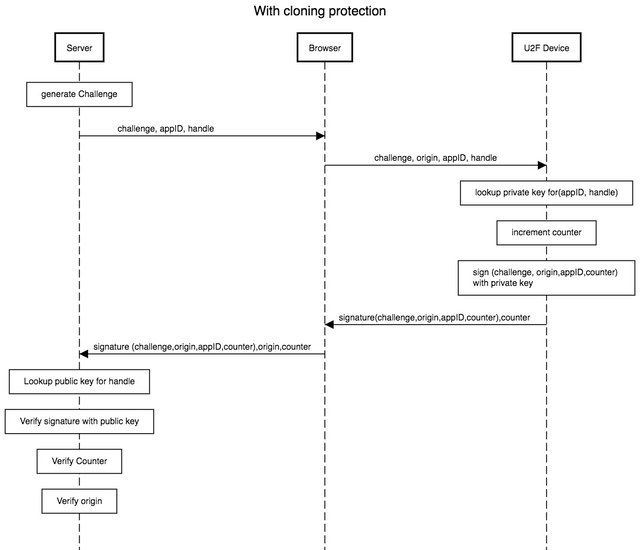
It should be noted that this solution does not always work. If the cloned device logs on to a service first, it is accepted. The extent to which there are other mechanisms for cloning protection at the hardware level is certainly dependent on the device in question.
Registration
Now I would like to illustrate the registration process here.
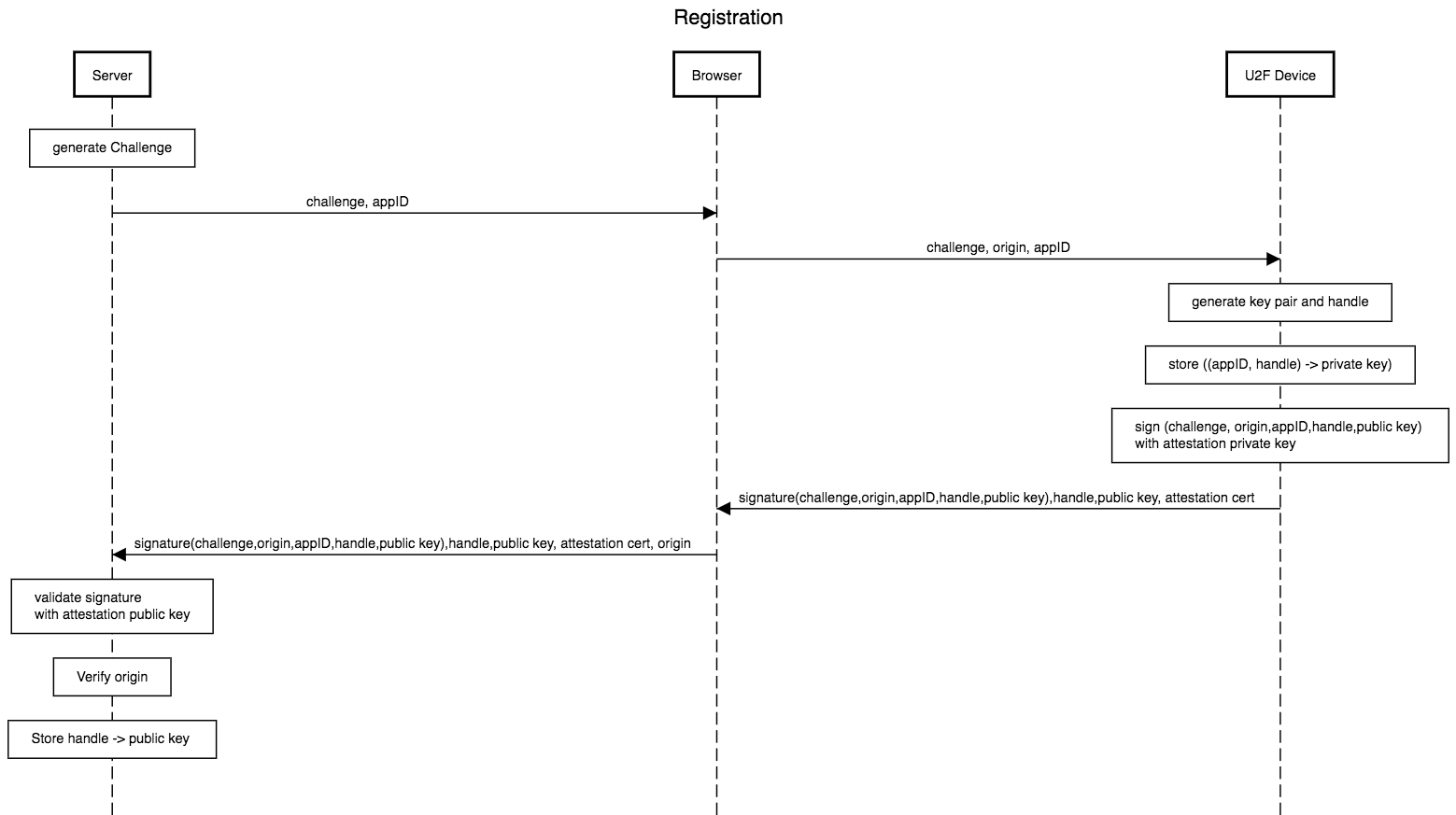
The public key transfer certificate corresponds to the X. 509 standard[5]. This is used for example when using HTTPS pages.
