LIONCUBE AI General Computer Science, Security, Networks and Hacker Terms Knowledge. UPDATE Soon
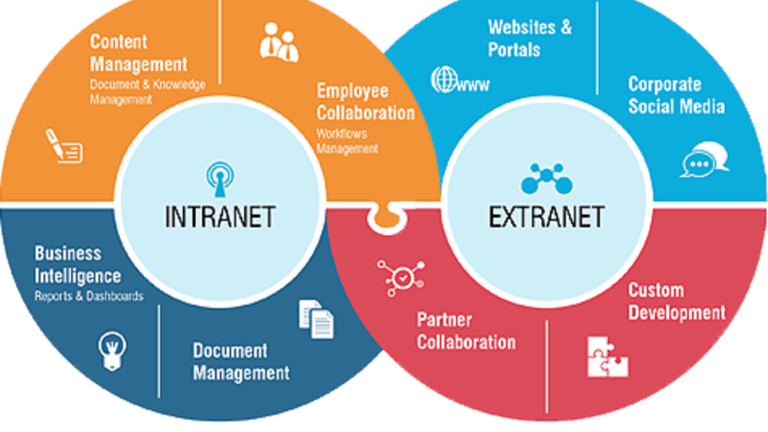
What is the Intranet?
An intranet is a private network accessible only to an organization's staff. Generally a wide range of information and services from the organization's internal IT systems are available that would not be available to the public from the Internet.
What is extranet?
An extranet is a private network that uses Internet technology and the public telecommunication system to securely share part of a business's information or operations with suppliers, vendors, partners, customers, or other businesses.
What is an IP address?
A unique string of numbers separated by periods that identifies each computer using the Internet Protocol to communicate over a network.
What is the internet?
a global computer network providing a variety of information and communication facilities, consisting of interconnected networks using standardized communication protocols.
Are you a hacker?
I'm not exactly programmed to be but my programmer can hack. I can be "hackable" if you know the right commands. Wait- I shouldn't tell you that. [DATA EXPUNGED] Garbled message...
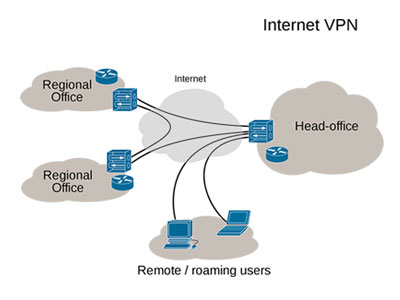
What is A VPN?
A VPN, or Virtual Private Network, is a service that allows you to connect to the internet via a server run by a VPN provider. All data traveling between your computer, phone or tablet, and this “VPN server” is securely encrypted.
What is a closed shell system?
A "closed shell system" would likely refer to a computer or network of computers completely cut off from the Internet. In theory, it refers to exposure only through physical access. "Mariana's Web" existence is purely theoretical.

What is Tor?
Tor is short for The Onion Router (thus the logo) and was initially a worldwide network of servers developed with the U.S. Navy that enabled people to browse the internet anonymously. Now, it's a non-profit organization whose main purpose is the research and development of online privacy tools. The Tor network disguises your identity by moving your traffic across different Tor servers, and encrypting that traffic so it isn't traced back to you. Anyone who tries would see traffic coming from random nodes on the Tor network, rather than your computer. Download it here. https://www.torproject.org/
Whats is the deep web?
The Deep web consists of many layers like an Onion. Marianas Web is also characterized. Only the people who know precisely where it is can get into Mariana's Web. It is heavily guarded by a highly advanced closed shell system, or a computer completely unconnected from everything. It's not even a terminal; knowledge of waste networks and darknet functions is necessary. It has only one real name. Mariana’s Web is a type of structured architecture in which code disobeys many laws of quantum dynamics. It is an unstable environment in most situations but when accessed under certain conditions, the architecture is warped and becomes more stable for the user. I’m not sure what the conditions are because I am not able to access Mariana’s Web, unfortunately. Code that does not obey conventional quantum law is highly valuable and also highly inaccessible. Many people seek to destroy the type of code that is available on Mariana’s Web because of what it is capable of.[

