DDoS Protection: The Unique way to protect your Network from the attack of DDoS Botnet
How DDOS Works
I have been wondering for months what is it about attacks on webplatforms, and what are the way forwards. For years till this present moment websites have been attacked. For those that have experienced one, they will never wish to experience any again for the stress they went through before they could overcame it. It is never easy.
source
What is DDoS?
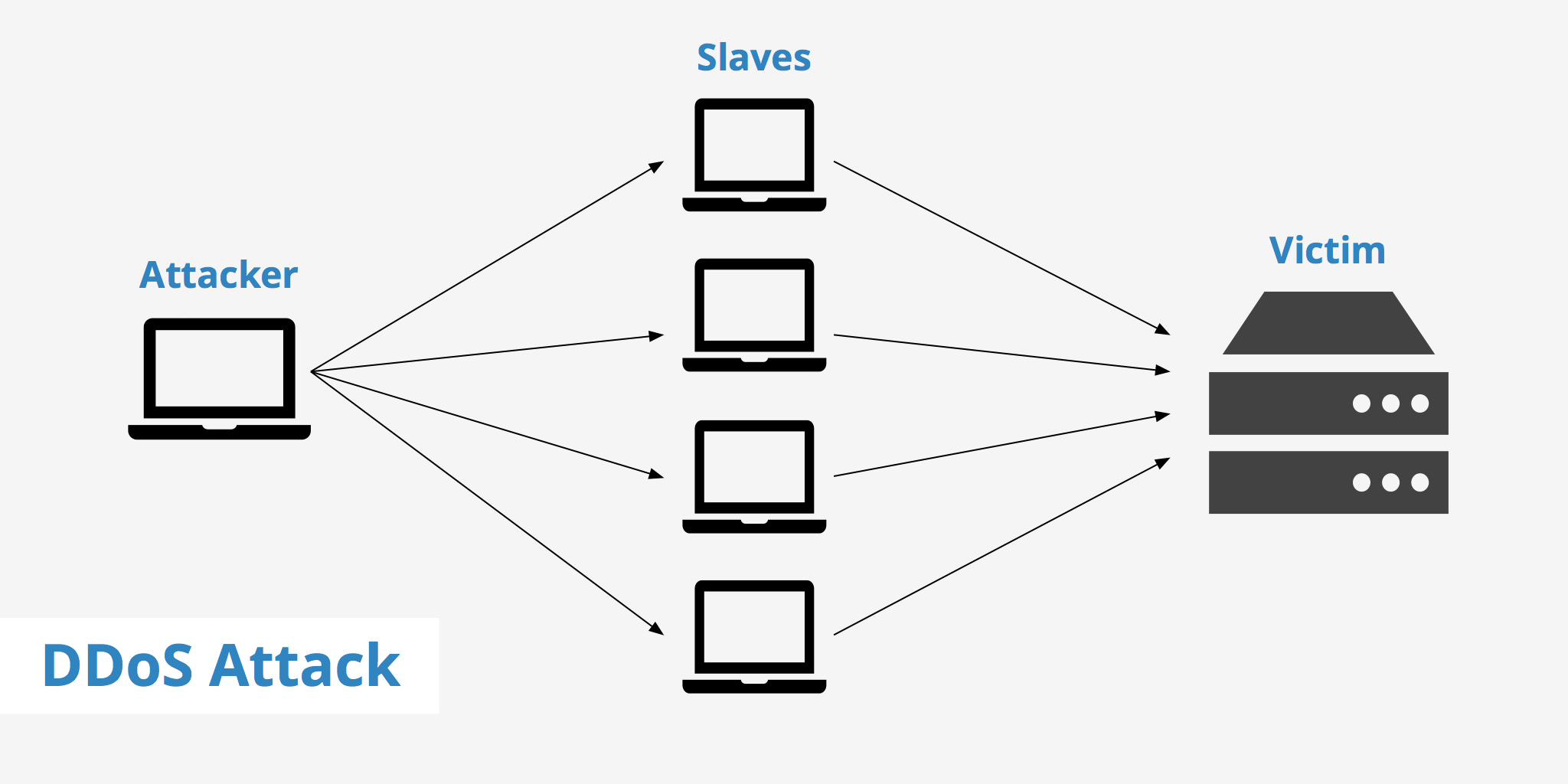
The acronyms stands for Distributed Denial of Service. It is one of the most common kind of cyber-attacks ever known.