Example
Now that the basic procedure has been explained, I would like to illustrate it with a practical example. A test page[6] provided by the manufacturer yubico is recommended for testing.
A user name and password are selected for registration. You will then be prompted to confirm the operation physically on the U2F device.
The following data can be viewed during registration:
Login Data
username: security101_U2F_test
password: vCRz2%)PxuRBAMu83UfkT$/MmreXZ{
Registration Data
origin: https://demo.yubico.com
version: U2F_V2
challenge: fIqqz7ymVeuNmq4A89X0wA47dlETvHQg4npm69kKmiY
appId: https://demo.yubico.com
Response Data
clientData: {"typ":"navigator.id.finishEnrollment","challenge":"fIqqz7ymVeuNmq4A89X0wA47dlETvHQg4npm69kKmiY","origin":"https://demo.yubico.com","cid_pubkey":"unused"}
registrationData: 0504dcb4c288b614c28e8d175cee743a8cffa2a52d6b044148add5e3f84cac432b09093b44310b44d49a31d737e47d5af6b36f59a8b35c2345e5f0bd9f1a6df7367840ba92cc8a5f03f2ec9252fa92eab579bce62923b7613ba1d897a0531bbcf6b6f48b3d93eb5d823fe55ee7ed66da8bd11c06ea62a5d57d7006f625620aaea9613a3082015d30820103a003020102020121300a06082a8648ce3d04030230273125302306035504030c1c4c6564676572204649444f204174746573746174696f6e2043412031301e170d3136303732313133333633375a170d3236303730393133333633375a3030312e302c06035504030c254c6564676572204e616e6f2d5320553246204174746573746174696f6e20426174636820313059301306072a8648ce3d020106082a8648ce3d0301070342000423c27f2c89f642caa2acafd8914c7aa6d3e2c04b37125df69a16867258ec404630980bf89c432ce689efec046f5a5cf461d02335a08384987860e1fcd70cd387a31730153013060b2b0601040182e51c020101040403020520300a06082a8648ce3d040302034800304502207a1a27a2cbde2978826be0fdbd4ca85e3f6e3f72417c5968dba9407e60c46a140221008f2aff7afeff55cf8fced7f579cfec9c87940aa5442560c6e79f3da01aaa6a423045022100d5c80f0b83529936daf50d1c8cfebbc0b7f35111f2168678b5ff95b7ba51d5da02204c56aa2039974cc7c3dd1e3ded876346a957c637fd85fc04f6f403cd912d9fb1
Attestation Certificate
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 33 (0x21)
Signature Algorithm: ecdsa-with-SHA256
Issuer: CN=Ledger FIDO Attestation CA 1
Validity
Not Before: Jul 21 13:36:37 2016 GMT
Not After : Jul 9 13:36:37 2026 GMT
Subject: CN=Ledger Nano-S U2F Attestation Batch 1
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey
Public-Key: (256 bit)
pub:
04:23:c2:7f:2c:89:f6:42:ca:a2:ac:af:d8:91:4c:
7a:a6:d3:e2:c0:4b:37:12:5d:f6:9a:16:86:72:58:
ec:40:46:30:98:0b:f8:9c:43:2c:e6:89:ef:ec:04:
6f:5a:5c:f4:61:d0:23:35:a0:83:84:98:78:60:e1:
fc:d7:0c:d3:87
ASN1 OID: prime256v1
X509v3 extensions:
1.3.6.1.4.1.45724.2.1.1:
...
