How Good is Your Data Breach Response?
Data breaches are commonplace and every organization who handles sensitive or private data should have a proper capability to respond to an incident. Many companies have a basis set of procedures, while others maintain a mature set of people and processes. There are a small percentage of organizations, who over the years, have refined their capabilities to a professional level. Knowing where you stand and how you can improve is key to finding the right level of information security preparedness.
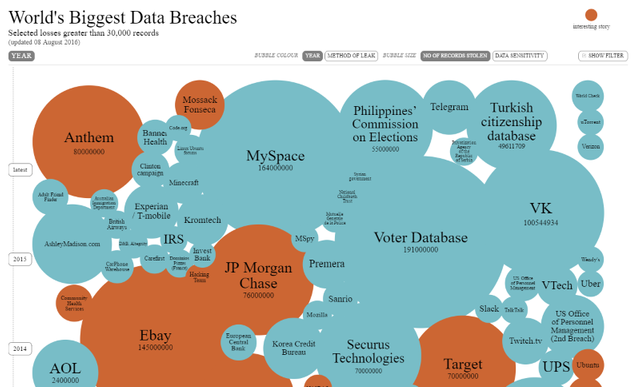
Data breaches are an epidemic.
The Health industry took a beating in 2015. Record amount of sensitive healthcare files were taken or went missing. According to the U.S. Department of Health and Human Services Office of Civil Rights, about 35% of the U.S. population had their health records exposed in 2015.
Government, financial, and technology based organizations were also targeted. In total, over 707 million records were lost or stolen in 2015, according to Gemalto’s Breach Level Index. In reality, no company is safe.
This is why it is important to not only have strong preventative controls, but a good set of processes and resources to respond to an incident. Proper crisis response can limit the damage and prevent reoccurrences.
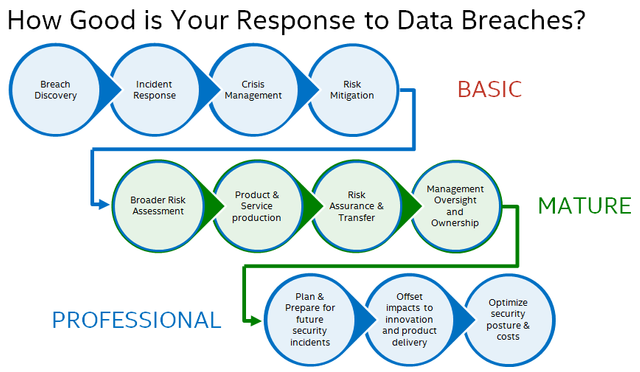
Data Breach Response
Basic controls are employed to handle the crisis and close the vulnerability of the leak. This is the very minimum. Many companies who lack the forethought, assemble this team after the first major data breach is detected. It is chaos. Trying to deal with an unfamiliar situation while under the scrutiny of customers, regulators, and executives can be a nightmare. This level of capabilities is typically slow and focuses exclusively on the single breach aspects.
Management are usually disillusioned in thinking this was a one-time event and will never happen again. The marching orders are to find this problem, resolve the issue, and return to business as normal. The weakness is not understanding the vulnerability is likely systemic. Plugging one hole in the dam with a finger does nothing if you ignore all the other cracks.
Mature capabilities are usually a sign of experience. They have had a data breach before and realized they need to look for other weaknesses and to be prepared for the next one. It is a realistic way of thinking, although not popular with executives. They would rather not have any such incidents, but then realize the cost for such controls would be obscenely expensive. So a balance is struck. These organizations conduct risk assessments to find vulnerabilities in their data handling, may choose to pay for breach insurance, and will have internal accountability clearly established.
Professional level data breach capabilities are found in organizations who understand the value of their data, regulatory compliance, and the trust of their customers and partners. The best external consultant teams also possess these skills. They are willing to swoop in and address all aspects, but for a price. Professional class organizations carefully protect the information under their control but also put serious measures to detect breaches and respond very quickly. They plan and regularly test their response capabilities, working to keep them current with business and infrastructure changes. Experts work with production teams to help establish compensating controls, so the business can continue to operate, even during an incident. Lastly, they work to keep costs down and fine tune the capabilities to maintain the optimal balance of corporate security, productivity, and costs.
What is the right level?
There is no universal right level. Every organization is different. Companies have varying risk appetites, various regulatory requirements, and oversee different types of data. In general, the more serious the consequences of a data breach, the more an organization should be looking towards mature or professional levels.
Data is valuable and breaches will continue to occur. No organization or agency is immune. When preventative controls fail, rapid detection and competent response is required to minimize the immediate and long term losses.
Interested in more? Follow me on Twitter (@Matt_Rosenquist) and LinkedIn to hear insights and what is going on in cybersecurity.
At my job (network engineer) we see probes of networks almost continuously. I can put a new edge device connected to a brand new internet circuit and often see a probe hitting it with an hour of being deployed.
It is indeed a challenge, and likely will continue to be a GROWING challenge.
Agreed. As data becomes more valuable, threats will work harder to steal, copy, or hold it hostage. Although a strong preventative defensive structure should be implemented, it is unreasonable to expect all attacks will be prevented. That is the moment when a good data breach response process becomes hugely valuable.
Yes, it is when you EVER consider yourself unhackable that you truly let your defenses down. You and I know there is no such thing. And if you ever say you are unhackable in public... oh you fool... like honey to the flies.
So true! More like flies to bullsh**