Ransomware - Forcing Bitcoin Adoption via File Encryption - Since 2013

Ransomware - What is it?
If you have never heard of ransomware of been forced to deal with the affects of being hit by such an attack consider yourself lucky. Ransomeware; traditionally attacking corporations seeking to encrypt data and holds the decryption keys for ransom; generally requesting payment in varying amounts of bitcoin for decryption keys that can be used to unlock your files and return them to their normal un-encrypted state.
Ransomware is a rapidly expanding industry and for good reason; the advent of bitcoin and the ability to be paid by the 'customer' (aka victim) without disclosing personally identifiable information has created a playing field that is easy to enter and has a very lucrative business model!. The Ransomware industry is set to break the 1 billion USD mark this year putting it with the likes of Amazon.com and FedEx in terms of profits. These venture are so successful that larger ransomware distributors are employing customer service teams to assist their 'customers' with either obtaining bitcoin, paying bitcoin or unlocking files after payment is received.
The first majorly successful ransomware was know by the name "CryptoLocker' which netted almost 3 million dollars from victims globally.
The name it self has almost become a brand as such and newer variant will actually brand themselves as CryptoLocker to leverage the brand awareness. The Original CryptoLocker was shutdown in late May 2014 with the discovery and destruction of the Gameover ZeuS botnet; during the shutdown operation a database of private keys were also discovered and made available through an online tool that allowed victims to unlock their files without paying the ransom.
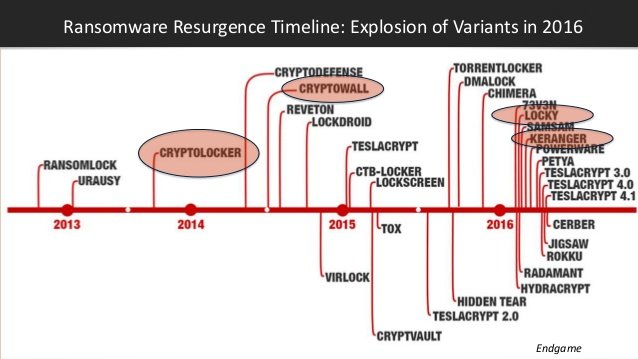
Since Cryptolocker there have been a number of variants charging different amounts and deploying different strategies and fear campaigns.
See the image below reporting the most successful variants released since 2013
Ransomware dramatic video from AV vendor Trend Micro (5min)
How does infection occur?
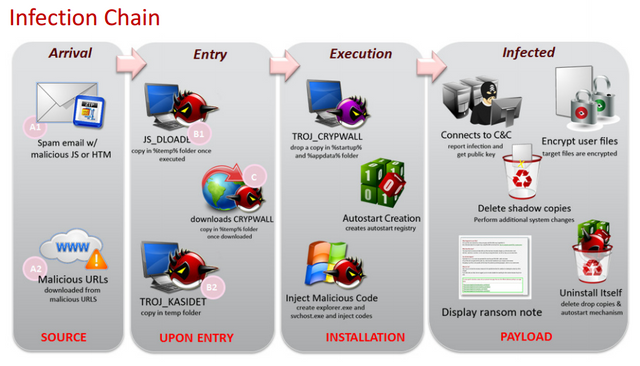
Infection normally occur's from targeted email with attachments, malicious web advertisement or links (delivered via social media or email).
Browser based attacks will attempt to use JavaScript exploits or just trick the user into downloading an executable application often containing harmless extensions in the name of the file such are invoice.doc.exe this file is generally a 'dropper' and once executed it will download the actual ransomware from an internet source.
Attachment based ransomware often come in the form of office documents with embedded macros which will look to infect the machine with ransomware; these attachments similar to the files mentioned above portray to be legitimate files and often come from freshly crafted domain name that look very similar to the official brand or company they are pretending to be.
Once the ransomware is downloaded it will make changes to the system to ensure it survival potentially disabling the anti virus, creating auto start entries, eliminating backup files, populating itself to other locations and injecting itself into memory.
