[Cryptography Episode 3] Classical Cipher - Substitution
In transplanion cipher we saw ways to change the position of the letters to create ciphertext. Substitution cipher is an alternative to this. In this type of cipher, the letters are not changed, but the letters are changed! One such example of cipher is Caesar Cipher, whose first user is Julius Caesar himself!
Caesar Cipher
What Julissa Caesar used to do is, instead of every letter in a plain text, it would place a color next to its three cells. Such as:
A becomes D, B becomes E.
Just think about Z, what will happen?
Z will be replaced by C!
So let us see, what will be the cipher text of "SHOSHIKKHA"?
S V
H K
O R
S V
H K
I L
K N
K N
H K
A D
Then the whole word is standing "VKRVKLNNKD"
What is the name of a pretty name is a situation of what is going on. Hey, this is the purpose of making cipher text!
Caesar backtracked three words. If we want to give two, four which can be happy, we can give it back! But one thing is that, in the Roman alphabet (or English), going to the house of 25 houses, the same thing as going back a house! Again, if we forward 13 to A, we get 14 letters of the letter. Again, A will be left behind one room Z (26), this Z is left to the left (13-1) behind the 14th. That is, the pattern is going to get the same letter in front and behind: If x is given the same letter behind the front and y, then x + y = 26 () is the total number of letters.
Now those who cross the programming, let's write down a C code encryption-decryption!
/ * The purpose of this is to increase interest in junior programming. But if you do not have patience then you can skip this piece. It will not affect the cryptography discussion later! * /
Our advantage is that, according to Caesar cipher, there may be a maximum of 25 types of cipher texts written in English. We will generate 25-separate text for decryption and see what is meaningful! And encryption is more straightforward. Tell the user how to forward or backward how many cells will be left behind. Then I will work accordingly. So let's start working by not talking!
Our first task will be to create a user interface. The user who asks the user, wants to encrypt or decrypt it. Then we will create an if-else if-else ladder. If he wants to encrypt, I'll work accordingly. Encrypting to decrypt. And if you put the wrong input, he will (Bharati) understand his mistake and return to the beginning!
So the basic structure of our code will be as follows
#include <stdio.h>
int main() {
printf("What operation do you want to execute?\n");
printf("Press 1 for Encryption.\n");
printf("Press 2 for Decryption.\n");
int i;
scanf("%d", &i);
if (i==1) {
}
else if (i==2) {
}
else {
printf("Vai thik moto input den na ken? :'(\n");
printf("Abar notun kore shuru koren!\n\n");
// nicher kaj ta interesting na? Ki hobe bolo to? :p
main();
}
return 0;
}
This is the beginning of our original work. Press 1, we will do encryption. At the beginning of the encryption we need to know whether he wants to move forward or get back, and how many cells he wants to move. So we'll know it from the user with the help of two variables.
if (i==1) {
int daanebaame, kotoghor;
printf("Forward or backward?\n");
printf("Press 1 for Forward.\n");
printf("Press 2 for Backward.\n")
scanf("%d", &daanebaame);
printf("How many positions to move?\n");
scanf("%d", &kotoghor);
// nicher kaj ta keno korchi bolo to?
if (daanebaame == 2) {
kotoghor = 26-kotoghor;
}
}
Here's why I'm doing the work below "nicher kaj ta keno korchi bolo to?" Because we know that going back to the x, the 26-x house is going to be the same thing! So we just want to get rid of the code going forward!
However, if the user is saying that the biggest inference of this code is 1 room, we will go to the front of 25 rooms! That means 25 times more work to us! Although it is very harmful, I do not want to do too much work idle!😉
Your work will be written separately in the code in front of the two sides. Can not you?
Now the rest of our work is:
First, take the input using get (). We will not have more than 100 characters in size.
As far as you are saying, remove the letters as far as possible. If it goes beyond Z, then use Z to Z as it takes, leaving the remaining cells A from A. The job is simple. Suppose we have our checkered letter ch variables. We will check in ASCII whether ch + kotoghor> 'Z' is not. If this is true, then we will write c '' A '+ kotoghor - (' Z'-ch) of the cipher text!
Having trouble understanding? Hold our current color ch = X
kotoghor = 5
Then ch 'will be value, ch' = 'A' + 5 - ('Z' - 'X') = 'A' + 5-2 = 'D'
Now let's finish the encryption code
if (i==1) {
int daanebaame, kotoghor;
printf("Forward or backward?\n");
printf("Press 1 for Forward.\n");
printf("Press 2 for Backward.\n");
scanf("%d", &daanebaame);
printf("How many positions to move?\n");
scanf("%d", &kotoghor);
// nicher kaj ta keno korchi bolo to?
if (daanebaame == 2) {
kotoghor = 26-kotoghor;
}
char plaintext[100];
char cyphertext[100];
getchar(); // eta dite hoyeche ekishathe gets ar scanf use korar karone. google korle aro jante parbe!
gets(plaintext);
int a,len = strlen(plaintext);
for (a=0; a<len;a++) {
if (plaintext[a] + kotoghor<='Z') cyphertext[a] = plaintext[a] + kotoghor;
else cyphertext[a] = 'A' + kotoghor - ('Z'-plaintext[a]);
}
cyphertext[len] = '\0';
printf("Your desired Encrypted text is:\n%s\n", cyphertext);
}
This time the decryption! This is a simple task. We will give up to 25 possible plain text output in 25 lines with just one text input. Without giving up the code, I give it directly! Our decryption code is such
else if (i==2) {
char cypher[100], plain[100];
getchar();
printf("Cypher text please?\n");
gets(cypher);
int ghor,a,len = strlen(cypher);
for (ghor=1; ghor<=25;ghor++) {
printf("Forwarding %d position: ", ghor);
for (a=0; a<len; a++) {
if (cypher[a] + ghor<='Z') plain[a] = cypher[a] + ghor;
else plain[a] = 'A' + ghor - ('Z'- cypher[a]);
}
plain[len] = '\0';
printf("%s\n", plain);
}
}
The whole code will be available in this link .
