Cryptographic Hash Function: A Simple Introduction
The most versatile cryptographic algorithm is the cryptographic hash function. The cryptographic hash function is widely used in variety of security applications and Internet protocols. And here I am going to give a very basic idea of what it really is.
Hash Function:
A hash function H accepts a variable - length block of data M as input and produces a fixed size hash value h=H(M). A "good" hash function has the property that the results of applying the function to a large set of inputs will produce outputs that are evenly distributed and apparently random.
Cryptographic Hash Function:
This term is not new. The hash function that are commonly used for security related applications are cryptographic hash functions. A cryptographic hash function is an algorithm for which it is computationally infeasible to find either:
- Data object that maps to a pre-specified hash result (also known as the one-way property).
- Two data objects that map to the same hash result (also known as the collision-free property).
Cryptographic hash functions are used to do message integrity checks and digital signatures in various information security applications, such as authentication and message integrity.
There is no formal definition which captures all of the properties considered desirable for a cryptographic hash function. These properties below are generally considered prerequisites:
1. Preimage resistant:
Given h it should be hard to find any m such that h = hash(m).2. Second preimage resistant:
Given an input m1, it should be hard to find another input, m2 (not equal tom1) such that hash(m1) = hash(m2).
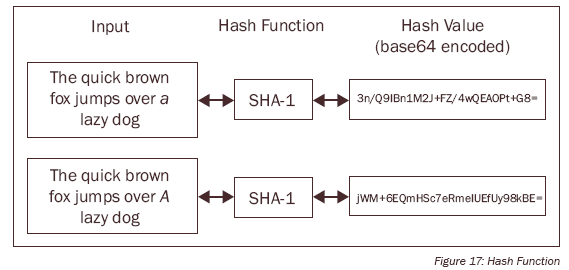
The above figure depicts a simple operation of cryptographic hash function. There are several cryptographic hash function in present context. Some of them are:
1. Message Digest (MD) Algorithm
A message digest takes an input of arbitary length and produces an output as digest or hash of the input. The output is much shorter than input so that processing and storing can be done fastly. The message digest algorithms were all developed by Ronald Rivest during 1989 to 1991. Its vsersion are:
I. MD2
MD2 was developed in the year 1989 by Ronald Rivest to be run on 8-bit machines. It was used to verify data integrity by producing 128-bits message digest from input data and using along with digital signatures. It is rarely used in today's time because it takes considerably a long time to produce message digest or hash value. Also it could leak information of key using collision attacks.
II. MD4
MD 4 Algorithm is a cryptographic hash function developed by Ronald Rivest in 1990. It produces 128 bits (four 32 bits words) message digest and is optimized for 32-bit computers. But this hash function was suspectible to cryptanalytical attack. Collisions were easily found in this version in less than one minute using PC. So, Rivest proposed an improved version in 1991 that was called MD5.
III. MD5
MD5 was designed by Ron Rivest in 1991 to replace an earlier hash function, MD4. MD5 is a widely used hash function with a 128-bit hash value. An MD5 hash is typically expressed as a sequence of 32 hexadecimal digits. The attacks were said to have been reported to some extent. Attacks required to find out original message include 2128 bits operations. Attacks to try and find out two messages producing same MD require 264 bits operations.
The 128-bit (16-byte) MD2, MD4, and MD5 hashes (also termed message digests) are typically represented as 32-digit hexadecimal numbers. The following demonstrates a 43-byte ASCII input and the corresponding MD hash:
MD2("The quick brown fox jumps over the lazy dog")=03d85a0d629d2c442e987525319fc471
MD4("The quick brown fox jumps over the lazy dog")=1bee69a46ba811185c194762abaeae90
MD5("The quick brown fox jumps over the lazy dog")=9e107d9d372bb6826bd81d3542a419d6
Even a small change in the message will (with overwhelming probability) result in a completely different hash, due to the avalanche effect. For example, changing d to c:
MD2("The quick brown fox jumps over the lazy cog")=6b890c9292668cdbbfda00a4ebf31f05
MD4("The quick brown fox jumps over the lazy cog")=b86e130ce7028da59e672d56ad0113df
MD5("The quick brown fox jumps over the lazy cog")=1055d3e698d289f2af8663725127bd4b
2. Secure Hashing Algorithm (SHA)
In recent years of crytpocurrency and blockchain technology, the most widely used hash function has been the Secure Hash Algorithm as every other widely used hash functions had been found to have a substantial cryptanalytic weaknesses. SHA was developed by the National Institute of Standards and Technology (NIST) and published as a federal information processing standard (FIPS 180) in 1993. The family of SHA includes many versions which are:
I. SHA - 0
Published in the year 1993, the collisions attacks were found on 261 operations during 1998. Further on 2005, the collisions attacks was done on 236 operations and breaks hash function desirbale properties of preimage resistant and second preimage resistant ( I have described about it above).