Signature Algorithm: ecdsa-with-SHA256
30:45:02:20:7a:1a:27:a2:cb:de:29:78:82:6b:e0:fd:bd:4c:
a8:5e:3f:6e:3f:72:41:7c:59:68:db:a9:40:7e:60:c4:6a:14:
02:21:00:8f:2a:ff:7a:fe:ff:55:cf:8f:ce:d7:f5:79:cf:ec:
9c:87:94:0a:a5:44:25:60:c6:e7:9f:3d:a0:1a:aa:6a:42
-----BEGIN CERTIFICATE-----
MIIBXTCCAQOgAwIBAgIBITAKBggqhkjOPQQDAjAnMSUwIwYDVQQDDBxMZWRnZXIg
RklETyBBdHRlc3RhdGlvbiBDQSAxMB4XDTE2MDcyMTEzMzYzN1oXDTI2MDcwOTEz
MzYzN1owMDEuMCwGA1UEAwwlTGVkZ2VyIE5hbm8tUyBVMkYgQXR0ZXN0YXRpb24g
QmF0Y2ggMTBZMBMGByqGSM49AgEGCCqGSM49AwEHA0IABCPCfyyJ9kLKoqyv2JFM
eqbT4sBLNxJd9poWhnJY7EBGMJgL+JxDLOaJ7+wEb1pc9GHQIzWgg4SYeGDh/NcM
04ejFzAVMBMGCysGAQQBguUcAgEBBAQDAgUgMAoGCCqGSM49BAMCA0gAMEUCIHoa
J6LL3il4gmvg/b1MqF4/bj9yQXxZaNupQH5gxGoUAiEAjyr/ev7/Vc+Pztf1ec/s
nIeUCqVEJWDG5589oBqqakI=
-----END CERTIFICATE-----
After this registration it is possible to login. To do this, enter the user name and password again and confirm it with the U2F device when prompted.
Upon successful login, the following data can be viewed:
Login Data
username: security101_U2F_test
password: vCRz2%)PxuRBAMu83UfkT$/MmreXZ{
Challenge Data
version: U2F_V2
challenge: EukOIwh52fC_LRMcS3B9HXrPA3Yw_RDaOZ0BOUOZUU0
keyHandle: upLMil8D8uySUvqS6rV5vOYpI7dhO6HYl6BTG7z2tvSLPZPrXYI_5V7n7Wbai9EcBupipdV9cAb2JWIKrqlhOg
Response Data
clientData: {"typ":"navigator.id.getAssertion","challenge":"EukOIwh52fC_LRMcS3B9HXrPA3Yw_RDaOZ0BOUOZUU0","origin":"https://demo.yubico.com","cid_pubkey":"unused"}
signatureData: AQAAAAMwRAIgbYpkN7QL5GJn4y3p4OrbnvQhF9Po12H1-nzh5G2yb4gCIBLmxlUoR2RwEtIYQe_VXHej0eaKuUwhwI-pLzerPY3R
Authentication Parameters
touch: true
counter: 3
U2F Devices

Source
I don't want to make any recommendations at this point, because I have little insight into the implementation of the hardware. Nevertheless, I would like to introduce a small selection of U2F devices I know:
Sources and further links
- (1) https://fidoalliance.org/
- (2) http://www.dtic.mil/dtic/tr/fulltext/u2/a408338.pdf
- (3) https://de.wikipedia.org/wiki/Challenge-Response-Authentifizierung
- (4) https://de.wikipedia.org/wiki/Phishing
- (5) http://www.rfc-editor.org/rfc/rfc2459.txt
- (6) https://demo.yubico.com/u2f
- https://www.youtube.com/watch?v=vv11XMG5UJg
- https://blog.trezor.io/secure-two-factor-authentication-with-trezor-u2f-e940fd5a60af
- https://fidoalliance.org/specs/fido-u2f-v1.2-ps-20170411/FIDO-U2F-COMPLETE-v1.2-ps-20170411.pdf
- https://www.nitrokey.com/files/doc/Nitrokey_FIDO_U2F_Infoblatt.pdf
- https://github.com/conorpp/u2f-zero/wiki
- https://github.com/google/u2f-ref-code
- https://fidoalliance.org/how-fido-works/
- https://github.com/conorpp/u2f-zero/wiki
(*) All links were seen on 12.02.2018 between 08:00 and 16:00 o' clock. At that time I wrote this article in German

I would like to point out that I only wanted to give a rough overview and some details have been ignored.
Thank you for reading !
Great thanks for this detailed explanation about U2F. I use a Nano Ledger as a cold storage but without the U2F option because I was thinking that a hardwarewallet by itself is pretty secure enough. So do you think that U2F should be always used even with Nano Ledger or is it just mandatory for those who need some kind of extra potection?
Thank you very much!
If you use the ledger as cold storage, this is a secure way to secure your coins.
U2F is an easy way to implement a factor in authentication processes. This is not necessarily necessary.
However, it is important to use 2 factors of authentication in any way.