The Strange Case of Reality Winner

Reality Winner was only 25 years old when she was arrested for removing classified material from an NSA agency and mailing it to a news outlet. According to official reports, the document she obtained and leaked outlined a spear phishing attack launched by the GRU (the Main Directorate of the General Staff of the Armed Forces of the Russian Federation) against the US Government. It was alleged that this was the attack in which Russia obtained the Podesta emails released in 2016. If such an attack by a foreign power did indeed occur, why then is Reality Winner locked away in prison instead of lauded as a hero?
Ms. Winner served for six years in the U.S. Air Force as a Farsi and Pashto linguist, specializing in communications intercept operations and analysis on behalf of the NSA. She left the Air Force in 2016 and in 2017 began work as a civilian contractor at the Georgia Cryptologic Center, an NSA facility in Augusta, GA. that specializes in analyzing communications intercepts from Europe, the Middle East and North Africa. Winner had been very active on social media and was critical of U.S. foreign policy around the world, a point of view that was used against her as "anti-American rhetoric". She was also very critical of Donald Trump, calling him a "fascist", and took the initial allegations of Russian interference in the 2016 election seriously.
In May 2017 Winner accessed a top-secret NSA document and made the decision to mail a copy of that document to The Intercept. Her responsibility for the leak was uncovered and she was arrested.
A cursory reading of the document would seem to support the allegations of a Russian hack through a spear phishing campaign but a closer look seems to suggest not only no smoking gun but also no gun at all.
Scott Ritter, a former United Nations weapons inspector who blew the whistle on the Bush Administration's lies about WMDs in Iraq, offered an in-depth analysis of this document which I will quote below. The article this is excerpted from is sourced at the end of this piece. Ritter writes:
The opening paragraph of the leaked NSA document states:
Russian General Staff Main Intelligence Directorate actors … executed cyber espionage operations against a named U.S. company in August 2016, evidently to obtain information on elections-related software and hardware solutions. … The actors likely used data obtained from that operation to … launch a voter registration-themed spear-phishing campaign targeting U.S. local government organizations.
Two explanatory footnotes, heavily redacted, likewise attribute the reported actions of “Cyber threat actors” to the GRU and other redacted organizations affiliated with it. There is no doubt that, from the perspective of NSA analysts who prepared the document, the GRU was the driving force behind the cyberactivities being reported.
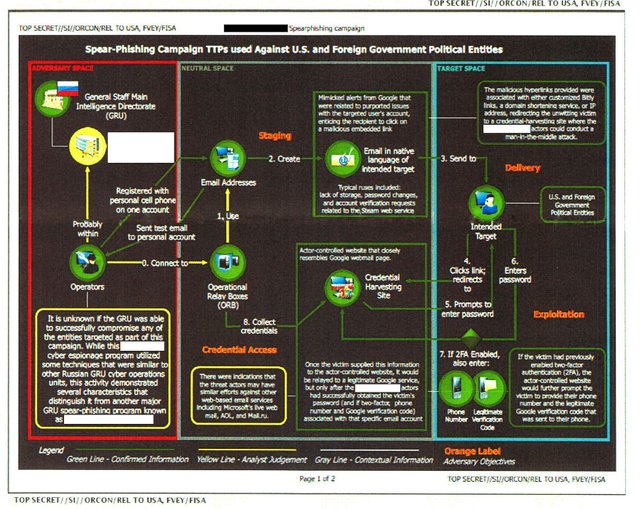
The strength of this assertion, however, collapses when one examines the colored chart that accompanied the text of the report detailing the “Spear-Phishing Campaign TTPs used Against U.S. and Foreign Government Entities” (TTPs are tactics, techniques and procedures). While the document, as released by The Intercept, shows only the first page of what is described as a two-page chart, the material it contains is clear and concise regarding what it is illustrating. The activity flow chart, which details the sequencing and relationships involved in the execution of the spear-phishing campaign, breaks the sourcing of the information into three categories: green, yellow and gray.
Green stands for “confirmed information.” Most of the technical details reported on fall into this category.
Yellow represents what is described as an “analyst judgment,” which is a far cry from the assertion of fact indicated by the green designation. The color yellow is used five times. Three signify the flow of activity involved in the TPPs. Two, however, deal with the critical issue of attribution. While the report indicates that the “operators” (cyberactors) are confirmed quantities, the linkage between them and their immediate supervising command authority is not confirmed, but rather derived from an analytical judgment.
This is a critical fact that has been overlooked in the media hype surrounding the NSA document. It is also significant that this command authority is not the GRU headquarters itself, but rather a different entity, whose identity has been redacted throughout the document by The Intercept at the request of the NSA. The NSA document provides some clues as to the affiliation of the entity in question, noting that it is similar to “other Russian GRU Cyber Operations Units.”