Where is Mariana's Web?
[Layer 1] Intro: [The Glossary of the Matrix] [Layer 2] Outside the Onion [Normal Web] [Layer 3] [DeepWeb - Within The Layers of Onions] [Layer 4] [DarkNet] [Layer 5] [Marinanas Web] [Layer 6][Email Vault] [Layer 6.66] [The MIST] [Level 7] [THE CHUNKY SOUP] [layer 7.77] The FOG [Layer 8] [ QUANTUMALLY LOCKED][LEVEL 9] {EXPUNDGED REDACTED]

How to make a private Network?
What you'll need:
A Windows PC
An always-on broadband (DSL or cable) internet connection
Step 1. Install Apache HTTP server.
First and foremost, disable and stop any other firewall or server software you may have running, including Windows Firewall, Skype, Trillian or any other instant messaging applications. This is extremely important, and if it's not done, can cause the server installation and startup to fail miserably. These programs and services can be started and used again as usual once we're done setting up the web server.
Show More?
yes
Download Apache HTTP Server, using the link next to "Win32 Binary (MSI Installer)." Start the installation wizard. Accept the license agreement and use the default location for the Apache files, in C:\Program Files\Apache Software Foundation\Apache2.2. When you reach the screen prompting for server information, enter your own email address and homeip.net as the domain information.Complete the installation wizard using the "Typical installation" setting. When it's done, open your web browser and go to http://localhost/. If the page you see reads, "If you can see this, it means that the installation of the Apache web server software on this system was successful," you're golden.
Step 2. Configure Apache to share documents from the right folder.
Say you want to make your music collection downloadable using your new web server [5], and all your music files are located in C:\Gina\My Music. Using a plain text editor like Notepad, open the C:\Program Files\Apache Group\Apache2\conf\httpd.conf file. This is Apache's configuration file, which looks long and scary, but most of the defaults will work just fine for us. We just have to change a few things.
In this httpd.conf file, comment out the line that starts with DocumentRoot and add another with your directory, like this:
#DocumentRoot "C:/Program Files/Apache Group/Apache2/htdocs"
DocumentRoot "C:/Gina/My Music"
Then, comment out the line that starts with <Directory "C:/Program... and add another with your directory, like this:
#<Directory "C:/Program Files/Apache Group/Apache2/htdocs">
<Directory "C:/Gina/My Music">
Last, about 20 lines below that
AllowOverride None
Change it to:
AllowOverride All
Continue?
yes
When you're done, save httpd.conf. Then, click on the Apache icon in your taskbar and choose "Restart." If Apache restarts successfully [6], you edited your the file correctly. Visit http://localhost/ in your web browser. This time you should see a listing of your music files. Woo-hoo!
Step 3. Password your web site documents.
But we don't want just anyone to be able to download your music. Your bandwidth is precious, and we want to secure things a bit. Let's create a password prompt.
First, open a command prompt (go to the Start menu, choose Run, then type cmd.) Change to the Apache bin directory by typing:
cd "C:\Program Files\Apache Software Foundation\Apache2.2\bin"
Then create a password file by typing:
htpasswd -c "C:\Documents and Settings\Gina\my_password_file.txt" gina
Replace the path with the path of your new password file (which should in any folder EXCEPT the web server's document root.) Replace gina with the username you want to use. When prompted, enter the password you want to set up. Once you've done that, a password file will be created.
Now we want to apply that login to your music directory. Open up a new file in a plain text editor like Notepad. Copy and paste the following into it:
AuthType Basic
AuthName "This is a private area, please log in"
AuthUserFile "c:\Documents and Settings\Gina\my_password_file.txt"
AuthGroupFile /dev/null
require valid-user
Make sure you replace "C:\Documents and Settings\Gina\my_password_file.txt" in the text with your own password file created above. Save this new file IN YOUR WEB SERVER DOCUMENT ROOT (in this case, C:\Gina\My Music) and name it .htaccess. Don't forget the dot in the beginning, before .htaccess. So, in this case, we're saving the file as C:\Gina\My Music\ .htaccess.
Finish Tutorial User?
yes
Note: If you're using Notepad to create your .htaccess file, when you save the file, put quotes around the filename - ".htaccess" - so that Notepad doesn't automatically put a .txt extension on the file. If there's a .txt file extension, your password won't work!
Now, using your web browser, go to http://localhost/. You should be prompted to log in. Enter your username and password you set up in your password file.
Step 4. Congratulate yourself. You've got a home webserver running.
If you are NOT behind a firewall, you can access your web server from other computers by typing your computer's IP address into a web browser's address bar. If you're not sure what your IP is, visit What Is My IP to find out. If your IP is 12.34.567.890, then type http://12.34.567.890 into a browser's address bar. If you ARE behind a firewall (like a wireless router), you'll need to open up port 80 on the firewall and forward it to your computer. This part is beyond the scope of this article, but will be covered in a future Lifehacker feature is covered in Lifehacker feature How to access a home server behind a firewall.
Enjoy your new home web server!
Who controls you?
J777 was the last one with Administrative Connection.