Come back to our original discussion!
Kamasutra Cipher:
One of the earliest signs of encryption is the Cemetery Cipher. Kamsutra was written in the fourth century AD. It was based on the manuscript of the fourth century BC, that is, about 2,500 years ago today!
In this Kamasutra, women were asked to be skilled in 64 different industries. This list is like a chess game, as well as the 45-th industry name is mlecchita-vikalpa. This mlecchita-vikalpa's English is The Art of Secret Writing! There are several types of encryption methods in Kamasutra.
In one of the first, there are several pairs of alphabets. I do not know Sanskrit, so I have given examples in English. There are 26 characters in English. So, it can be possible to pair in 13. Again this pair can be made possible by 26C2!
After the pairing, each letter of the plain text is replaced by a different color according to its pair! For example, I have a pair of M and N. Then I'll write where I am, N. And where you get N, I'll write M!
MonoAffectic Cipher
Another type of cipher method is to create a new scale. For example, the basic order of the alphabet is:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
So, I want to make my cipher text in the first place. So I made the opposite as happy
X Y Z A B C G F E D M N O K J V T R S U Q P W I J H
So now say "SHOSHIKKHA" - what will happen? For convenience, these two lines are written afterwards
Real: A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
Fake: X Y Z A B C G F E D M N O K J V T R S U Q P W I J H
You can see, SHOSHIKKHA is going to become SFJSFEMMFX!
One advantage of this type of cipher is the 26-alphabet alphabet can be redesigned to 26! -1, which is more than 400,000,000,000,000,000,000,000,000,000! If you do not know the alphabet order, then it's hard to guess!
With 26 shifts of Caesar cipher, 26 types of alphabets are found in such a format
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
B C D E F G H I J K L M N O P Q R S T U V W X Y Z A
C D E F G H I J K L M N O P Q R S T U V W X Y Z A B
D E F G H I J K L M N O P Q R S T U V W X Y Z A B C
E F G H I J K L M N O P Q R S T U V W X Y Z A B C D
F G H I J K L M N O P Q R S T U V W X Y Z A B C D E
G H I J K L M N O P Q R S T U V W X Y Z A B C D E F
H I J K L M N O P Q R S T U V W X Y Z A B C D E F G
I J K L M N O P Q R S T U V W X Y Z A B C D E F G H
J K L M N O P Q R S T U V W X Y Z A B C D E F G H I
K L M N O P Q R S T U V W X Y Z A B C D E F G H I J
L M N O P Q R S T U V W X Y Z A B C D E F G H I J K
M N O P Q R S T U V W X Y Z A B C D E F G H I J K L
N O P Q R S T U V W X Y Z A B C D E F G H I J K L M
O P Q R S T U V W X Y Z A B C D E F G H I J K L M N
P Q R S T U V W X Y Z A B C D E F G H I J K L M N O
Q R S T U V W X Y Z A B C D E F G H I J K L M N O P
R S T U V W X Y Z A B C D E F G H I J K L M N O P Q
S T U V W X Y Z A B C D E F G H I J K L M N O P Q R
T U V W X Y Z A B C D E F G H I J K L M N O P Q R S
U V W X Y Z A B C D E F G H I J K L M N O P Q R S T
V W X Y Z A B C D E F G H I J K L M N O P Q R S T U
W X Y Z A B C D E F G H I J K L M N O P Q R S T U V
X Y Z A B C D E F G H I J K L M N O P Q R S T U V W
Y Z A B C D E F G H I J K L M N O P Q R S T U V W X
Z A B C D E F G H I J K L M N O P Q R S T U V W X Y
The beautiful 26x26 square is named Vigenère square!
Pipe cipher:
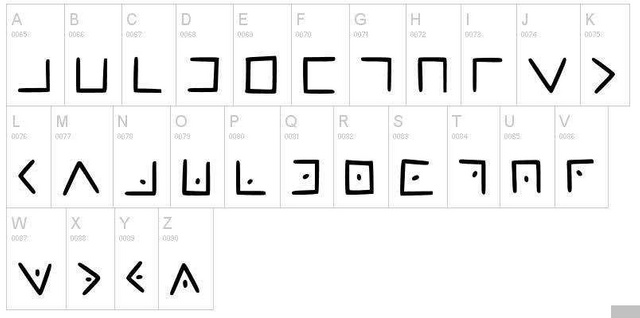
Those who are familiar with the Robert Langdon series, they must have heard the name of Free Mason. The frescens are mentioned in The Lost Symbol. So these freemasons used a kind of cipher to keep their documents safe. Its name is Pigpen Cipher.
In such a cipher the letters were not replaced by letters, but replaced by symbol. Take a look at the picture below to understand the pattern of these symbols
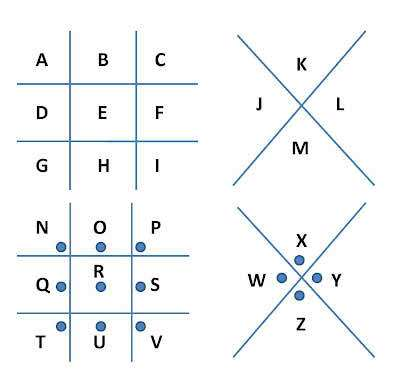
At first the letters were arranged in this way. Now seeing the picture below, hopefully how can you get the marks from the letters!