There is little doubt that the NSA has a specific unit in mind, and that its identity is so sensitive that the agency requested The Intercept to redact it throughout the document. It is also clear, however, that the NSA has not established a confirmed link between this secret cyberoperations unit and the “operators” behind the reported cyberoperations targeting the 2016 election. Rather, the link is purely speculative, a product of analytical judgment, not hard fact.
The third and final color used in the NSA chart is gray, which stands for “contextual information.” This color is used three times in the chart. First, it links the confirmed activity to other cyberattacks on “U.S. and Foreign Government Political Entities.” What is important in this revelation is that the NSA is declaring that it has no proof that the events documented in the leaked document have any connection with, for instance, the cyberattack on the Democratic National Committee (DNC), the German Parliament or any other entity. An analytical assumption is being made that is provided for “context.” But the document does not sustain this assumption with any fact-based data.
The second use of “contextual information” deals with a specific type of operation known as “credential harvesting,” in which passwords, phone numbers and verification codes are collected using what is called a “man in the middle” attack—basically diverting the signal to a host server, where the harvesting is done, before sending it on to its intended destination. The chart indicates that the NSA can confirm credential harvesting at an “actor controlled” server based in what is called “neutral space”—neither Russia (“adversary space”) nor the United States (“target space”)—most likely a server on European soil. It hints at a capability to harvest credentials in the “target space,” but the link is gray—for context only. There is no fact-based information that allows such an assertion to be made.
The third and final use of “contextual information” deals with the attribution to the GRU itself. The chart links the GRU to the redacted cyberentity using a gray line (the redacted entity had, in turn, been linked to the “confirmed” operators in yellow). The significance of this attribution is enormous—the NSA is acknowledging that any attribution of the GRU to the activities being reported on is purely “contextual” in nature. It has no evidence of this attribution whatsoever.
Nothing in the document’s confirmed information links it to the GRU. The GRU attribution is presented for contextual purposes only. It is an inferred command relationship to a redacted cyberoperations management capability that is linked to the confirmed cyberoperators only through analysis (i.e., best guess), not fact.
The NSA document, both in its title and text, is therefore misleading in the extreme. There is simply no fact-based information provided in the report that confirms that the events reported on were being organized and managed by the Russian GRU, despite the document’s assertions otherwise.
This lack of confirmation of any fact-based linkage between the GRU and the cyberattacks on the 2016 election in the NSA document is striking in another regard. The NSA has always been assumed to be the agency that possessed “smoking gun” evidence when it came to Russian attribution in the cyberattacks on the American electoral process.
William Binney, a former intelligence official with the NSA who resigned when he discovered the agency was using his own surveillance program designed for data-monitoring terrorist activities to instead spy on US citizens, has since maintained that the NSA has zero evidence and zero confidence that there was ever a Russian hack. With its spying practices, everything that is transmitted back and forth across the Internet is recorded and filed by the agency. In 2011 a hack from China was pinpointed within seconds to the exact location in the exact city where the hack originated but no such trail exists for the alleged Russian hack.
Judging by a proper analysis of the document released by Reality Winner, it would seem a standard spear phishing incident took place and the NSA speculated the GRU was the culprit or, more likely, simply used them as an example to demonstrate how such an attack works.
The question is, what would be the purpose in taking and releasing such an underwhelming document one year after the Russia hacking hysteria had already been dominating the headlines? I have a hard time believing someone of Ms. Winner's credentials and experience would be unable to correctly interpret the document she released. So did she really believe the document showed a Russian hack or did she believe it proved no such hack took place? Which do you think is the more likely explanation for why she is locked away in federal prison with no contact with the outside world?
Source: "Leaked NSA Report is Short on Facts, Proves Little in Russiagate Case" - Scott Ritter, truthdig.com June 8, 2017.
https://www.truthdig.com/articles/leaked-nsa-report-is-short-on-facts-proves-little-in-russiagate-case/
Very informative article. Thanks!!
Other sources have shown the rate at which the data was copied from the DNC server exceeded what could have been accomplished remotely. It was done with a USB. Not a hack.
Brennan and friends made up the Russian hack out of whole cloth. Not sure what role Reality played, but generally the folks leaking stuff to the media were not whistleblowers, they were laying down a smoke screen.
Glad you enjoyed it!
In fact, it was William Binney and his team of former intelligence professionals who revealed that the data was leaked, not hacked. They've done excellent work in this case.
It's very possible Reality was a part of that smokescreen. It's hard to say. Perhaps time will tell.