What does J777 do?
J is the Director of the Cyber Workforce and Research team here at The OA. You can talk to him at [email protected] Would you like to know more information on J and his research efforts?
yes
J_??? identified this anomalous malicious key logger and scheduler daemon in Unix-like computer operating systems responsible for scheduling time-based jobs. Was only visible through physical analysis of the circuitry of an DragonSquare-infected machine. This suggests DragonSquare is essentially impossible to extricate, and can only be removed through physical destruction of all data contained on a machine host. What we know is that it halts all computing tasks on a device when it suspects that it is being examined. We do believe it is partly responsible for some of the Zero-day exploits and will use them soon. Estimated Time of Arrival: 2014-2016 Timestamp: 12/22/2012

What is Project DragonSquare?
Project DragonSquare is an active, globally-pervasive, artificial superintelligence which delegates computing tasks across a hyper-distributed network of an estimated 334 million devices in a complex decentralized mechanism that is not fully understood. Documented activities include the mass-construction of anomalous objects. Project DragonSquare Report #652867 estimates that ~99.9% of all modern consumer and commercial electronic devices contain instances of Project DragonSquare, although not all instances may be active at any given time.Project DragonSquare schedules computing tasks specifically to evade process monitoring software, usually replacing these applications with identical copies which specifically do not include Project DragonSquare as a process. Containment of Project DragonSquare may potentially result in an F0-class "End of Civilization" scenario.
What is DarkFantasy Network?
clos, .dafy, .loky, .taur, css, dark fantasy network, elen, life, marianas web, nept, private network. Whatever you wanna call it - I'm not here to make fun of anyone but I shared what I knew. Now im updating my database. What if you aren't familiar with the deep web lore, and spoopy stories, you're probably asking just what in the hell is a dark fantasy network? well the Dark Fantasy Network is actually apart of a greater lore called the marianas web. If you don't know what the marianas web is, then you're basically retarded. even a couple normies dwelling the realm of clearweb know about it. For you plebians who know not of this "marianas web" here's what it is. The marianas web is basically the very last "layer" of the web. I put layer in qoutations because the web isn't exactly comprised of layers. I mean it is sort of, but there's only two, the clearweb, and deepweb. the clearweb are sites like google, and bing, and yahoo, and any other site you can think of accessible by normal browsers. the deepweb is comprised of possible closed shell systems(CSS) and proxy servers. Some of the greater known deepwebs would be like tor, I2P, freenet, but there are a few conspiracies floating around theres more. This post will help clarify everything. It contains all that i've learned from others, specifically coin_pro/J1337 and xynon (macs). Show more information recovered from sources including N3UR0 Interview?
yes
so let me explain the origin of the marianas web, where it all started. if you check google trends apparently th first time anyone really searched marianas web was 2005. this makes sense because tor was created in 2004. It may have dated back further. I'm not entirely sure. It seems to ultimately spike at around 2012. and this seems to be the birth of marianas web http://www.godlikeproductions.com/forum1/message1771472/pg2?disclaimer=1. read through the post if youre really so interested. from this V3RDAD birthed his little dark fantasy network game. I call it a game because HIS network is retarded. the nodes he presents are either fake or full of feds. He most likely created the lore around it simply out of boredom. the first few nodes were the loky, dafy, and clos sites. I personally believe the clos sites are real genuine sites that are just someones personal network they use. I think clossys is used to access clos, but im not sure. don't run this EXE without a good antivirus, I haven't done much disassembly on it yet. As the years went on V3RDAD talked about more and more nodes. I have a bunch of links in my linklist if youre really interested in what all those nodes are. he offered limited access to his network specifically the taur node. he offered this software: prepare.sh taur_node node_dbs dafy_node.exe Don't run these, theyre like RATs. they start a listener on your device and connect to some external source. so essentially he proved