Security 101: Physical Security - Disk Encryption I
In the previous part we secured our bootloader against the Single User Mode hole, but we discovered that if we boot up a CD/DVD and try the recovery method, the data is still vulnerable. The best way to combat this, is disk encryption!
A sample of encrypted data is this:
Original: I love steemit
Encrypted with blowfish: S0eOZNjpHcJESHOiwuCJSg====
Previous parts:
1. Introduction
2. General Principles and Guidelines
3. Physical Security: Intro
4. Physical Security: Single User Mode
5. Physical Security: Securing your Bootloader
What is data encryption
When encrypting your data, everything gets unusable without a key or a password. Your operating system can't read the files too. Most linux distros offer encryption with a password that offer access to your OS when you login. The key remains in memory while your encrypted disk or volume or folder is mounted. If you are going to use a password, make sure you use a long one, as complex as you can, as it may be the weak link that exposes your data to anyone.
Disk encryption should be as transparent as possible for the user. For example, while you are logged in, the data should be decrypted and encrypted on the fly using a virtual block device, without you having constantly to type your password.
The standard is LUKS - Linux Unified Key Setup. It is used across most linux distros, and is a front-end for dm-crypt.
dm-crypt does what I described above. It sets up a virtual block device that provides unencrypted access to all your data when you are logged in (= supplied your encryption/decryption key), and encrypts all the data you try to store on the fly, while writing them to your disk.
LUKS supports multiple passphrases, that unlock a master key for data decryption. It is also considered portable, as the information is stored in the partition header and can be used across various linux distros.
It is also working great for removable devices, such as USB HDDs, flash drives etc.
Encrypting during linux install
Most linux distros offer you the ability to encrypt your disk while installing. It is easy to use this, as you don't have to do any configuration whatsoever, which is also a disadvantage, as you'll have to rely on the default settings supplied by each linux distro developers.
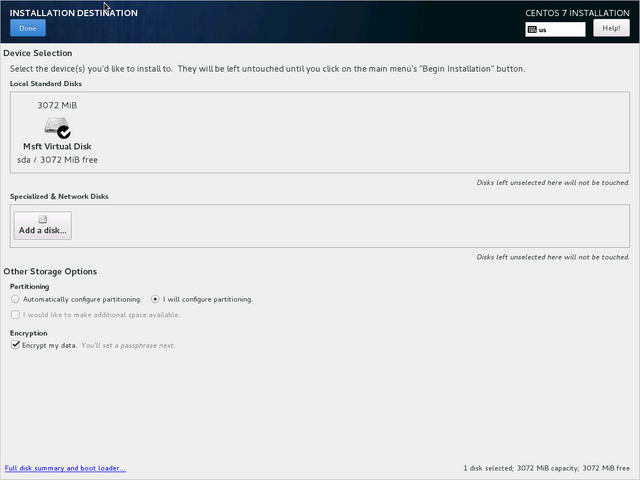
On CentOS, you have to select "Encrypt my Data" when choosing the target drive for installation:
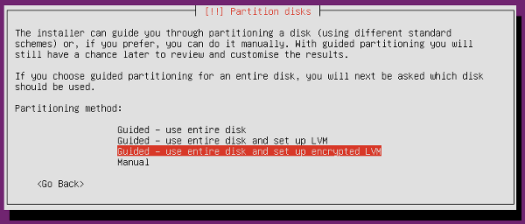
On Ubuntu, you have to select "Guided - use entire disk and set up encrypted LVM" when the setup asks you to partition the disk:
You'll have to type your passphrase every time you start your computer, as it wouldn't be able to mount your data otherwise.
Encrypting a new disk
You can use this method to encrypt a partition or device (from USB Flash drives to remotely mounted cloud hosted virtual partitions) that is available in your system. However, if you have data on this device, this encryption procedure will remove all data. I will be covering the encryption of a device with data in the next article.
The first thing we've got to do, is to install cryptsetup: sudo apt-get install cryptsetup
Then, with fdisk -l you've got to locate the disk or partition you want to encrypt. For this example, I'll be using /dev/sdb as the device I want to encrypt.
Unmount the device: sudo umount /dev/sdb
We are now, going to fill the drive with nonsense data to make sure any sensitive data available in the disk, won't be recovered (at least, not easily). You can use any utility you want/like/prefer for this. I'm going with good ol' dd: sudo dd if=/dev/urandom of=/dev/sdb
Depending on your disk size and the data available on the disk, this may take several minutes (and even hours) to complete.
After dd finishes, we are going to initialise the encryption process. Under no circumstance should you interrupt this process.
sudo cryptsetup luksFormat /dev/sdb myencdevice
You will get asked if you are sure you want to proceed, and you have to reply with YES. Also you'll be asked for a passphrase twice. This process is almost instantaneous. Now, you just have to open the disk with cryptsetup:
sudo cryptsetup luksOpen /dev/sdb encvolume1
You can change "encvolume1" to anything you want. This will be used as the device name on /dev/mapper/.
We are ready to start using the device. You can start by making a filesystem:
sudo mkfs -t ext4 /dev/mapper/encvolume1
And then, mount it at the folder you want to: sudo mount /dev/mapper/encvolume1 /path/to/mount/fs.
If at any point you want to close the device, you'll have to do:
sudo umount /path/to/mount/fs
sudo cryptsetup luksClose encvolume1
Great.. But now, how can I use this everytime I boot my system? I don't want to be typing the "cryptsetup luksOpen" command on each and every boot.
You just have to mount it!
Open up /etc/fstab to add the new filesystem we created:
sudo nano /etc/fstab
At the end of the file, you just have to type this: /dev/mapper/encvolume1 /path/to/mount/fs ext4 defaults 0 0
Now, we also have to add an entry to "/etc/crypttab". This will ask you for your encryption password at boot time, in order to make the disk available for you:
So, open up the file sudo nano /etc/crypttab and write this inside (make sure to edit it so it applies to your own device name etc):
encvolume1 /dev/sdb none luks
If you are going to use encrypted removable devices (such as USB Flash drives), then a better option is to use UUID which is also supported by cryptsetup. Now, go ahead and reboot the system. You'll get asked for the encrypted disk's password before you'll be able to boot your system.
In the next part we're going to examine how can we use encryption on systems where we don't have block level access to devices, as well as how can we encrypt devices without losing our data. Click here to read it!
Craving for more? Until the next part is available, have a look at my Server 101 series:
- Intro and getting into your server - Single Article
- Basic Server Security - 3 Parts
- Setting up a Web Server - 4 Parts
- Managing Your Server - 4 Parts
- caddy - Lightweight Web Server - 1 Part
- Emailify your server! - 6 Parts
- Setting up a Password-Protected proxy server with Squid - 1 Part
- OpenVPN in less than 2 minutes
- Piwik - Your personal Google Analytics alternative
- Email notifications for SSH Logins
- Keeping your server up to date
Congratulations @dimitrisp! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOP