SmartEdge: Simple NAPT configuration
Rules – how to apply NAT
- NAT policy should be apply to incoming traffic
- IP outgoing interface cannot be used in the NAT pool
- NAT pool must be on separate subnet (not part of interface subnet)
- In dynamic nat, NAT type of route is automatically created (no need extra route configuration)
- In static nat, extra route must by added (ip route 6.6.6.0/24 1.1.2.2) to point nat interface for coming back packet
- If we do “clear ip route * ” dynamic nat is stop working and nat policy must be recreated on interface level (SEOS 6.2)
- On “multibind” interface, combination with static and dynamic nat is not working (only dynamic is operational), pool should be configured as multibind
ip nat pool my-pool napt multibind
- NAT policy could be applied on the subscriber level
subscriber default
ip address pool
nat policy my-nat
Dynamic NAT
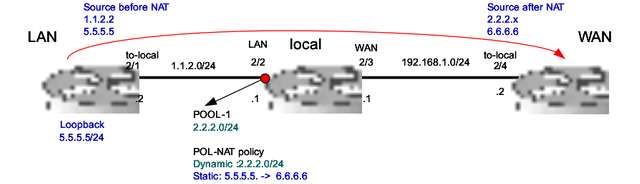
The ping from “LAN” context with any source address will be NAT-ed in “local” context in LAN interface. Example source address 1.1.2.2 will be replace to POOL-1 address 2.2.2.0/24 (dynamic mapping) and routed to context WAN.
Static NAT:
The ping from “LAN” context will be NAT-ed in “local” context in LAN interface. Source address 5.5.5.5 will be replace to 6.6.6.6 (static mapping) address and routed to context WAN.
Example configuration:
!
context local
!
ip nat pool POOL-1 napt
address 2.2.2.0/24
!
nat policy POL-NAT
! Default class
pool POOL-1 local
! Static rules
ip static in source 5.5.5.5 6.6.6.6
!
interface LAN
ip address 1.1.2.1/24
ip nat POL-NAT acl-counters
!
interface WAN
ip address 192.168.1.1/24
!
ip route 0.0.0.0/0 192.168.1.2
ip route 5.5.5.0/24 1.1.2.2
ip route 6.6.6.0/24 1.1.2.2
ip route 159.107.0.0/16 159.107.90.1
!
context WAN
!
interface to-local
ip address 192.168.1.2/24
no logging console
!
ip route 1.1.2.0/24 192.168.1.1
ip route 1.1.3.0/24 192.168.1.1
ip route 2.2.2.0/24 192.168.1.1
ip route 6.6.6.0/24 192.168.1.1
!
context LAN
!
interface Static loopback
ip address 5.5.5.5/24
!
interface to-local
ip address 1.1.2.2/24
no logging console
!
ip route 0.0.0.0/0 1.1.2.1
!
! ** End Context **
!
card carrier 2
mic 1 fe-12-port
!
port ethernet 2/1
no shutdown
medium-type copper
bind interface to-local LAN
!
port ethernet 2/2
no shutdown
medium-type copper
bind interface LAN local
!
port ethernet 2/3
no shutdown
bind interface WAN local
!
port ethernet 2/4
no shutdown
bind interface to-local WAN
!
end
Checking nat translation:
[LAN]Redback# ping 192.168.1.2
PING 192.168.1.2 (192.168.1.2): source 1.1.2.2, 36 data bytes,
timeout is 1 second
!!!!!
[LAN]Redback# ping 192.168.1.2 source 5.5.5.5
PING 192.168.1.2 (192.168.1.2): source 5.5.5.5, 36 data bytes,
timeout is 1 second
!!!!!
