Offensive Cybersecurity is Changing the Industry
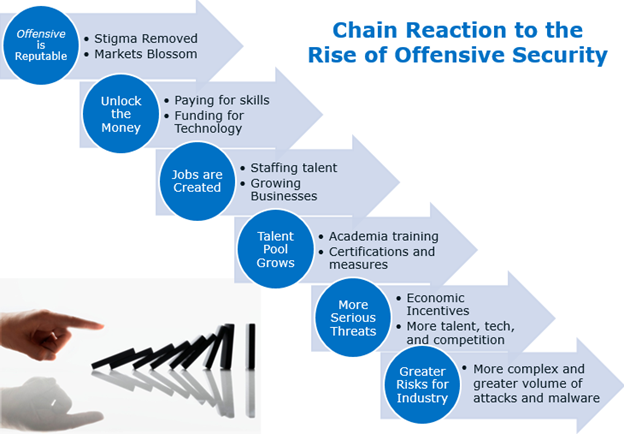
The rise in offensive cybersecurity, primarily fueled by nation state and cybercriminal investments, has had a domino effect on the security industry. The course of events unfolding of the past few years, are faithfully following a path I charted out some time ago (circa 2012) and the consequences will result in more serious cyber risks for everyone.
The original predictions can be found here: https://www.linkedin.com/pulse/how-offensive-cyber-security-changing-industry-matthew-rosenquist I was recently asked to revisit my forecast and see if activities over the past year have supported the predictions.
So let us take a look at the 6 cascading steps which I originally outlined and see if events in the world today reflect these predictions.
The Domino Effect
1. Offensive is Reputable – Over the past few years, we are witnessing many nation states spending huge sums to build up a cyber offensive capability. At last count, 29 countries have formal cyber warfare units and 63 countries use cyber tools for surveillance.
2. Unlocking the Money – Vast sums of money are now in play. Bug bounties, rewards for vulnerability researchers, have reached a million dollars or more. Companies are setting up their own public reward systems. The U.S. government alone, submitted a budget of $19 billion for 2017 cybersecurity. Cyber criminals are also raking in the money, some estimates reach upwards of $1 trillion.
3. Jobs are Created – There is a tremendous shortage of cyber security and offensive warfare talent. Estimates range from 1 to 2 million available openings as cyber roles have 12 times the growth of the overall job market. The U.S. government agencies are creating hiring allowances to try and lure more candidates in. The private sector is in no better shape, with 70% of organizations stating they are understaffed for defense. The shortage of qualified personnel is a persistent problem which is driving up salaries and fueling headhunting to a new level.
4. Talent Pool Grows – In response to the shortage of trained workers, the education system has pushed forward with aggressive programs at high school, junior college, and major universities across the globe. Certification programs are also in high demand. Although diversity remains an issue, with a lack of women and underrepresented minorities, the future is bright for the many students in the academic pipeline.
Where are we today?
Chronologically, we are in the 4th phase and edging into the 5th of the predicted chain. A talent pool is growing and the industry is entering a phase where more serious threats emerge, which is the 5th prediction followed by the 6th and final prediction of greater overall risks for the industry.
If you are interested in the details of those predictions, I urge you to read my full post, which can be found on LindkedIn: https://www.linkedin.com/pulse/how-offensive-cyber-security-changing-industry-matthew-rosenquist and the original post (2013) on the Intel IT Peer Network: https://itpeernetwork.intel.com/how-offensive-cyber-security-is-changing-the-industry/
…I would post the full How Offensive Cyber Security is Changing the Industry blog on Steemit, but I think @cheetah would not like that. A note to @cheetah, the image in this post is mine, I created it, but can be found in many places on the Internet including the links I provided. So expect to find it.
Great read! It seems cybersecurity is a fantastic industry to be working in at the moment. Can you recommend any online cybersecurity resources/courses to help bolster one's credentials?
Very good question. I was thinking the same thing. Especially, as is pointed out in the article, jobs growth is an expected outcome of these developments.
There are a growing list of materials, schools, and programs. Look at certification programs (ex. SANS), local community colleges, tech schools, and universities. There are massive amounts of online material and even free cyber-ranges to test and grow your skills. It really depends on the type of credentials you are looking to obtain. Lastly, and this is important, get practical and realistic experience to fuel your knowledge and comfort in dealing with these problems. Experience is one of the most important factors hiring organizations are looking for.
