What exactly is DDoS attack? How it works?What are its types?What are its protection option?
Hello Steemit Friends,

As we all know Steemit was under DDoS attack due to which we all faced slowness issue. But do you know what is a DDoS attack? Do you know how DDoS attack works?What are its types?And how it can be protected? If you have no idea on this, then don't worry as in this post I have mentioned everything you want to know about DDoS attack.
What is the DDoS attack?

DDoS is Distributed Denial Of Service attack. It is a type of a cyber-attack in which perpetrator attempts to make a server, website, and other network resources unavailable to their users by overwhelming it with unwanted traffic from multiple sources. This actually takes place when any cyber hacker temporarily or indefinitely disrupts services of a host connected to the internet.
In order to overload the systems, perpetrator targets the machines or resources with supernumerary malicious and infected requests. This excess flow of infected data results as inaccessibility for the genuine visitors of that particular resource.
How DDoS attack works?
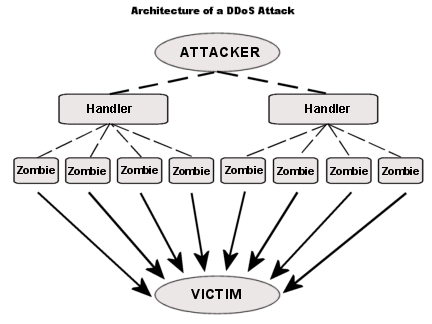
This massive attack begins by introducing the vulnerability in a single computer system and setting it as DDoS master. The DDoS master system identifies and gains control over other vulnerable or already infected systems. Master system does the job of gaining control by either infecting the systems with malware or through bypassing the authentication controls.
Let’s move to the detailed mechanism of DDoS attacks. Definitely, these types of attacks are performed by the hacker and the team of hackers to get any website down. But these hackers are not alone who go through with it, they have a complete army of infected systems connected to the internet. This group of infected devices called botnet. And It will be shocking for you to know that maybe your laptop, computer, router, webcam, and any other smart device which works on the internet or connects with internet can be a part of a botnet. Our system can be a part of Botnet when any malware through malicious software, email or download link gets install in our system and gives the permission to that hacker to control our system remotely. In this case, a hacker will use our system as a part of his malicious activities such as DDoS attacks. Just like this, the hacker gains control over millions of devices connected to the internet worldwide. By using these devices, the hacker sends the huge amount of unwanted requests to the targeted system (server) in order to crash that system completely which results in complete breakdown. This happens because unwanted requests create the undesirable traffic which crosses the limit bandwidth of that server.
What are the different types of DDoS attacks?

Generally, DDoS attacks can be divided into three types:-
• Volume-based attacks
• Protocol attacks
• Application layer attacks
Volume-based attacks include UDP floods, ICMP floods, and other packet floods. The main aim of this attack is to consume the total bandwidth of the targeted site.
In Protocol attacks SYN floods, fragmented packet attacks, Ping of death and Smurf DDoS etc. are included. The objective of these attacks is to create malfunction inside the intermediate communication equipment, such as firewalls and load balancers.
If we talk about Application layer attacks, It includes low-and-slow attack, GET/POST floods, attacks that target Apache, Windows or open BSD vulnerabilities etc. The attacks are done with an eye to crash the web server.
Some common DDoS attacks types:-
UDP Flood
A UDP flood can be any DDoS attack which floods the target with User Datagram Protocol (UDP) packets. This attack floods the random ports on a remote host and ultimately host replies with an ICMP “Destination Unreachable packet” due to repeated checks for the application. This process exhausts the resources of the host completely.
ICMP (Ping) flood
The principle of this attack is similar to UDP flood attack, ICMP flood overloads the target resource by bombarding it with packets (ICMP echo request packets). This attack destroys the incoming and the outgoing bandwidth.
Slowloris
Slowloris is a type of web server chain destruction attack which enables one web server to take down another server. This attack doesn’t affect the other services or ports on the aimed network. Slowloris makes a large number of active connections to the targeted web server and keeps them open for as long as possible. Slowloris never completes a request even after constantly sending the superfluous HTTPS headers. The targeted server keeps each of these false connections open. These unwished open connections lead to the denial of other connections from genuine clients.
HTTP Flood
In HTTP floods malformed packets spoofing or reflection techniques are not used. And it requires very less bandwidth in comparison to any other DDoS attack to bring the targeted site down. These types of attack begin with the exploitation of HTTP GET or POST requests. In response to every single request, it forces the server to allocate the maximum resources possible which ultimately results as a slowdown.
Internet Of things and DDoS attacks
As the number of internet connected devices is increasing with the pace of technology. These devices are giving an instance to the hackers in easy creation of botnets. Nowadays devices are available in every part of the world which also provides ease in the successful creation of malicious networks like Botnet.
Overall we can say that IoT (Internet Of Things) may be useful to their genuine users but in some way, they are more helpful to DDoS attackers.
Difference between DoS and DDoS attacks:-
DoS (Denial of Service) attack is much different from a DDoS(Distributed Denial of Services) attack.
In DoS attack, only a single internet connected computer system is used to flood a targeted resource or system. But in DDoS attacks, multiple computer systems and internet connections are used to slow or bring down the targeted server or resource.
Why are DDoS attacks so Dangerous?

• Attack Diverts the genuine audience
• Regular DDoS attack decreases the ranking of the website
• The main threat is for the organizations and business websites due to arrival of glitches in the projects due to attack
• It requires a big time to get overcome from an attack and maintaining the old reputation on the web.
DDoS mitigation Strategy:-

The term “DDoS mitigation” refers to the prevention of DDoS (Distributed Denial of Service) attacks. A healthy mitigation strategy includes these four stages.
- Detection
The identification of the malicious flow of traffic that may be the signal of DDoS assault. It is necessary to detect the attack as early as possible. - Diversion
Changing the path of the traffic from its target, either to be filtered or completely discarded. - Filtering
Filtering is effective when you are able to block an attack without taking your users into the trouble. - Analyses
Analyses are spanking when a detailed security log of the attack is maintained. Security logs should be able to give the all necessary information about the attack.
DDoS protection options

There are many services available online which provides protection against DDoS attacks. These protection service providers effectively secure all components and important data. You have to just go to their site and register yourself for getting secured from DDoS attacks. A high amount is charged for getting the protection from attack.
Mere nam @scoutting
Hy @swaraj, this india song i dedicate to all india friends.
Please listen and vote and resteem
https://steemit.com/music/@scoutting/muskurane-by-arijit-singh-original-song-cover-by-scoutting-20171027t0449292z
its good news...now all will be aware of this cyber attacks also..