The Hacker's Language in Action: #1 First Contact
It is discreet, powerful, simple, extensible, portable. Widely used in areas such embedded systems, mobile devices, The Internet of Things, games and more. Its name, Lua, born in 1993 and its father is Roberto Ierusalimschy. But hackers worldwide found its beauty.
Why do Hackers like it?
Information on Russian hackers and malware can be found on this steemit post with other information sources.
Get Lua
The official web site is lua.org and the binaries for windows on Lua Builds. For Linux or Mac OS installation is easier on Lua Downloads.
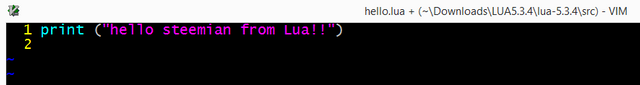
First program on file "hello.lua"
- Put:
- Execute
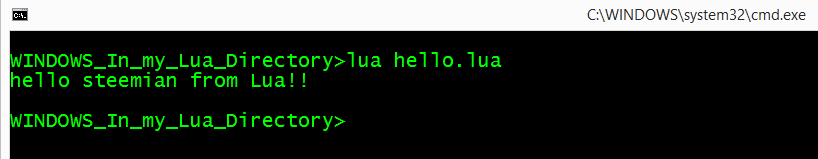
Chunks: Each piece of code that Lua executes (a file or single line in interactive mode).
- Other hello:
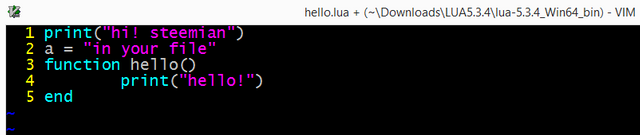

Others: with
dofile("myfile.lua")in interactive mode we are using your owner functions and variables. Orlua -i myfile.luato execute your file and then stay in interactive mode orlua -l myfile.luafor load file only. - Comments:
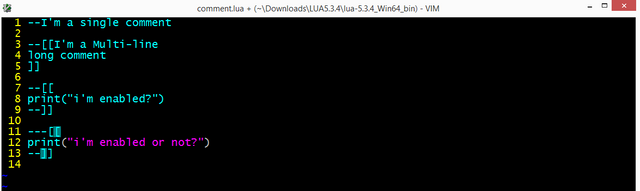
Line 11 is a common trick
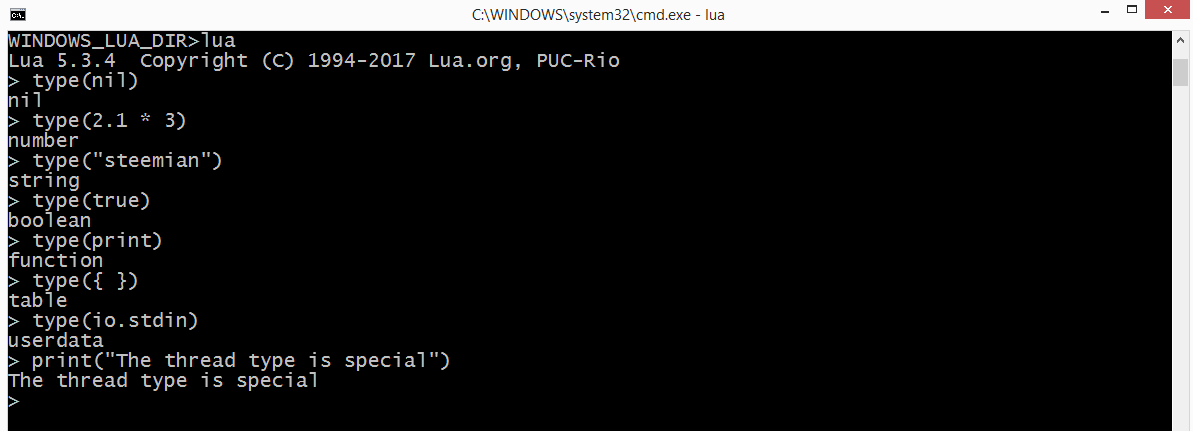
Eight basic Types
nil: A type with a single value, nil, and whose main property is to be different from any other value.
Booleans
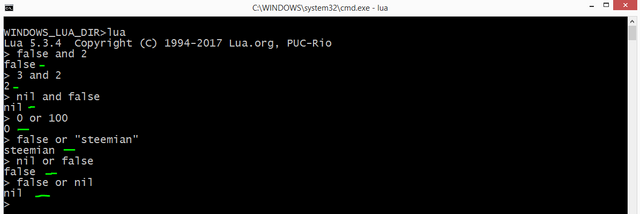
Lua supports conventionals set of logicals operators: and, or, not.
A GOLDEN RULE: The result of the and operator is its first operand if that operand is false; otherwise the result is its second operand. The result of the or operator is its first operand if that operand is not false; otherwise the result is its second operand.
To be continued...
References:
- Roberto Ierusalimschy, Programming in Lua, Fourth Edition.
- lua.org