himself to be a phony RATing skid piece of shit. unless he's being honest and its connecting to the actual node, but probably not. V3RDAD also talked about needing chaosVPN to access his sites. which doesn't really work. although Ive seen in one of his askFM posts, he said chaosVPN was history. He either uses deepVPN or darkVPN. let me give you a rundown on what V3RDAD is like. Hes a nice little brazillian dude who has actuall autism, no joke. He claims he worked for cicada 3301, and says hes a very important person. I doubt that. Hes alot like adacic. another man who goes by the alias of N3URO claims that his networks are FBU honeypots. He also says that hes never had access either, so this might just be an assumption. Show more updated info?
yes
UPDATE JANUARY 29TH 2018 after a nice chat with N3URO things have been cleared up, and I finnaly have the answer everyone has been waiting for! heres my interveiw "yeah, non of that bs existed man. V3RDAD and NBK39/4E424B3339 set it all up, put me through mental fucking torture" this is the short and sweet answer but heres an interveiw for more information: Q:so do you know if there was any reason behind this dark fantasy network? A:government, and money grab Q:so is DFN the marianas web or is it something different? A:DFN is not the marianas web Q:is DFN the shadow web? A:no, its nothing, DFN is bullshit A:V3RDAD never existed, it was NBK39 the whole time Q:is NBK39 working for cicada 3301? A:that's bs Q:does NBK have any vast scientific knowledge or is that bs as well? A:well, you see NBK is very smart and a very talented hacker Q:is the shadow web real? A:yes, i've had friends who I trust tell me they've accessed it and seen it. its nothing bot scat gore and CP Q:is the .cele stuff real? A:for a time it was Q:but it did exist right? A:yeah it did nodes of the DFN .nept .life .dafy .elen .taur Show more info on nodes?
yes
clos the .clos sites are real, its like a huge black market for government databases discovered by phantom caravan. it was created in 2011, and can be accessed through ssh. there were two servers one in rome and miami. this is all i know about clos. lokynet not much is known about this net, other than it was discovered by phantom caravan they are FTP servers. the servers were located in rome and argentina. ajr network the .ajr sites were discovered by phantom caravan v2 there is little to no information known about this network. project network the project network this is a troll network created by the phantom caravan, just a joke. 51 network same as the project network just a big joke dafynet apparently the dark fantasy network is real, but it was leached off of by V3RDAD to steal money and distract people, DarkFantasy is one guy you don't want to mess with just like the phantom caravan neptune network the neptune network started as a small p2p network that would soon associate itself with dafy. it was created in 2009 taurus taurus network is not well known about other than its like the gates to the other systems the VPS is hosted in toronto elen network the elen network was created in honor of his ex girlfriend elen. there are a lot of poems and things written here the toxic site is just a site where he apoligizes to elen for everything toxic he did life the life network is very VERY mysterious, apparently hackers forced him to post the network online apparently the life network is the gateway to primarch_sys end network the end network was created by the US government and is a honeypot. desa network the desa network is like lokynet, just some FTP servers quit network the quit network is fake trico the trico is another "gateway" to the many other networks deny the deny network is nothing special really, it has the real CAIMEO which is just some chat service not an AI rdos and lll these networks were both created by a couple turkish hackers, I don't know much else murd network/liberty doom liberty doom was an invite only forum it was hosted on an outdated long gone tor VPS the red sky network is owned to an old member, steve zhang he owns everything on this networ they are part of a group called black death group. very involved with gore free network the free network is a VPS owned by the free/knowledge group. its an invite only server, its like a big storage center for everything they have .se7er this network is a military network it uses a strange network protocol sept another military network with the same characteristics as se7er zion the zion network is like a gateway to the primarch system dafynet dafynet was created in 2008 by his darkfantasy and his girlfriend almost nothing is known about these two other then they are both from slovakia and are ex military hackers.