It may attempt to elevate it privileges to a system or administrative user to get further penetration into the machine and other machines on the connected network.
It will then go to work enumerating the data that is has access to either on the local infected computer or analysing potential targets on the local network; once a list of important data is complied it will connect to a C&C server and request a public key for use with the encryption operation and then set to work at encrypting the data and destroying any accessible method of recovery.
Once completed the ransomware will use some method of informing the user of the infection and presenting a ransom amount and means of payment; generally at this stage the ransomware software will self destruct to prevent post analysis of itself and protecting its methods for use on future attacks
Few intresting varients
Most ransomware are variants of cryptolocker and use a search and encrypt style operations although some have stepped outside the box and for that reason i would like to mention a few
Chimera
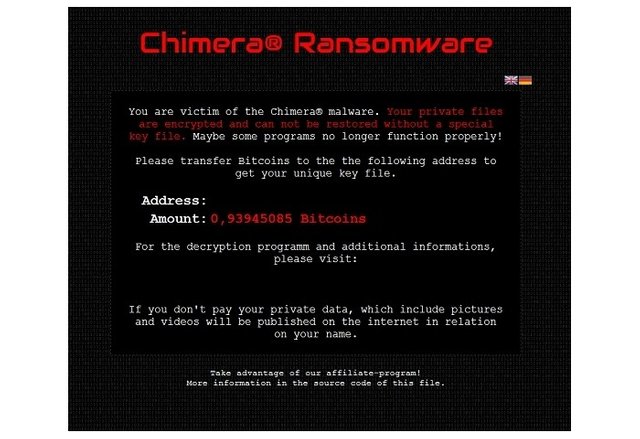
Ex-filtrates and encrypts your data and if the ransom is not paid by the deadline uploads your private information to the internet and associated the data with your real world identity.
Jigsaw - play on Saw the movie
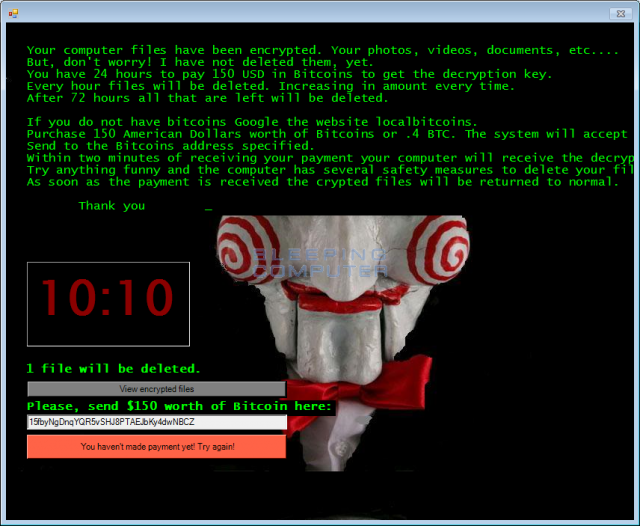
Jigsaw encrypts and starts deleting your files at an exponentially increasing rate; deletion rounds happen ever 1 hours and amount of files deleted will depending on the time elapsed.
Cerber
Cerber morphs server side every 15 seconds to evade detection of signature based detection methods; it also provides audio instructions in 12 languages to explain what happened and how the customer can recover.
Petya

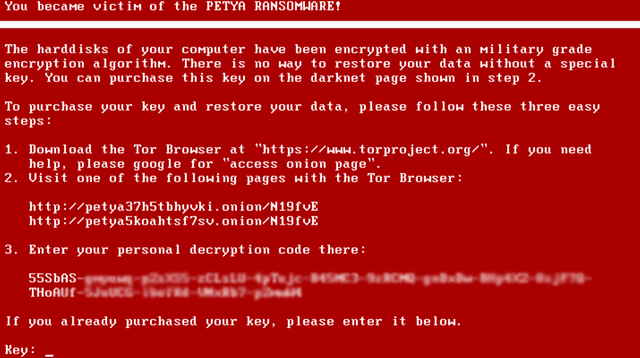
Petya could have an article by itself but the crux of it is that Petya will overwrite the Master Boot Record of your HDD and then crash you machine; on restart the computer will look like it is running a check disk but it is actually encrypting the contents of your HDD.