So your basic contention is that since countries and businesses are investing in offensive cybersecurity, that a much larger amount of money is being poured into the hacking industry than when hackers were forced to work underground, which will lead to greater threats coming? Defensive measures aren't incrementally and diametrically being worked on to continue staying a step ahead of the offensive measures?
First, let me refer you to my original predictions which discusses the relationship https://www.linkedin.com/pulse/how-offensive-cyber-security-changing-industry-matthew-rosenquist
In a nutshell, the vast investment in offensive technologies, people and skills have had an unintentional consequences, making the overall threat landscape more dangerous. With higher risks, more security is needed. This creates a tectonic shift where spending for security must also increase, causing ever more investment.
Look at it this way: if hacking tools and skills did not get a huge financial boost and remained relatively stagnant over the past 5 years, we would not have as serious of a problem as we have today.
I'm not convinced it's due to funding or anything. I think it's actually due to the popularity of imperative programming languages and the fact that a lot of very common problems are a result of mistakes by the programmers, which are a result of over reliance on and trust in too many programmers, which in itself is a result of favoring programming languages which are notoriously difficult to write secure software in.
Fully functional programming languages, correct by construction, formal correctness, this is one approach to bug free software. Another approach is isolation of processes, virtualization, separation, and quick recovery. As far as I know, there isn't a lot of money going into improving the programming languages or just teaching the correct by construction approach, and it's notoriously difficult to write software in that approach because there hasn't been enough effort to make formal verification easy.
As with everything else, it's also statistics and surprise. The risk stats seem to favor the attacker who just has to get lucky and find some zero day or take advantage of some little known exploit. The defense side has to somehow know every exploit, every zero day, and patch it up before someone somewhere takes advantage? It in my opinion is a losing battle which is why I looked into correct by construction, formal verification, attack tolerant information systems, and artificial immune systems, with the idea that you can improve security by reducing the attack surface through limiting unexpected behavior in the software, and making it so recovery ability is self improving.
You bring an interesting perspective to the discussion! But consider this, many of the 'bugs' you hear about were actually part of the design. In many cases 'features' are being misused or used in way not intended.
Companies like Microsoft, Google, Apple, Oracle, and other spend billions of dollars trying to make their software 'bug-free' and without vulnerabilities. They do a great job, but with increasing complexity it becomes exponentially more difficult over time as systems are connecting more users, devices, for different usages, and creating much more data.
The other aspect I would have you consider is that technology is just a tool. In many cases it is how you use it which defines if it is good or bad. Some examples: are vulnerability scanners good? Network sniffers? Keystroke loggers? The reality is they are both good AND bad, depending on what someone is using them for. In fact some were created by hackers but are now used by security and vice versa. In the end, it is not easy to find a single source of insecurity, just as it equally difficult to identify a single fix.
You highlight a valuable point here:
Managing complexity is one of the biggest issues in software development. There are ways to do this that I've looked into involving composability but this is all new and not yet a best practice. I think if complexity can be managed, then if you can understand the behavior of your software you can at least know what can't happen.
Of course you are right that no one knows how software will be used and people could use even bug free software in unexpected ways, but when it's bug free at least you know what the software can't do. There are no single fixes but my intention was to question why there isn't more funding going into secure software development and why are developers continuously making the same human errors which get exploited over and over? I'm talking about examples like cars being hacked, or electronic hearts, the sort of devices which require software to be correct by construction and to have predefined parameters or hard constraints.
There is an interesting video on the topic of LangSec which you may already have seen:
Reference: https://blog.hackster.io/def-con-24-car-talk-1f1b9def8fb
I wasn't disagreeing with your assertion, it makes perfect sense, I was more questioning how can this be happening? That offensive cybersecurity is being built up, the technical advances are readily available to businesses, governments, and hackers alike, and that defensive measures are not being funded at an even faster rate.
The amount of Offensive R&D far exceeds the Defensive R&D is one reason. Another is the rise in offensive skills and tools makes them more efficient at causing impacts.
Defensive is almost futile because offensive capabilities far outpace defensive. But there are some promising ideas. Have you heard of attack tolerant information systems and the CRASH Program? A lot of the insecurity comes from a flawed approach to software development which in a way leaves the back door open.
References
http://www.darpa.mil/program/clean-slate-design-of-resilient-adaptive-secure-hosts
Nice article man @mrosenquist
Thanks much @funnyman!