Developing Key Box : Journal Entry for 2018 03(March) 12
March 12th, 2018
In this developer's journal of Key Box:
Usability with passwords and keys
Have you ever wondered why Steemit passwords are so long? For many typing in 52 letters and numbers is a task that requires patience and skill. Suppose you lose your place while typing, then you start all over again because the password does not appear as you type it in. If you get one letter wrong in your password, you can't get back in. The process can not tell if you are off by one letter, or completely off or using a password for another site or user. So, why do the software creators make things so hard?
What are they really for?
There are three scenarios we can imagine of people trying to get into your account:
- The attacker has access to your machine as an administrator
- The attacker has access to your machine as you
- The attacker has access to Steemit.com
- The attacker does not have access to your machine but can try to guess your password.
If you're trying to guard against someone who has admin access on your machine, forget it. You type in your password from paper to the screen and guess what? Your browser is a custom copy that records your passwords. Easy attack. Once an attacker is in the inner sanctum of your computer you cannot trust it.
Now, if an attacker has access as you, this attacker can record your keystrokes and save your passwords that way. In that case, they can get your password.
A typical user's computer has a double firewall. One inside the machine itself and the other NAT router box which connects to an ISP. Basically, all of the 65,000 doors that allow Internet traffic in are closed and only open for when you try to open something in an internet program of some kind. The problem is what you might be downloading and opening while you use the Internet.
I have heard dozen of times it is dumb to have a file called passwords.txt saved on the computer or use the clipboard to store the passwords. In these cases, the concern is that there is some kind of malware on the computer that could exploit this list of passwords. Well, if the malware is there, they can still keylog your passwords as you type them in. So, it really is of no consequence to have the passwords you need with frequency stored on the computer. Although, it might be a good idea to keep the passwords you do not use offline, backed up and stored in multiple places but in a secure way.
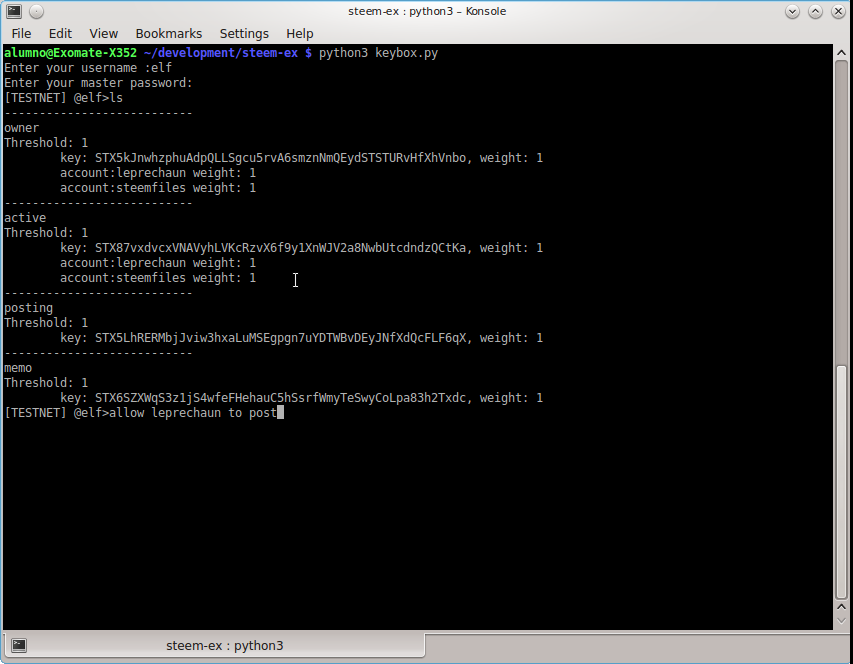
Now, Steemit.com, is different form your computer. It undoubtedly has firewalls but it cannot be steemit.com and block all of the ports to it at the same time. Why? Because as a service it has to be able to accept connections from people's machines to it. An exploit in the server software could compromise Steemit.com. The attacker would first have access as the www-data user, which shouldn't have access to write the binary files. There is no keylogging attack because nobody it typing on the Steemit.com machine itself, it's the various users' computers that have the keyboards. The passwords that people have are not stored by Steemit.com and they are not even sent to Steemit.com. So, the attacker would need to elevate its power from www-data user to the root user in order to replace files and start logging what people are typing in. Unless the attacker is someone working at Steemit Inc. For this, there is keybox, it will be able to change your password and then you can use your posting key to log into dtube.com, chainbb.com and steemit.com. Monetary active keys should be desktop programs like Vessel.
Finally, the last scenario is your password is hidden but anyone can validate any password in an automated way. So, an attacker can have put his computers guess your password thousands of times a second. It is like mining bitcoins but with the difficulty a lot higher than bitcoin. In fact, unless you chose your own password a hacker would be better off mining bitcoins than trying to guess a long 52 character password. There you have it, your passwords are so long because of this scenario and the other three require they have special access already, which may be impossible.
Brute forcing a password
You can see how long it could take to hack your password with the GRC Password Haystacks Page. I generated a password at steemit.com and put it into this haystack page and the page reports that it would take an array of computers 5.17 billion trillion trillion trillion trillion trillion centuries to guess that password.
So a generated password will probably keep you safe. You can attempt to crack the password with the following code. The code assumes you used an eight character password and should take thousands of years before it finishes. You can interrupt it with CNTRL+C.
from steembase.account import PrivateKey
from steembase.account import PasswordKey
alphabet = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789"
real_public_owner_key = "STX5kJnwhzphuAdpQLLSgcu5rvA6smznNmQEydSTSTURvHfXhVnbo"
def password_gen(length):
assert(length > 0)
if length == 1:
for x in alphabet:
yield x
else:
for beg in password_gen(length-1):
for x in alphabet:
yield beg + x
counter = 0
try:
for guess in password_gen(8):
private_key_obj_guess = PasswordKey('elf', guess, role='owner')
public_key_obj_guess = private_key_obj_guess.get_public()
# STX because it's a testnet key
public_key_string_guess = format(public_key_obj_guess, 'STM')
counter += 1
if public_key_string_guess == real_public_owner_key:
print("Your password has been guessed!")
break
except KeyboardInterrupt:
pass
print("%d guesses made" % (counter,))
That's it, there is almost nothing to it. A real hacking program would try the shorter passwords between 0-7 as well and would probably actually printout or save the private key if it matches, of course! There are other things like using dictionaries to try all of the dictionary words. A faster program could be written in C++ or Assembly. You need to have passwords that are not dictionary words and you shouldn't share passwords between different sites as some sites might actually store your password as is.
Removing the burden of copy and paste
There is a concept of a password manager with most computers. This means you do not need to copy-and paste from a passwords.txt file to the web-browser. The web-browser can store it. Well any software should be able to. I tried a keyring module.
First, I installed keyring
pip3 install keyring
Secondly, I added this kind of code.
import keyring
keyring.set_password("system", "elf", 'secretpassword')
password = keyring.get_password("system", "elf")
# password is 'secretpassword'.
Thirdly, errors, errors, errors.
It's great when libraries just work. This is what users expect from the software we write but when they don't either it's time you learned to avoid a package rather than thinking of it as wasted time. If you have got this module to work, please comment below. If not, I would stay away from it.
 March 9th
March 9th March 8th
March 8th