Locky

Locky is wide spread and sounds cute but it comes in the form of an office document attachment in an email pretending to be a trusted provider. The document files contains a macro that will start is malicious attack
Ransomware is expensive
Ransom amounts vary from variant to variant but generally are in the order of 0.5-1 BTC; with some notable exceptions.
- Emper Ransomeware - 13 Bitcoin
- Petya Ransomware - 1-2 Bitcoin
- Bucbui Ransomware - 5 Bitcoin
- Crypshed Ransomware - $30 USD
There has also been cases where custom ransoms have been demanded such as hospital that had all it patient records encrypted which was requesting $17,000 USD payment for decryption details HERE and a few other cases such as a police station and government facilities.
Clearly if you are going to get hit with Ransomware you are much better off with Crypshed for the bargain basement price of $30 USD!!
Protection is difficult - Ransomware is sneaky!
Given the scale and profitability of ransomware vendors they are constantly adapting their method of attack and evasion of gateway and endpoint protection.
One variant of ransomware name 'Cerber' is constantly morphing every 15 seconds to evade signature based detection. At this rate even if you have a solution which is connected to the early detection network (distributes hashes of malicious files to a network of peer once a infection is detected) it is not very effective against Cerber as the rate at which updates are discovered, broadcasted and acted upon is often not quick enough to protect against the constantly changing variant.
At this stage Antivirus vendors are starting to look a file operation and stop attacked based off triggers such as an untrusted processes updating files to frequently or looking at kernel operations.
There is no hard and fast advise that i can provide to prevent ransomware infection but a few methods that will help keep you from infection are below
- BACKUP!! frequently - check out my previous post relating to backup strategies tailored to protecting your digital currencies HERE
- Check your current antivirus has ransomware detection such as those described above
- Be vigilant and treat every email and link as suspicious.
- when you are looking to click a link hover your mouse over the link and ensure the target address is what is depicted in the link itself and that the website you are looking to visit is the official page of the purported company or just manually visit the website by typing the official URL into your web browser or using google search
- Disable hiding of know file extensions to better understand the file type you are about to run
- Ensure you keep your system updated with the latest operating system patches and 3rd party patches such as browsers, java, flash etc..
- Install script blocking extension to your browser such as SafeScript or NoScript
- use a tool such as Sandboxie to isolate/sandbox your browser from you computer
Sentinel One - Next Gen Anti Virus
There is a new company that has released products that seem to be only available to the enterprise users for the time being but they are so confident in their abilities to protect against ransomware that they back their product with a guarantee and offer compensation of $1000 per home user or $1,000,000 per enterprise if you are using there product and get hit with ransomware; their product is also rated in the 'visionary' section of the garner magic quadrant. The AV vendor is Sentinel One and their website can be found at https://sentinelone.com/.
I could not see any publicly available software or options to purchase directly but these seems like a vendor to keep an eye on!
Great post. Dont know this exist at all ;-)
Air-tight security is the utmost need of the hour. Not only in the cryptocurrency space but throughout the web. As the world advances, more of the current services will move online where these hackers lurk. So, a breakthrough innovation in security is required.
Perhaps someday quantum computing will be feasible and be able to achieve this.
yeahhh good point
When moving in the Internet never click on suspicious content. Always take care and try to use antivirus software.
You don't want your Steem and Steem Dollar in the hands of others :)
liked it
this is a superb article about security, UP!
Never open email attachments from people you don't know and from people you don't expect to receive attachments.
Basically, just don't download attachments.
Nasty things they are @steempower

Identity theft is also on the rise
What about steem dollars?
Very interesting. I hope reading that won't bring me bad luck aha