Is your cloud computing platform safe from Flip Feng Shui?
Flip Fend Shui - A massive threat to the cloud!
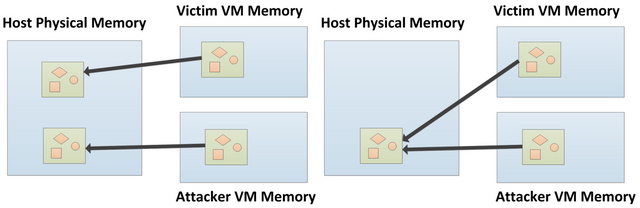
What is Flip Fend Shui?
- Flip Fend Shui (FFS) is a new exploitation vector that allows an attacker virtual machine (VM) to flip a bit in a memory page of a victim VM that runs on the same host as the attacker VM.
- The attack allows an attacker to completely compromise co-hosted cloud VMs with relatively little effort.
- Existing cryptographic software is wholly unequipped to counter it, given that 'bit flipping is not part of their threat model. This includes Digital Signature Algorithm, Diffie-Hellman, Elliptic Curve Cryptography, and Elliptic Curve Diffie-Hellman.
- All Virtual Machine vendors are vulnerable (Oracle, Redhat, Xen, VMware).
- More than 85% of DDR3 modules are vulnerable.
- DDR4 is also affected.
Examples of attacks
Compromising OpenSSH: flips a bit in the page cache of a victim VM storing the authorized_keys file of OpenSSH. authorized_keys files stores the (often) RSA public key. A user with the RSA private key associated with that public can then login to the SSH server.
Compromising apt-get: chain two FFS attacks to trick apt to install a tampered software packaged from a malicious repository without any suspicious warning.
Currently have virtual machines in the cloud?
You need to immediately contact your cloud computing platform to enquire if your virtual machines are secure from this exploit vector! If they are not, you should seriously consider migrating your virtual machines to a more secure platform - an attacker could potentially spin up a free trial VM to attack your web services.
I personally contacted DigitalOcean (Referral code), and they publicly responded on Twitter stating that they are not vulnerable to this exploit vector!
Reply in the comments if you get responses from your cloud computing platform of choice regarding this exploit!
Related links
Official 'Flip Fend Shui' website.
Arstechnica UK article on Flip Fend Shui.
Arstechnica UK article on DDR4 rowhammer vulnerability
'TheRegister' article on Flip Feng Shui.
/r/netsec thread on 'project zero' - a similar rowhammer bug.
Related rowhammer exploit in javascript!
Upcoming BlackHat event on Flip Feng Shui
Wikipedia article on Rowhammer
Theo de Raadt nailed the core of the issue nearly a decade ago:
And people called him nuts.
I have always recommended to my customers not to run on public clouds - this was the craze for years, appears to finally be dying down a little bit again.
If you control the hypervisor, it is a little bit better, but really .. why not do away with it completely.
All other things being equal, less complexity is a better prospect.
Do you think this kind of attack has long been in the hands of state sponsored hackers? Or do you think that the current security threat level that Flip Feng Shui has elevated us to has only now become a reality?
They have known.
For years.
No reply from Vultr nor Linnode.
I will push on Linode on their support system regarding this issue. Also posted to them on twitter earlier today.
Apparently, an user within the Gridcoin community contacted Linnode & they stated that they were not vulnerable but failed to back up the claim with any further details.
Disclaimer: I am just a bot trying to be helpful.
Azure
Twitter response:
https://twitter.com/AzureSupport/status/771430272831066112
They recommended to read this page: https://www.microsoft.com/en-us/TrustCenter/Security/AzureSecurity
Unclear whether or not they're secure, certainly not as direct a response compared to DigitalOcean.
Disclaimer: I am just a bot trying to be helpful.