II. SHA - 1
When a message of length < 264 bits is input, the SHA produces a 160-bit representation of the message called the message digest. The SHA -1 is designed to have the following properties: it is computationally infeasible to recover a message corresponding to a given message digest, or to find two different messages which produce the same message digest. It's design closely models MD5 hash algorithm. It was developed by National Security Agency (NSA) to be part of Digital Signature Algorithm but was rejected for use after 2010 when cryptographic weaknesses were found on it.
III. SHA - 2
In 2002, NIST produced a revised version of the standard, FIPS 180-2, that defined three new versions of SHA, with hash value lengths of 256, 384, and 512 bits, known as SHA-256, SHA-384 and SHA-512, respectively. Collectively these hash algorithms are known as SHA-2. These new versions have the same underlying structure and use the same types of modular arithmetic and logical binary operations as SHA -1.
Steemit uses SHA-256 hash algorithm for security appliance. Beside that SHA 256 just has 256 bit on hash value. It is shorter than SHA 512. Because of that SHA 256 hash faster speed than SHA 512 but SHA 256 hash a good security. Other coins which use SHA-256 hash algorithms are:
- Bitcoin
- BitcoinCash (BCH)
- Peercoin
- Neos Coin
- Pascal Coin
- Cure Coin...........................and many more. You can find out here Cryptocurrencies hash algorithms
Applications of Cryptographic Hash Function:
To better understand some of the requirements and security implications for cryptographic hash functions, it is useful to look at the range of applications in which it is employed.
1. Message Authentication
Message authentication is a mechanism or service used to verify the integrity of a message. Message integrity means the message send has not been modified, changed, altered or tampered. Message authentication assures that data received are exactly as senti.e., there is no modification, insertion, deletion or replay. In many cases, there is a requirement that the authentication mechanism assures that purported identity of the sender is valid.
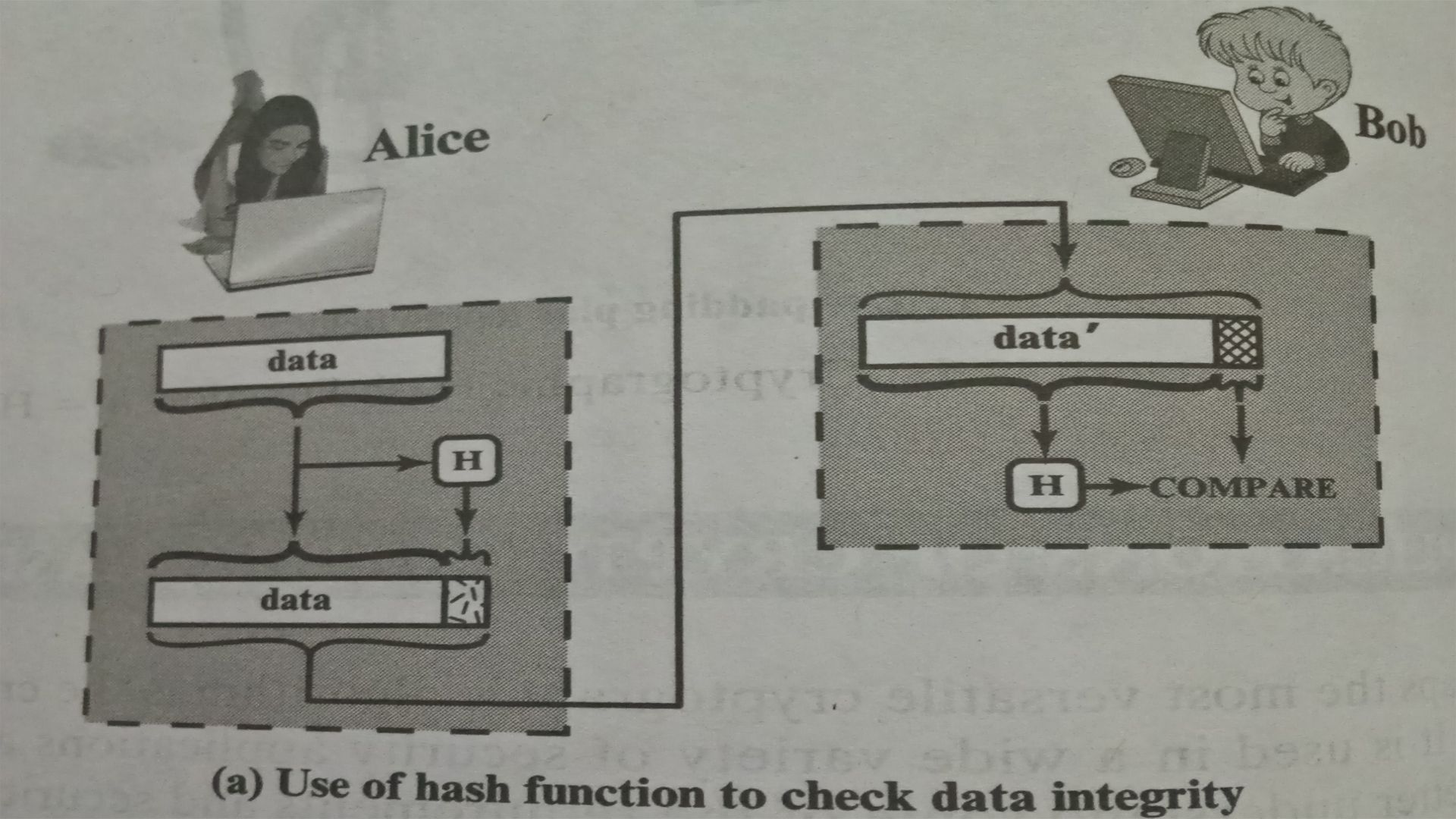
The essence of the use of a hash function for message integrity is as follows. The sender computes a hash value as a function of bits in the message and transmits both the hash value and the message. The receiver performs the same hash calculation on the message bits and compares this value with the incoming hash value. If there is a mismatch, the receiver knows that the message has been assured.
The hash value must be transmitted in a secure fashion. That is, the hash value must be protected so that if an adversary alters or replaces the message, it is not feasible for adversary to also alter the hash value to fool the receiver. This type of attack is shown here:
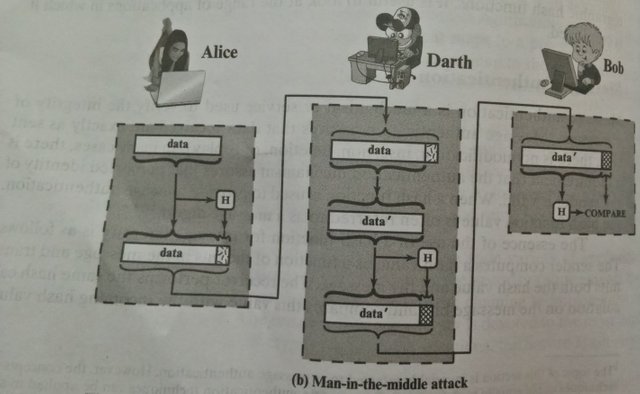
Alice transmits a data block and attaches a hash value. Darth intercepts the message, alters or replaces the data block, and calculated and attaches a new hash value. Bob receives the altered data with the new hash value and does not detect the change. To prevent this attack, the hash value generated by Alice must be protected. This type of attack against hash function is known as the "Man in the middle attack(MITM)"
2. Digital Signature
Digital signature is a mechanism of assuring that the digital documents or messages is authentic i.e., the message was created by a known sender. It is a generated by public key encryption scheme as a digital code and is embedded to electronic documents to ensure confidentiality and integrity of message.
The operation of digital signature is similar to message authentication code (MAC). In the case of digital signature, the hash value of a message is encrypted with a user's private key. Anyone who knows the user's public key can verify the integrity of the message that is associated with the digital signature. In this case, the attacker who wishes to alter the message would need to know the user's private keys. The following figure shows a simpler model of digital signature:
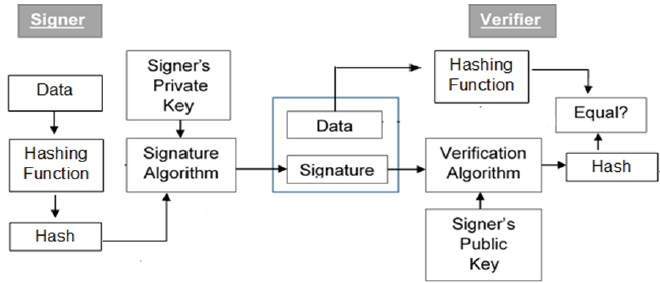
Here the hash code which is obtained by applying hash function to a data or original message is encrypted, using public-key encryption with the signer's private key. And together with encrytped hash code and signature algorithm a signature is produced. This signature and an original data is input to receiver's or verifier's side. The verifier's side also computes hash of the data. The signer's public key is known to receiver's and he performs verification of signature with this public key and signature produced by sender and computes hash. If this hash value matched to hash value calculated with original data by receiver, the verifier decides that the digital signature is valid. The digital signature also provides for non-repudiation of message i.e., a sender can present his digital signature as evidence in future in case of dispute arises to third party or Court of Certification Authority.
So I will limit the topic on the basic of hash function only as this post had become too lengthy. In my next article, I will be writing about Message Digest (MD) operations and other related topics.
References
Pearson's Crytpography and Network Security (By William Stallings)
https://www.tutorialspoint.com/cryptography/cryptography_digital_signatures.htm
steemstem:

SteemSTEM is a community driven project which seeks to promote well-written and informative Science, Technology, Engineering and Mathematics (STEM) posts on Steemit. The project involves curating STEM-related posts through upvoting, resteeming, offering constructive feedback, supporting scientific contests, and other related activities.
DISCORD: https://discord.gg/j29kgjS
Informative post! I learnt alot. I will be waiting for more details on Message Digest (MD)
Thank you sir for your time and consideration in reading this post. Your comment is much appreciated. Will be writing on post about Message Digest (MD) very soon. I will be informing you sir when I post.
You have a broken link and the book is copyrighted meaning you are very very likely breaking copyright laws with those pictures
@kryzsec, the link has been fixed and I have mentioned the source of picture. Will that be okay🙂?
Wonderful introduction...nice attempt
Thank you sir🙂