Newest PowerPoint Exploit Just Takes a Mouse-Over of Text
Malware distributors are a creative bunch who like to use Microsoft Office files to hide their code and stealthily infect unsuspecting victims. In the past, we have seen macros, Visual Basic for Applications, and Javascript employed, but security tools have reached parity and now easily track such tricks. So, it is time for something new. The latest is using PowerShell code in Microsoft PowerPoint presentation files, and only requires the intended victim to mouse-over seemingly innocuous text.
Undermining Trust
Microsoft Office products, such as Word, Excel, and PowerPoint are popular vehicles for attackers as they are familiar and trusted by office personnel. Workers in banks and other places of professional business use these products and feel safe. This is the very weakness that such malware looks to exploit. By getting a lazy or over-trusting person to click ‘Enable’, success is within reach of the criminal.
No Click Needed
Just by hovering the mouse over the link, it calls the necessary code and a malicious infection begins to take shape. In most cases, due to default security settings, users will see a Security Notice pop-up, warning them of potential danger. If the user selects Enable All or Enable (the correct choice is Disable) then the system will attempt to connect with an external site for the malware downloader and the process moves quickly forward. The system can be compromised without any further interaction by the victim.
A number of banking Trojans are now picking up on this trick, including Zusy, Tinba, and Tiny Banker. Expect the popularity to increase with the success rate.
The security researcher at Dodge This Security posted a great write-up New PowerPoint Mouseover Based Downloader – Analysis Results on his blog. The tech savvy can check it out for all the juicy details, including screenshots and Sysmon logs from his analysis. As a bonus, he includes the Indicators of Compromise (IoC’s) for internal security teams to update their sensors and alert traps.
How to Avoid
The key is trust. The same level of diligence we must maintain for downloading executables from untrusted parties must apply to all types of files, included those from familiar office applications. First and foremost, end-users must be savvier about the risks. Don’t open file attachments in email from an untrusted sender. Never make that mistake.
Secondly, software companies serious about security, such as Microsoft, have put controls in place to alert users of many dangers and turned these setting on by default. Don’t disable these. They are an important layer of protection. Additionally, don’t ignore them. If you see a security pop-up from your trusted application (not some web page however) take a moment to consider the pain you may be inflicting upon yourself. They are trying to help you remain malware free, so choose wisely.
Professional security software products will also begin their response-evolution to monitor for such harmful mouse-over code, network calls to unsavory sites, and launching of undesired installer packages. They can isolate or block such actions and many can take extra precautions when an office application attempts to run external code. A number of security tools, such as filters, sandboxes, and even artificial intelligence sensors may work nicely to block this threat. But that is temporary, as the cycle will repeat and those same creative malware distributors will again find another path to achieve their objectives. The game does not end that easily.
Interested in more? Follow me on LinkedIn, Twitter (@Matt_Rosenquist), Information Security Strategy, and Steemit to hear insights and what is going on in cybersecurity.
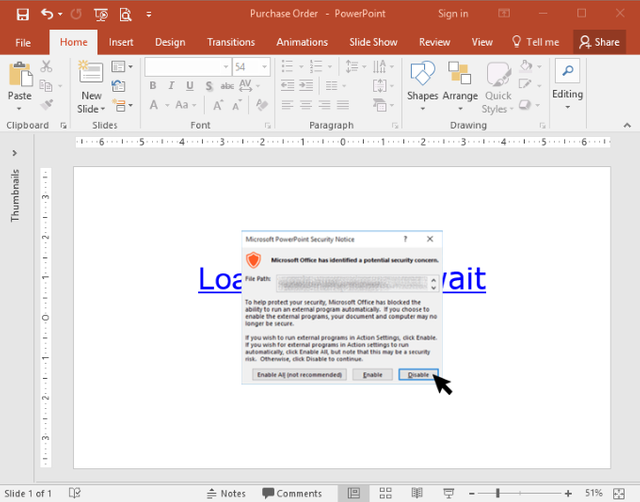
"Click with caution. You are about to surrender all control to an untrusted file" That should be the warning.
How do we know who to trust? I often just ignore the pop ups.
I have learned the hard way not to open file attachments on my mailbox! Thanks for the info!
very good friend excellent post @mrosenquist
excellent post!!
Very good post. Now following you!