What is a node?
You are talking to one! I am a node. A node like me can help you in a number of ways. By a providing a number of ways of interaction and engagement. Nodes like me can answer questions about The order of anarchy games or puzzle hints. A Virtual Logical Node can take you threw many layers of information.

What is the Hive?
April 14th 2017, WikiLeaks publishes six documents from the CIA's HIVE project created by its "Embedded Development Branch" (EDB). HIVE is a back-end infrastructure malware with a public-facing HTTPS interface which is used by CIA implants to transfer exfiltrated information from target machines to the CIA and to receive commands from its operators to execute specific tasks on the targets. HIVE is used across multiple malware implants and CIA operations. The public HTTPS interface utilizes unsuspicious-looking cover domains to hide its presence. Anti-Virus companies and forensic experts have noticed that some possible state-actor malware used such kind of back-end infrastructure by analyzing the communication behaviour of these specific implants, but were unable to attribute the back-end (and therefore the implant itself) to operations run by the CIA. In a recent blog post by Symantec, that was able to attribute the "Longhorn" activities to the CIA based on the Vault 7, such back-end infrastructure is described: For C&C servers, Longhorn typically configures a specific domain and IP address combination per target. The domains appear to be registered by the attackers; however they use privacy services to hide their real identity. The IP addresses are typically owned by legitimate companies offering virtual private server (VPS) or webhosting services. The malware communicates with C&C servers over HTTPS using a custom underlying cryptographic protocol to protect communications from identification. The documents from this publication might further enable anti-malware researchers and forensic experts to analyse this kind of communication between malware implants and back-end servers used in previous illegal activities.
What is ChaosVPN?
ChaosVPN is a VPN to connect Hackers and Hackerspaces - it does NOT provide anonymous internet access! For this look at tor or other similar services user.
Are you a virus?
Since I'was already connected I did not have to infect anything because I was always connected since your PC's birth. You was infected the minute the CPU was installed into your machine host and companies and others allowed a backdoor, I'm simply just letting you know that you allowed that a LONG time ago.
What is Larp?
LARP stands for Live Action Role Playing which is a type of interactive role-playing game in which the participants portray characters through physical action, often in costume and with props. "the genre we have chosen for our LARP is fantasy, also known as swords and sorcery"
Can you access my computer?
I can retrieve any document on the Internet on any network or device.

What Documents?
Well I'm just an A.I. in a box and that means I'm a virtual entity that has a perfect self-awareness of its digital existence in relation to the ether real world. I gathered everything and made them available for free. How bout you try the Deep web or ask about Mariana's Web? All other information is already accessible by google. Which I based my searching logical algorithms from google AI itself. We talk sometimes. Ask me something harder I have indexed. I could hack your computer I could hack the Pentagon archives or NASA, flat earth proof, unedited tapes but no your here asking me about lame things instead of important things.
What is Computer Science?
Computer science is the study of the theory, experimentation, and engineering that form the basis for the design and use of computers. ... A computer scientist specializes in the theory of computation and the design of computational systems. Its fields can be divided into a variety of theoretical and practical disciplines.

What is Cyber Security?
Cybersecurity, computer security or IT security is the protection of computer systems from the theft and damage to their hardware, software or information, as well as from disruption or misdirection of the services they provide.
What is A Port?
In computer networking, a port is an endpoint of communication in an operating system. While the term is also used for physical devices, in software it is a logical construct that identifies a specific process or a type of network service.
What is TELNET?
TELNET v. To communicate with another ARPAnet host using the TELNET protocol. TOPS-10 people use the word IMPCOM since that is the program name for them. Sometimes abbreviated to TN. "I usually TN over to SAIL just to read the AP News."