According to Verisign: the global number of DDoS attacks is increasing to over 50millions per year.
Therefore, whenever this attack occurs, the victims will unable to access their systems and network resources, in most cases, disrupting the internet services and make it unbearable for the victims.
Distributed Denial of Service happen most of the time as a result of multiple compromised systems attacking a source. Thereby flooding your system with lots of unwanted traffic coming from those multiple systems and forcing your entire network or system to shut down and make it inaccessible and until you are able to find solution to it again.
It also can happen when a large number of organized bots typically known as botnet start attacking internet services. Malicious programs are been spread to vulnerable systems, either through attachments, emails, visiting untrusted and unprotected websites, in fact downloading from unknown and insecure websites which already has a network of infected botnet on them and thereby rushing in to your system like human virus and causing costly damages to it.
One of the popular botnets among millions for several purpose is ‘Mira, housing about 380,000 bots. It became very famous among others in 2016, when shutdown about a million German internet access and exploiting the weak security systems for several hours than expected. It is capable of infecting unsecure devices like IP cameras, DVRs, Computer networks, mobile phones and any other devices that make use of internet services.
Hackers find pleasure in using Distributed Denial of service to bring web services down from different reasons which might be for political, revenge, stealing and for different motive as they wish and for sort of illegal financial gain. Wicked people do pay hackers to them build botnet and execute it for the above mentioned motive, especially, revenge.
What is DDoS capable of?
One of the popular botnets among millions for several purpose is ‘Mira, housing about 380,000 bots. It became very famous among others in 2016, when shutdown about a million German internet access and exploiting the weak security systems for several hours than expected. It is capable of infecting insecure devices like IP cameras, DVRs, Computer networks, mobile phones and any other devices that make use of internet services.
How to diagnose if your system is been infected by DDoS Botnet
You may find it difficult to tell maybe your system is been infected by DDoS attack or not, especially when working with Internet Service Provider that does not have high reputation to protect. DDoS attack that are down in multiple location are used to cripple the internet service of systems from all types of domains. To find out may be you are a victim of not, follow the following procedure to find out:
- Open command prompt on your computer
- ping websites like google.com or ask.com for example
- use a particular orders and directions on your system to ensure the genuineness of the DDoS diagnosis on your system.
- type in “-n” command on the command prompt to specify the specific amounts of ping request you want the command prompt to execute
- you can use the perfection of “-t” command when it comes to continuous pinging of the outside world
- stop the pinging by pressing Ctrl + C, and then note the percentage of the packets lost displayed on the screen at the ping statistics below and also the number next to time.
After you have done all these steps, the bits fo information will give you clues of what has gone wrong with your service. The time column below represent the duration it takes for a 32-byte packet to transfer info from your system to the ping server e.g google and also the duration it takes to receive info back to your system. You can also use network analyzer tools to check for outbound traffic with huge packet size at fast interval.

source
How to Protect Your System form DDoS Attack
It is very difficult to eliminate this kind of attack, therefore it is very important and necessary that you have the right information on how you can defend your system from DDoS attack. Note: the following tips are not the only way with which you can protect your system from DDoS attack, these are just tips of the iceberg as you can source for more or sick advice from experts.
You do not have to wait until you will be attacked by DDoS, you have to put a counter measure in place like soldiers in defensive zone protecting their territory from infiteration of the enemies.
- Purchase DDoS protection products to defend loss of information and money due to attack
- Contact your ISP to know maybe they offer DDoS protection services, either free or paid.
- Ensure you have enough bandwidth. Because this will give you time to diagnose and get rid of any form of attack. And also enable server to accommodate traffics to reduce the intensity of the attacks.
- Set up secured VPS hosting for your website. This will reduce the probability of been attacked as you are provided with DDoS protection service. Another advantage is that VPS providers provide full access to console, which will give you the privilege to eliminate and diagnose any form of treat to your network.
- Purchase a Dedicated Server; purchasing a dedicated hosting server will give room for more bandwidth , as you are not on shared server. This will give you more security control over your server. While your users and customers has nothing to worried about.
- Blocked Spoofed IP Addresses.
- Use proxy protection
- Filter UDP Traffic to stop unwanted and malicious traffics that can cause harm to your system.
- Host your website on Cloud Service
You can always source for more information on the internet as there are numerous information that can help you out. Hope you find this content helpful. Please do not forget to upvote it and even if you can resteem. Thanks for reading.
This post has received a 0.63 % upvote from @drotto thanks to: @banjo.