Cyber Risks Compound with Technology Adoption

Just how reliant are we on computing infrastructure? Sometimes it takes just a little outage to get a taste of the interwoven dependency we don’t readily see.
Lines of Travelers
Source: pic.twitter.com/VGLUOUiaoP
It can be small. The international travelers landing in U.S. airports on January 3rd, one of the busiest travel days of the year, found themselves stuck in long lines due to a temporary outage with the customs processing system. Mobs of disgruntled holiday travelers waited for the issue to clear up. Airports across the country reported delays from half an hour to over two hours. The technical issue, not attributed to a cyber attack, impacted the travel of over 30 flights into Miami International. In Atlanta, at the biggest airport in the world, Hartsfield-Jackson was impacted for 90 minutes.
Even the most mundane things, like crossing a border, can be impacted when technology goes awry. Modern day systems are built for efficiency therefore have deeper dependencies on upstream components. Like dominoes, when one thing breaks, the ecosystem is not built to absorb the loss and instead comes to a grinding halt. This creates a backup and like ripples in a pond have far reaching consequences.
Social without Internet
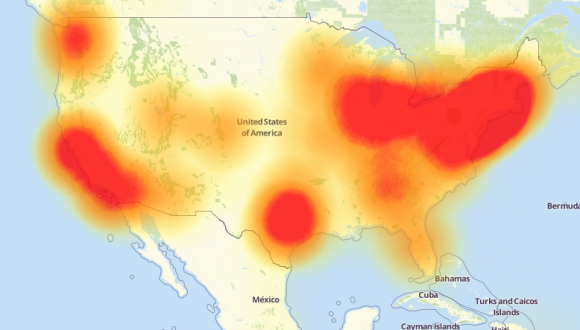
In October 2016, simple devices connected to the Internet were recruited by attackers to form a botnet and collectively sent network traffic to Dyn, a Domain Name System (DNS), internet service company, which resulted in significant blackouts and slowness to major Internet sites like Twitter, Spotify, Reddit, the New York Times, Wired, Github, Etsy, and many others. It became a stinging Distributed Denial of Service (DDoS) attack the likes we have not seen in years.
Source: Downdetector.com
DDoS attacks are not new. They have been around for many years. Technology infrastructure and security services have evolved to protect against such attacks, making them largely ineffective. Until recently that is. When instead of big powerful systems trying to cause damage, attackers shifted tactics and approached it like a colony of ants. Home routers, DVD players, consumer internet cameras, and a host of other small IoT devices were harvested like crops and their collective power was pointed at targets. The impact was unprecedented. A number of such attacks, starting in the back half of 2016, continue to pose a risk to online properties. Dyn was just one simple target. What happens if such attacks are made against critical systems?
Dominion Over Electricity
Ukraine has already suffered two separate power outages attributed to hackers, the latest in mid December, which affected regions around its capital. Customers were without power for over an hour, as personnel had to manually switch equipment to restore electricity. The attack was largely seen as sending a message, rather than trying to cripple a nation.
President Obama, in his final press conference of 2016, stated the U.S. is more vulnerable than other potential adversaries
"Our economy is more digitized, it's more vulnerable, partly because we're a wealthier nation, and we're more wired than other nations" – Obama 2016
Former FBI agent Austin Berglas stated:
"A three-pronged attack against our power grid, transportation, and financial systems would be devastating and potentially viewed as a terrorist attack against the United States".
Aggregate at Risk
The United States operates at an extremely high pace with huge efficiencies. We are a modern nation and have crafted our world to move at a dizzying pace where unimaginable systems work together like cogs to turn the engine of our everyday lives. The very foundations of which are now becoming more dependent on computers, data, and the Internet. Our transportation, power, financial systems, healthcare, emergency services, fuel infrastructure, communication networks, food distribution networks, and government services are all reliant in some way on digital technology that can be targeted by attackers.
Much like the butterfly-effect, situations in one small system may cascade to cause catastrophic impacts elsewhere. Who could have imagined that home cameras and DVR’s left with default passwords, by apathetic consumers, would be the engine used take down huge chunks of the Internet? Yet it did. Sadly, those were not even the nation-state level threats. They were likely just curious hackers looking to experiment with what they ‘could do’. The big players have much more tools in the tool-box, which are designed for greater impact over a longer period of time.
As we go into 2017, entranced with the glistening of new technology, we must also understand there is a risk that accompanies it, which aggregates and compounds over time. Cybersecurity must play a part in every step forward we make.
Image Sources:
- pic.twitter.com/VGLUOUiaoP
- Downdetector.com
Interested in more? Follow me on Twitter (@Matt_Rosenquist), Steemit, and LinkedIn to hear insights and what is going on in cybersecurity

@mrosenquist, your post has been chosen by @STEEMNEWS.ONLINE as one of today's promoted posts for its excellent content.
As a SNO featured article, you have been awarded one TRAIL coin. Please stop by the SteemTrail Discord server to find out how to claim your TRAIL coin. You will need an Open Ledger account to do so.
STEEMNEWS.ONLINE watches the #steemnews tag most closely. Excellent news articles can be supported by making steemnews.online one of your operators on Streemian.
Thank you for your hard work and contribution of excellent content to Steemit.

Thanks for the recognition! Not sure how to claim the trailcoin. Are there instructions somewhere? I do have an Openledger account
Yes, if you follow the link to the Discord server, there are pinned instructions in the #steemtrail channel. Basically all you need to do is input your Steemit account and your OL account in the #open-ledger-account-add channel.
thanks!
This post has been ranked within the top 25 most undervalued posts in the first half of Jan 06. We estimate that this post is undervalued by $10.03 as compared to a scenario in which every voter had an equal say.
See the full rankings and details in The Daily Tribune: Jan 06 - Part I. You can also read about some of our methodology, data analysis and technical details in our initial post.
If you are the author and would prefer not to receive these comments, simply reply "Stop" to this comment.
Thanks Daily Tribune! I am honored!