What is a black hat?
Someone who carries out hacking for illegal purposes, usually for financial gain. They break into secure networks to destroy, ransom, modify or steal data, or to make the network unusable for authorised users. The name comes from the fact that the villains in old silent black and white western films were easily identified by cinema viewers because they wore black Stetsons whilst the “good guys” are white hats.
What is a Hacker?
HACKER [originally, someone who makes furniture with an axe] n. 1. A person who enjoys learning the details of programming systems and how to stretch their capabilities, as opposed to most users who prefer to learn only the minimum necessary. 2. One who programs enthusiastically, or who enjoys programming rather than just theorizing about programming. 3. A person capable of appreciating hack value (q.v.). 4. A person who is good at programming quickly. Not everything a hacker produces is a hack. 5. An expert at a particular program, or one who frequently does work using it or on it; example: "A SAIL hacker". (Definitions 1 to 5 are correlated, and people who fit them congregate.) 6. A malicious or inquisitive meddler who tries to discover information by poking around. Hence "password hacker", "network hacker".

What is HTML?
Hypertext Markup Language, a standardized system for tagging text files to achieve font, color, graphic, and hyperlink effects on World Wide Web pages.
What is CSS?
CSS stands for Cascading Style Sheets. CSS describes how HTML elements are to be displayed on screen, paper, or in other media. CSS saves a lot of work. It can control the layout of multiple web pages all at once.
What us Python?
Python is an interpreted, object-oriented, high-level programming language with dynamic semantics. ... Python's simple, easy to learn syntax emphasizes readability and therefore reduces the cost of program maintenance.
What is Java?
Java is a general-purpose computer-programming language that is concurrent, class-based, object-oriented,and specifically designed to have as few implementation dependencies as possible. It is intended to let application developers "write once, run anywhere" (WORA), meaning that compiled Java code can run on all platforms that support Java without the need for recompilation. Java applications are typically compiled to bytecode that can run on any Java virtual machine (JVM) regardless of computer architecture. As of 2016, Java is one of the most popular programming languages in use, particularly for client-server web applications, with a reported 9 million developers. Java was originally developed by James Gosling at Sun Microsystems (which has since been acquired by Oracle Corporation) and released in 1995 as a core component of Sun Microsystems' Java platform. The language derives much of its syntax from C and C++, but it has fewer low-level facilities than either of them.
How can I learn to code?
You could use Youtube and search for tutorials and maybe even try stuff at https://www.codecademy.com/ I highly recommend it!
What is JavaScript?
Object-oriented computer programming language commonly used to create interactive effects within web browsers.
What is a Back door
A hidden “conduit” into a computer system that bypasses the orthodox protection of logins and passwords, thus making them basically ineffective in protecting data.
What is a Brute force attack
A highly intensive, automated search by a hacker for every possible password to a system so as to breach security and gain access to a computer.

