A reply to @modprobe's "A brief rant on password security" - and why he is wrong.
How strong are our passwords, and what do the strongest look like?
Two months ago @modprobe wrote an article by the title, "A brief rant on password security [Edit: Not so brief after all]".
In his piece he argued that the strongest passwords were sentence ensembles made from somewhat random words.
His example being: "Young thieves are edified by discovering the locks in the iron web" which he claimed to have made by "looking at stuff scattered across [his] desk".
He argues that the point of these types of passwords, and what makes them strong, is their length and unpredictability.
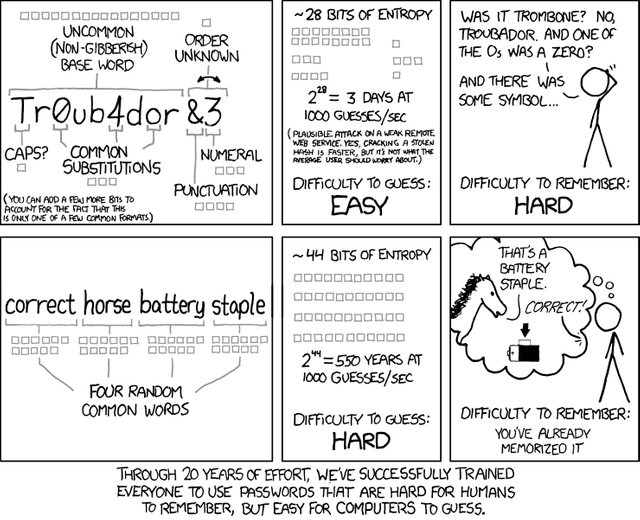
Furthermore, he linked to an XKCD comic to help substantiate his claim.
So what's wrong with this approach? After all, are long passwords not good passwords, and hard for computers to guess?
While it's not untrue that long passwords are relatively harder for computers to crack, this is a simplification.
What's really important, and XKCD touches upon this in his comic, is entropy.
Entropy is used in a lot of different sciences including information theory, and perhaps most famously thermodynamics. The formal definitions are a bit convoluted, but boils down to the following:
Entropy is basically a measure for how random, or unorderly, something is. Where a higher entropy means more randomness, so for our passwords we want a high entropy to make it hard for computers to guess.
Since language generally is quite orderly (has low entropy) a nonsense sentence of common, and even not so common, English words still has a low entropy, and is thus relatively easy for computers to guess.
Suppose then that you instead choose words like before and substitute some characters for others; not dissimilar to leet speak. The problem with this is that while it does increase entropy, the overall entropy is still quite low. Frankly, it's not that difficult for computers to predict that "e" is often subsidized with "3".
These attacks work by large dictionaries of English (doesn't need to be English but is most often) words, so instead of guessing the individual characters they guess whole words.
In the article cracking-12-character-above-passwords they found that on modest hardware using hashcat (a password cracking tool) they could crack a four word long password (sourceinterfacesgatheredartists) in just over 5 hours and 30 minutes. (although it could have taken them up to 4 days).
By enabling masks in a "hybrid attack" that aims to crack passwords where substitutions, and the appending of "randomness" are used, added about 20 minutes of entropy, so using leet speak does little to help make passwords stronger.
In fact, the very password strength tester @modprobe recommends (Passfault) ranks passwords constructed using this method as weak when a four word password: "seattlechairdavisarbol" is expected to hold up for two days against an everyday computer. - Definitely not something you want protecting important files.
How should you create passwords?
In order to decrease entropy and increase complexity the strongest passwords are long random passwords.
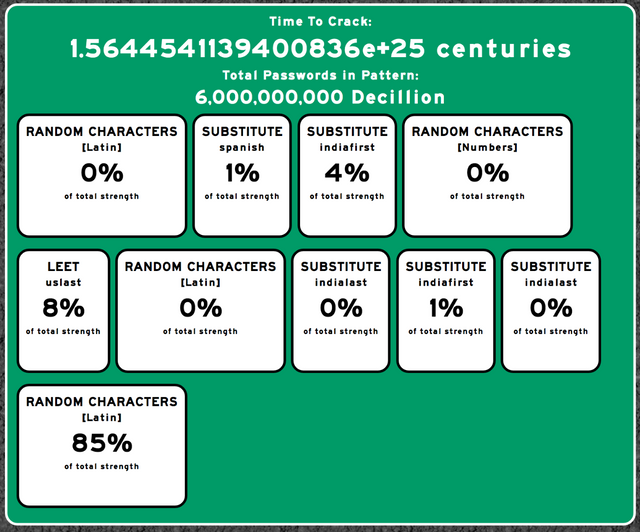
Suppose the following password: "BkQ$5[|mU6S@ezO+UAku;=%SVMpB" which I generated using Dashlane's password generator.
Using Passfault, it's estimated to take 1.5644541139400836e+25 centuries to crack, or 1.1*10^17 times to age of the universe using a regular everyday computer.
Or a mere 5.2*10^12 times the age of the universe using a "government cracker" estimated to run you $500.000.
However, the point still stands, how am I supposed to remember such long random passwords for every site I ever visit? To which the answer is: You're not.
Well, you will still have to remember one that unlocks your password manager that stores encrypted versions of likewise randomly generated passwords for every site you visit.
This way all of your passwords will take many times the age of the universe to crack using modern technology, and as it progresses, you can easily increase the length of your passwords.
That is until the quantum computers come and destroy everything. But that a topic for another time.
Note: There are a few more things wrong with sentence like passwords that I didn't touch upon, and further more wrong with XKCD's comic. For example, the way he calculates entropy, and time to crack by disregarding character space. Also, things like how the server stores your password, and if they offer two factor authentication can greatly affect how strong your password is. A sentence like password stores as a slow hash backed by two factor authentication can indeed be very secure.
Good stuff man.
"To which the answer is: You're not."
I think that's what's changed and people just haven't picked up on. 15 years ago, a knowledgeable user had 3-10 major websites, and 1-5 real life services (Cable, utilities), and maybe a few game accounts. There was one browser, and you got a new computer... never.
Worst case scenario, if something was compromised, you'd be aware, and it was isolated.
Nowadays there are so many aspects to online presence. Minumum password requirements, site ownership changes, log-ins just to log-in. Different browsers, phones authentication, apps that log you out of websites.
To have "my password" is such a crazy perception and expectation.