[local]Redback# show nat policy POL-NAT detail
Policy name : POL-NAT
Policy grid : 0x1
Number of rules : 1
Slot mask : 0xc
Number of binds : 1
Circuit : 2/2
Reference counters (in circuits * classes):
Slot 2
1
Static NAT Rules:
In/Out Protocol Src-Addr Port NAT-Src-Addr Port NAT-Ctx-Id
in ip 5.5.5.5 0 6.6.6.6 0 0x40080001
Class-Name Action/ Pool-Grid/ Dest-IP-Addr/ Timeout(sec) Admit-Ctrl
P2MP Context-Id Context-Id
default na[p]t 0x1 tcp 86400
Off 0x40080001 udp 120
finrst 240
icmp 60
syn 128
basic 3600
** Note: This is not official command and should be use with extra attention.**
The syntax could be changed in new release:
Checking dynamic translations
[local]Redback# show card 2 nat ?
circuit Display circuit nat information
counters Display NAT counters (without drop counters)
drop-counters Display NAT drop counters
log NAT Message Log
policy Display policy information
pool Display pool information
translation Display translation information
[local]Redback# show context
Context Name Context ID VPN-RD Description
------------------------------------------------------------------------------
local 0x40080001
[local]Redback# show card 2 nat translation context 0x40080001 source any
Slot 2 Ingress:
Type IP From IP To Ports Flag Pointer Ctx Flag
Flag: D-Dynamic, R-remote, Z-dmz, A-admission, I-ignore translation,
d-dest NAT, U - p2mp UDP
NAPT 1.1.2.2 2.2.2.0 1990/0009 0x0014 0x50024440 1/1 D
NAPT 1.1.2.2 2.2.2.0 1991/0010 0x0014 0x500244a0 1/1 D
NAPT 1.1.2.2 2.2.2.0 1989/0008 0x0014 0x500243e0 1/1 D
Checking static translation
[local]Redback# show card 2 nat circuit 2/2:1023:63/1/1/7 detail
Circuit 2/2:1023:63/1/1/7 ingress
Feature block pointer: 0x4ea8b4e0
Policy: grid=1 version=1 pointer=0xf0536ae0
Number src rules: 1 ptr 0xf05877c0
Number dst rules: 0 ptr 0x0
Number napt rules: 0 ptr 0x0
Out nat ptr 0xd053c2c0 napt ptr 0xf053eac0
class 0 ptr 0x4eaab500
Rule table:
Type IP From IP To Ports Csum Idx Ctx Vrs
src nat 5.5.5.5 6.6.6.6 0000/0000 0xfdfd 65 1 1
Circuit 2/2:1023:63/1/1/7 egress
Feature block pointer: 0x4ae2c520
Policy: grid=1 version=1 pointer=0xd00eb240
Number src rules: 0 ptr 0x0
Number dst rules: 1 ptr 0xd09cf0e0
Number napt rules: 0 ptr 0x0
Rule table:
Type IP From IP To Ports Csum Idx Ctx Vrs
dst nat 6.6.6.6 5.5.5.5 0000/0000 0x0202 129 1 1
Checking translation by using “access-list”
!
ip access-list dyn
seq 10 permit ip 2.2.2.0 0.0.0.255 any
seq 15 permit ip host 6.6.6.6 any
seq 20 permit ip any any
!
!
interface to-local
ip address 192.168.1.2/24
ip access-group dyn in count log
no logging console
!
[WAN]Redback# clear access-group ip-filter interface to-local in all
[WAN]Redback# show access-group ip-filter interface to-local in counters
Circuit 2/4, slot 2, IPv4 access-list dyn, in, 3 rules
Hit Count: 0 No Match (Default)
Hit Count: 0 seq 10 permit ip 2.2.2.0 0.0.0.255 any
Hit Count: 0 seq 15 permit ip host 6.6.6.6 any
Hit Count: 0 seq 20 permit ip any any
[LAN]Redback# ping 192.168.1.2 source 5.5.5.5
PING 192.168.1.2 (192.168.1.2): source 5.5.5.5, 36 data bytes,
timeout is 1 second
!!!!!
[LAN]Redback# ping 192.168.1.2
PING 192.168.1.2 (192.168.1.2): source 1.1.2.2, 36 data bytes,
timeout is 1 second
!!!!!
[WAN]Redback# show access-group ip-filter interface to-local in counters
Circuit 2/4, slot 2, IPv4 access-list dyn, in, 3 rules
Hit Count: 0 No Match (Default)
Hit Count: 5 seq 10 permit ip 2.2.2.0 0.0.0.255 any
Hit Count: 5 seq 15 permit ip host 6.6.6.6 any
Hit Count: 0 seq 20 permit ip any any