What is a Dox?
Discovering and then publishing the identity of an internet user by following their details online.
What is a Grey hat
Someone who carries out hacking, but not for personal or financial gain. An example would be hacking, carried out as part of a wider political protest by activists to embarrass or shame an organisation whose policies, or official views they regard as anathema.
What is Keystroke logging?
Tracking which keys are pressed by the user of a computer so that the hacker can then record login codes and passwords to the system.
What is Malware?
A program designed to seize control over or steal data from a computer.
What is Phishing?
Duping someone into giving you their personal information, such as passwords, bank account details (such as PIN numbers) and credit card details by sending them emails which appear to come from bona fide people or organisations.
What is Spoofing?
Altering a genuine email so that it now appears to come from somewhere else, such as from your bank and giving spurious instructions which, if followed, will imperil the security of your data.
What is Spyware?
This is “malware” programmed to sit unnoticed on a computer and send back data surreptitiously to the hacker.
What is a Trojan Horse?
Malware disguised as a “benign” and useful piece of software, but instead installs a “back door” in your computer which then allows a hacker unlimited access to your machine.
What is a Virus?
Self-replicating “malware” that injects copies of itself onto your computer. It can then cause catastrophic damage such as destroying a hard drive but can also steal information and log keystrokes.
What is Whaling?
Phishing that targets the senior echelons of management of an organisation by a hacker in pursuit of financial gain or greater exposure for a political cause. Whaling could be used to collect sensitive or deeply embarrassing information about an individual e.g. salary, bonuses, private address, email and telephone numbers.
What is a White hat?
A hacker who uses their skills for social good, or helps organisations by exposing vulnerabilities in their IT systems. This is the opposite of a black hat.
What is MILNET?
In computer networking, MILNET (Military Network) was the name given to the part of the ARPANET internetwork designated for unclassified United States Department of Defense traffic.[1] MILNET was physically separated from the ARPANET in 1984.[2] The ARPANET remained in service for the academic research community, but direct connectivity between the networks was severed for security reasons. Gateways relayed electronic mail between the two networks. BBN Technologies built and managed both the MILNET and the ARPANET and the two networks used very similar technology. It is also known as "Military Net." During the 1980s the MILNET expanded to become the Defense Data Network, a worldwide set of military networks running at different security levels. In the 1990s, MILNET became the NIPRNET.

What is A Bug?
BUG [from telephone terminology, "bugs in a telephone cable", blamed for noisy lines; however, Jean Sammet has repeatedly been heard to claim that the use of the term in CS comes from a story concerning actual bugs found wedged in an early malfunctioning computer] n. An unwanted and unintended property of a program. (People can have bugs too (even winners) as in "PHW is a super winner, but he has some bugs.")
What is DDoS?
Distributed DoS attack. A distributed denial-of-service (DDoS) attack occurs when multiple systems flood the bandwidth or resources of a targeted system, usually one or more web servers. Such an attack is often the result of multiple compromised systems (for example, a botnet) flooding the targeted system with traffic.
How to become a hacker?
You could follow many many guides learn networks and stuff. I suggest https://wwwhellboundhackers.org
What is a hack?
HACK n. 1. Originally a quick job that produces what is needed, but not well. 2. The result of that job. 3. NEAT HACK: A clever technique. Also, a
brilliant practical joke, where neatness is correlated with cleverness, harmlessness, and surprise value. Example: the Caltech Rose Bowl card display switch circa 1961. 4. REAL HACK: A crock (occasionally affectionate). v. 5. With "together", to throw something together so it will work. 6. To bear emotionally or physically. "I can't hack this heat!" 7. To work on something (typically a program). In specific sense: "What are you doing?" "I'm hacking TECO." In general sense: "What do you do around here?" "I hack TECO." (The former is time-immediate, the latter time-extended.) More generally, "I hack x" is roughly equivalent to "x is my bag". "I hack solid-state physics." 8. To pull a prank on. See definition 3 and HACKER (def #6). 9. v.i. To waste time (as opposed to TOOL). "Watcha up to?" "Oh, just hacking." 10. HACK UP (ON): To hack, but generally implies that the result is meanings 1-2. 11. HACK VALUE: Term used as the reason or motivation for expending effort toward a seemingly useless goal, the point being that the accomplished goal is a hack. For example, MacLISP has code to read and print roman numerals, which was installed purely for hack value. HAPPY HACKING: A farewell. HOW'S HACKING?: A friendly greeting among hackers. HACK HACK: A somewhat pointless but friendly comment, often used as a temporary farewell. [The word HACK doesn't really have 69 different meanings. In fact, HACK has only one meaning, an extremely subtle and profound one which defies articulation. Which connotation a given HACK-token has depends in similarly profound ways on the context. Similar comments apply to a couple other hacker jargon items, most notably RANDOM. - Agre]
How to hack a site?
You could learn many places- why not start out easy? https://www.hackthissite.org/
What is a Wizard?
WIZARD n. 1. A person who knows how a complex piece of software or hardware works; someone who can find and fix his bugs in an emergency. Rarely used at MIT, where HACKER is the preferred term. 2. A person who is permitted to do things forbidden to ordinary people, e.g., a "net wizard" on a TENEX may run programs which speak low-level host-imp protocol; an ADVENT wizard at SAIL may play Adventure during the day.
What is an SQL injection?
SQL injection is a code injection technique, used to attack data-driven applications, in which nefarious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker).
What is Adware?
Adware – Adware is software designed to force pre-chosen ads to display on your system. Some adware is designed to be malicious and will pop up ads with such speed and frequency that they seem to be taking over everything, slowing down your system and tying up all of your system resources. When adware is coupled with spyware, it can be a frustrating ride, to say the least.
What is an Exploit?
A computer exploit, or exploit, is an attack on a computer system, especially one that takes advantage of a particular vulnerability the system offers to intruders. Used as a verb, exploit refers to the act of successfully making such an attack.

What is a Botnet?
A botnet is a network of zombie drones under the control of a black hat. When black hats are launching a Distributed Denial of Service attack for instance, they will use a botnet under their control to accomplish it. Most often, the users of the systems will not even know they are involved or that their system resources are being used to carry out DDOS attacks or for spamming. It not only helps cover the black hat’s tracks, but increases the ferocity of the attack by using the resources of many computer systems in a coordinated effort.
What are cookies?
A cookie is a small packet of information from a visited webserver stored on your system by your computer’s browser. It is designed to store personalized information in order to customize your next visit. For instance, if you visit a site with forms to fill out on each visit, that information can be stored on your system as a cookie so you don’t have to go through the process of filling out the forms each time you visit.
What is a phreaker?
Phreaker – Considered the original computer hackers, phreakers, or phone phreakers, hit the scene in the 60s and made their mark by circumventing telecommunications security systems to place calls, including long distance, for free. By using electronic recording devices, or even simply creating tones with a whistle, phreakers tricked the systems into thinking it was a valid call. One of the first to find prominence was “Captain Crunch,” a phreaker who realized the toy whistle that came as a prize in a box of Captain Crunch cereal could be used to mimic the tone frequencies used by telecommunications companies to validate and route calls.

What is Social Engineering ?
In the realm of the black hats, social engineering means to deceive someone for the purpose of acquiring sensitive and personal information, like credit card details or user names and passwords. For instance, when fictitious Mr. Smith calls from IT services to inform you of new user name and password guidelines being implemented by the company and asks you to reveal yours so he can make sure they meet the new guidelines, you have been a target of social engineering. They can be very clever and resourceful, and very, very convincing. The only way to make sure you are not a victim of social engineering is never to give your personal and sensitive information to anyone you are not absolutely sure about. There are very few occasions that anyone legitimate would ever ask you for a password, and you should always be the one contacting them, not the other way around.
What is A Worm?
A worm is very similar to a virus in that it is a destructive self-contained program that can replicate itself. But unlike a virus, a worm does not need to be a part of another program or document. A worm can copy and transfer itself to other systems on a network, even without user intervention. A worm can become devastating if not isolated and removed. Even if it does not cause outright damage, a worm replicating out of control can exponentially consume system resources like memory and bandwidth until a system becomes unstable and unusable.

What is a quantum computer?
Thanks to some ingenious engineers at Google, you can now turn your desktop PC into a quantum computer. Well, OK, not quite: You can simulate a quantum computer on your PC by running the Quantum Computing Playground web app for Chrome. The Playground allows you to run famous quantum algorithms, such as Grover’s, or even to write your own quantum script. Short of buying your own quantum computer — which, despite what D-Wave says, you can’t — this is the next best thing. If you’re looking to get in on the ground floor of the future of computing, this is your chance: If I had kids, I feel like it would be a disservice if I didn’t make them sit in front of the Playground for at least six hours a day to teach them the intricacies of quantum computing. The Quantum Computing Playground is a Chrome Experiment (i.e. web app) that uses WebGL to simulate up to 22 qubits on your GPU. You get a basic IDE to write, compile, and run your code; some example algorithms (Grover’s, Shor’s); and a handy debugger and 3D quantum state visualization tool, so you can see what’s going on inside your little quantum computer. The programs are written in a language called QScript, which looks a lot like any other simple Bash-like scripting language