Generate Secure Random Passwords or Private Keys

Having a truly random password, is the only way to have a secure password. In cryptography this is referred to as CSRNG (Cryptographically secure random number generator), and there are many theories how to create one. Basically the output must look uniformly random, and there should be no bias on any of the values.
Now the requirement is a perfect random number generator. We know that humans are very poor at generating entropy, because all your sources are from your mind, or public life, that anyone can guess. Besides humans repeat numbers with a very big bias:
But we can't trust our PC either. It could have a weak or tampered RNG in it, or it might be a closed system, and processes could repeat, even if we gather entropy from multiple sources (mouse movement, CPU clock, heat, network traffic) it might not be a good quality randomness. So we need to combine them in a special way, and I think it needs external entropy as well. As good as a PC entropy is, I believe it needs to be mixed with external entropy in order to be truly random. So let me show you my theory.
My Methodology to create RNG
Warning this is experimental cryptography, and it might not be secure. Use it at your own risk. I will not be liable for any damages or financial losses.
My theory is to combine multiple randomness sources, with huge sizes of low quality entropy, and squeeze out a smaller key from it (256bit or 128bit) that is very high quality entropy. Sort of like how you input many tonnes of gold ore and squeeze out from it a few ounces of pure 24k gold.
We will need various sources of entropy, that we can find on the internet, they are public that is true, but we will combine it in such way that an attacker will have no way of knowing the output, even if they have the input. And you don't have to trust either of the input sources, in order to create a secure output.
Methodology
We will cryptographically combine various input sources, to create a secure output source. Some people suggested XOR-ing, but I have read that that it's not as recommended due to length extension attacks or other correlations and whatnot. So we will just encrypt the files together as our combination function. That will give us the output entropy pool, then we will just generate a salted hash from that, which will give us our password.
1) Random.org
They claim that they offer truly random entropy source from atmospheric noise. Whether that claim is true or not, it's a good input in our engine.
- I just grab 16,384 bytes from here: https://www.random.org/bytes
- That should give us 131,072 bits of entropy of who knows what quality
- Then I just download that to a file:
RandomNumbers
2) Random Photos
- I just grab 3 random photos from a search engine with the keywords: "whisky" , "brain" , "spaceship".
- Then I grab 3 other photos from a search engine with other random keywords: "gerard" , "house" , "movie".
Obviously if you do this, you should choose other keywords, because some entropy is lost by revealing the keywords.

- Now so far all 6 of these have been public information, mixed with my own random choices, now it's time to make it cryptographically random.
- First I will encrypt the second set of images with AES-256, by choosing 3 separate keys for it generated from my PC
Generate with this command on Linux:pwgen -s 100 3(I get these results, you should use others)- CjfkeB8StxXlwCpVN8r5zeKOFah7foDmTrWQm4H2x7nW8BcQXlD2opi9cUQbwtCNeSP9e7uHgUOCgTx91oyn7V6nQNXKNjH7exOF
- xdnLbsJttrUMhDRudX6SZENp1QmV50AbZRFyqrKUeok8LdpHqOvTJKd1aAEFxGWbfp7qRZsP4Qju1kZ2f30UyaelnpimJmrd4o8O
- kES6ldEugUG0HFQFSIr5AdAnNU9Up5awjLdL27rp72BaKhQH5j6SKYF80vhAFqJZudueuKDkGXKVQJpcu6iCGTzlLU8GcCtmzCcx
- So we encrypt the 2nd set of files I named PW, with these 3 keys with the following command:
openssl aes-256-cbc -in filename -out output -salt -pass pass:PASSWORD(just change the password, input and output to your own)
- First I will encrypt the second set of images with AES-256, by choosing 3 separate keys for it generated from my PC
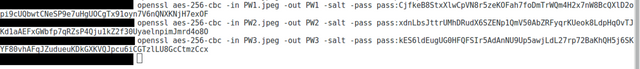
Then we have the 2nd set of files encrypted, which is used to XOR the 2nd set of files with the 3 sets of keys, as AES is largely based on the XOR function. So we have 3 somewhat good entropy sources now
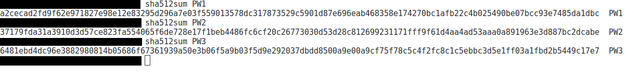
Then we take the hash of the encrypted files, and use those as the password for the encryption of the 1 set of files:

We take 512bits, with SHA512 hash function, a distilled 512 bit of entropy from our files:
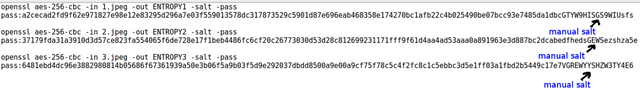
Just to make sure, I will add a little bit of salt to it at the end that I choose, to make sure it's indeed random, and encrypt the 1 set of photos with these 3 keys + their salt.
3) Putting it all together
We now have 4 sources of entropy, you can perhaps add more, like record yourself talking gibberish, and do the same thing with the sound file as we did with the random photos. Or video tape your city and use the video as an entropy source, it doesn't matter. The more the better, but just for this illustration, we are good with 4.
Now what we do now is just simply package it in a .tar file, because a .tar file doesn't compress it, it just creates a single archive out of many files.
- Our files are by order 7+15.6+8.7+16.4=47.7 kilobytes so our combined
.tarfile is 51.2kb , although most of that extra space is just encoding junk and headers. - So we have a source of 51.2kb of low but unique entropy pool, as the file itself.
- That is 51,200 bytes or 409,600 bits of entropy, and we will only need 128 bits or 256 bits in order to create a password. Needless to say that this file should stay secret, and it should not be shared, furthermore all other files used in the creation should be securely erased:
4) Generating a password or a Key
Now if we want to generate a password or a key, we just take the SHA128, SHA256 or SHA512 bit hash of the MAINENTROPY.tar file, and that will be the password. And after use, we should add a new random file with some random text in it like asfdksnkthwqi3rwui inside the archive, to act as a salt.
So if I'd wanted a BTC 256-bit Private Key now I'd just take the SHA256 of the entropy source:
89b7c6e7e2b8cfb7cce281d77320ba55892428d8de0a767317afa0e4664526eb
Which can be converted to WIF using a Bitcoin library, and it can already be used as a private key. (Of course you would need to use your own and keep it private)
And then create a random file filled with gibberish like this asfbhy9fdgdhy3wshfhufsudyiufsy9 and add it to the archive, so that it adds some bits, and acts as a cryptographic salt. Then when I want to generate another 256 bit key, I take a SHA256, and I get:
63bd905601be30e33a5e63926c66512406760e97cd86118efd0e7483b366163c
A totally different hash, that can be another 256 bit key. And so on. After every use, we add a salt to it....
That's it, that would be my experimental way of creating entropy from multiple sources. I await your comment or criticism, especially if you are a cryptographer or information security expert.
Disclaimer: The information provided on this page might be incorrect. I am not responsible if you lose money using the information on this page! This is not an investment advice, just my opinion and analysis for educational or entertainment purposes.
Sources:
https://pixabay.com
