Tracking pixels, the tiny invisible spies of the internet
Preface
In this post i would like to talk about tracking pixels and how they can be used as discrete read receipts in emails and more generally on how they can be used to derive the IP addresses of targets.
Whats a tracking pixel?
A tracking pixel is actually an image file, generally they are called tracking pixels because they track the IP address that accesses this file and the image has a height and width of 1 pixel. hence tracking pixel.
What can you use them for?
One use of Tracking pixels is within emails to function as a sort of silent read receipt or means of deriving an IP address of a targeted individual.
if the email client renders the tracking pixel the access is logged by the server hosting the tracking pixel and made available to the person paying for the service.
The other common use of tracker pixels is to provide analytics on websites regarding unique visitors and the locations from which these visitors originate from.
What do they look like?
See the lines above?, between those line could be a tracking pixel... there is actually a picture embed between the lines but it is not a tracking pixel. lucky for you!. You can see by the source of the file that it is just a normal picture hosted at tinyimg.io; it is actually a 1x1 pixel png file with a white background. it exhibits all the characteristics of a tracking pixel with out the nasty tracking.
Looks harmless, how does it track me?
With a traditional tracking pixel, it will be hosted on a web server which is monitoring it's HTTP logs and watching for anyone accessing that picture (these are uniquely generated for each email). generally this tracking pixel and associated logs/data will be accessible to the person paying for the service and presented in nice dash board for their viewing pleasure.
The log's generally contain information such as:
- access time
- amount of times accessed
- ip address of user
- user agent of browser/email client.
Tracking via email has a lot more appeal as you can derive the IP address of a targeted individual simply by sending them an email; with a browser based tracker pixel you are more likely to collect a lot of peoples details and not know which one was your actual target; one method to get around this is have an obscure page and use social engineering to get your target to browse to that page.
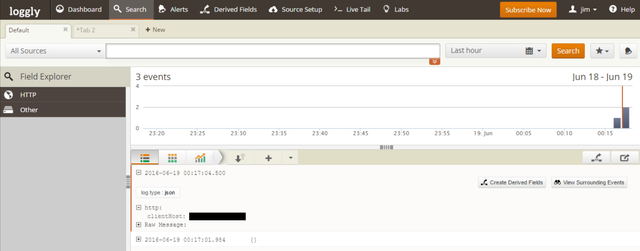
Tracking webpage views with rich data and nice dashboard
https://loggly.com provides a platform that allows you to track your page views with custom tracker pixels and provides a lot of in-depth data and a nice dashboard with charting to provide information relating the views over time. Loggly offers a paid service but also offer a trial sign up to allow you to experience the power of the platform at no cost.
Prevention
Most email clients these days do not download images within emails automatically; this helps considerably and should be enabled if it is an option on your client!.
This would mean that you would need to request your client to download the images before any chance of one of these little guys tracking your details.
On the other hand Internet browsers download images automatically and are much more vulnerable to being tracked with this technique.
Use a VPN or proxy server to protect against browser based tracking.
Some of Web security suites or components of AV/Firewall can assist in the detection and blocking of images with the dimensions 1x1 pixels. But this is not the only way to skin the cat any normal image file or element could be used to track this information and by blocking all these element's your webpages would look pretty boring.
Everywhere you go on the internet you leave a digital fingerprint, if you want to leave someone else's fingerprints, use a proxy server or VPN provider for your general browsing.

Steemit will soon be implementing measures to prevent tracking pixels in posts.
Really great to hear :)
Q. Will this be done by hosting all images within a post on IPFS or some host and not the original image host linked in the post? or maybe an in built image hosting service within the system, blocking other providers... ?
Combination of the two things you suggest.
There was a canvas fingerprint vulnerability and this reminds me of that. Is it related? Canvas fingerprinting allows for tracking of the computer by the unique hardware configuration which acts as a unique fingerprint for a computer.
Maybe I should start posting on these topics as well because it seems there is demand for this knowledge.
Please do, i would love to read your posts on this subject :)
great
I love your posts, but they really make me paranoid :-D
Cheers Cryptogee, sometimes being a bit paranoid is a good approach; don't get to worried, just be aware.
it's an interesting field of study; the more you know the more concerned you are and the more that you realise the mistakes you have made in the past, but live and learn :)
But you're not paranoid if they really are out to get you! :O